Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 09 março 2025

Describing activities of a crime group attacking Ukraine.

You could be hacked and not know it - Storcom, Lombard, Illinois, United States of America

A WINDOW INTO RUSSIAN SPEAKING CYBERCRIME by Tim Bobak
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore

Initial access broker repurposing techniques in targeted attacks against Ukraine

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

US7236486B2 - Integrated customer web station for web based call management - Google Patents
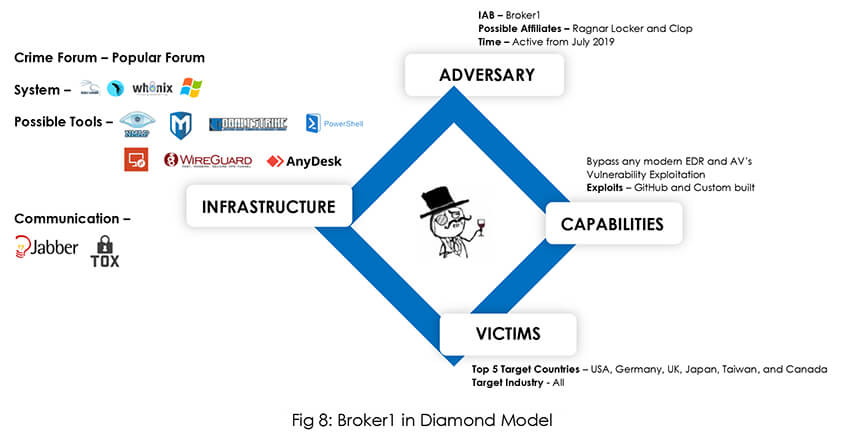
Inside the World of Initial Access Broker (IAB): Insights and Trends - CYFIRMA

Initial access broker repurposing techniques in targeted attacks against Ukraine

Initial access broker repurposing techniques in targeted attacks against Ukraine

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

The Role AI Can Play in Pharmaceutical Discovery - Techopedia

Security in product lifecycle of IoT devices: A survey - ScienceDirect
Recomendado para você
-
 Analysis Group Announces Senior-Level Promotions and Lateral Hires09 março 2025
Analysis Group Announces Senior-Level Promotions and Lateral Hires09 março 2025 -
 Analysis Group Office Photos09 março 2025
Analysis Group Office Photos09 março 2025 -
 Menlo Park - Analysis Group09 março 2025
Menlo Park - Analysis Group09 março 2025 -
 Analysis Group New York09 março 2025
Analysis Group New York09 março 2025 -
 Careers - Analysis Group09 março 2025
Careers - Analysis Group09 março 2025 -
 Dov Rothman - Analysis Group09 março 2025
Dov Rothman - Analysis Group09 março 2025 -
 Not All Evidence is Equal - Threat Analysis Group09 março 2025
Not All Evidence is Equal - Threat Analysis Group09 março 2025 -
 IAG Strategic Imaging for Accelerated Drug Development09 março 2025
IAG Strategic Imaging for Accelerated Drug Development09 março 2025 -
 Analysis Team – Analysis, Reporting & Planning Solutions09 março 2025
Analysis Team – Analysis, Reporting & Planning Solutions09 março 2025 -
 Group Analysis: Sage Journals09 março 2025
Group Analysis: Sage Journals09 março 2025
você pode gostar
-
 Super Dragon Ball Heroes Episódio 44 Completo JIREN SE IMPRESSIONA COM PODER DE BARDOCK LEGENDADO09 março 2025
Super Dragon Ball Heroes Episódio 44 Completo JIREN SE IMPRESSIONA COM PODER DE BARDOCK LEGENDADO09 março 2025 -
best plot twists in games|Pesquisa do TikTok09 março 2025
-
 Middle-earth: Shadow of Mordor: Lord of the Hunt - IGN09 março 2025
Middle-earth: Shadow of Mordor: Lord of the Hunt - IGN09 março 2025 -
 Atividades que estimulam a memória #1 Jogo das Diferenças – APEXA09 março 2025
Atividades que estimulam a memória #1 Jogo das Diferenças – APEXA09 março 2025 -
 Loja de Jogos - PLAYEASY, R. Pedro Taques, 47 - Consolação, telefone +55 11 2594-993309 março 2025
Loja de Jogos - PLAYEASY, R. Pedro Taques, 47 - Consolação, telefone +55 11 2594-993309 março 2025 -
 HQ com crossover de Rick & Morty e Dungeons & Dragons é lançado09 março 2025
HQ com crossover de Rick & Morty e Dungeons & Dragons é lançado09 março 2025 -
 Sonic Superstars Steam Key for PC - Buy now09 março 2025
Sonic Superstars Steam Key for PC - Buy now09 março 2025 -
The Sims 4 Rumo à Fama: Trailer Oficial de Anúncio The Sims 4 Rumo à Fama é anunciado! Conheça o estilo de vida das celebridades com os seus Sims! Disponivel em09 março 2025
-
 Uncharted, novo 007, Mobius e outros filmes são adiados; veja o que muda - Canaltech09 março 2025
Uncharted, novo 007, Mobius e outros filmes são adiados; veja o que muda - Canaltech09 março 2025 -
 Frankenweenie Cat Mr. Whiskers. Needle Felted Cat. White Cat09 março 2025
Frankenweenie Cat Mr. Whiskers. Needle Felted Cat. White Cat09 março 2025

