Towards an Automated Process to Categorise Tor's Hidden Services
Por um escritor misterioso
Last updated 24 janeiro 2025
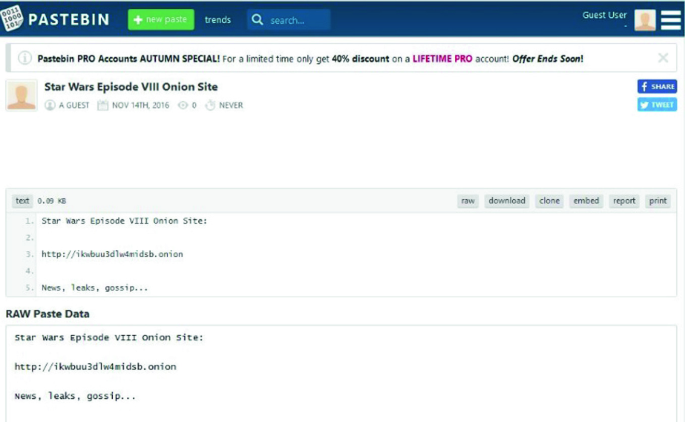
Detect malicious activity and protect your containerized workloads in EKS or AWS

Tor hidden service protocol overview
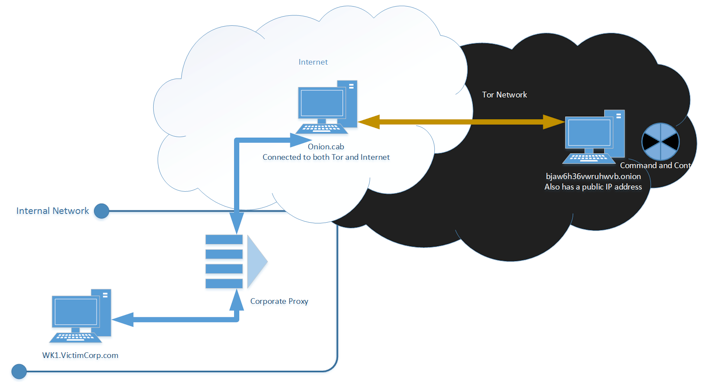
TOR Fronting — Utilising Hidden Services to Hide Attack Infrastructure, by Vincent Yiu

11 Ways Hackers are Using Automation to Boost Malware Attacks - 's Cybersecurity Blog

Towards an Automated Process to Categorise Tor's Hidden Services
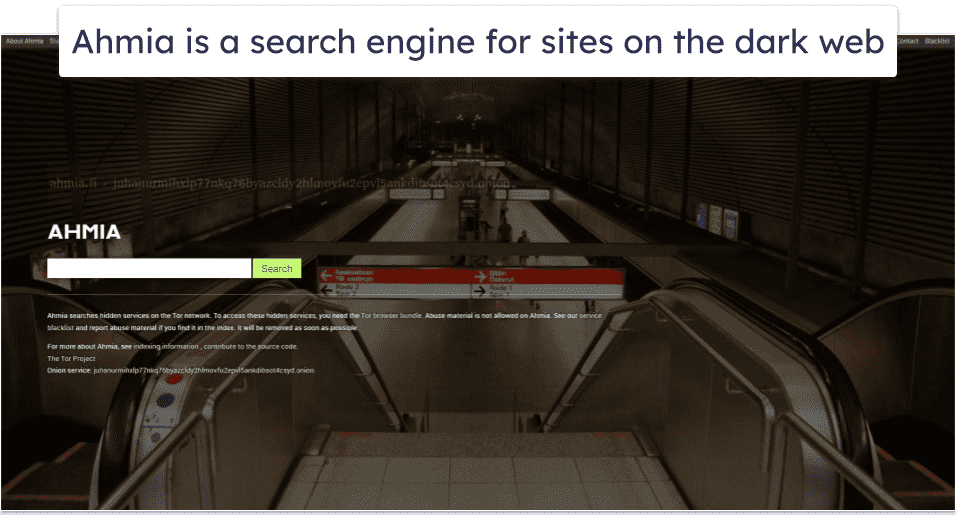
16 Best Dark Web Sites in 2023 + How to Stay Safe

The 6 Most Secure Email Services and the Security Measures They Practice

Botnet - Wikipedia
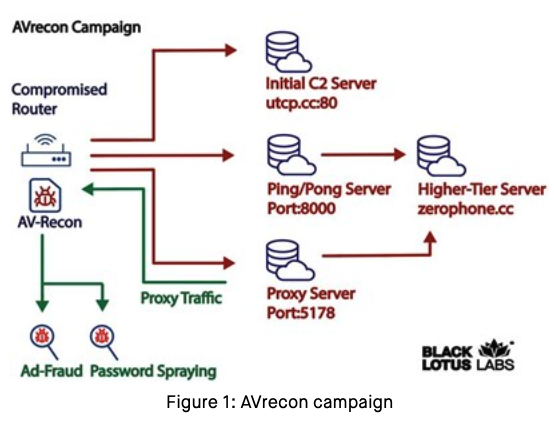
Who and What is Behind the Malware Proxy Service SocksEscort? – Krebs on Security

Can you trust Tor's hidden service directories? – Sophos News
Tor: Anonymity For Better or For Worse, by Leo Goldberg, Systems and Network Security
artificial intelligence Archives – Business Graduates Association
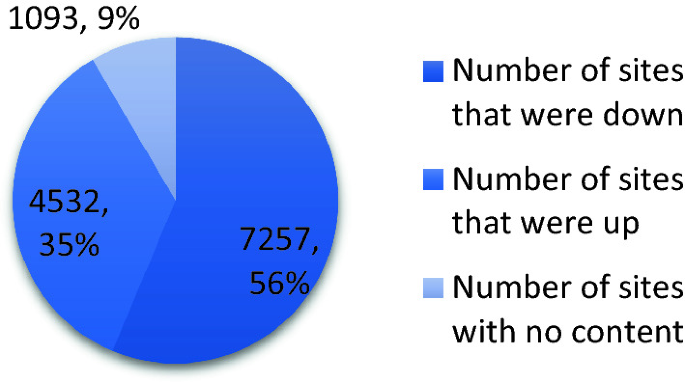
Towards an Automated Process to Categorise Tor's Hidden Services
Recomendado para você
-
 Nueva encuesta de HID revela cinco temas apremiantes que están reconfigurando la industria de la seguridad – Noticias ALAS24 janeiro 2025
Nueva encuesta de HID revela cinco temas apremiantes que están reconfigurando la industria de la seguridad – Noticias ALAS24 janeiro 2025 -
 SPEED DRAW SCRIPT HACK AUTOFARM INF COINS Roblox Speed Draw Script Pastebin 202324 janeiro 2025
SPEED DRAW SCRIPT HACK AUTOFARM INF COINS Roblox Speed Draw Script Pastebin 202324 janeiro 2025 -
roblox speed draw script pastebin|TikTokで検索24 janeiro 2025
-
Free Robux Script 202224 janeiro 2025
-
 Iri Shinsoj - Blog24 janeiro 2025
Iri Shinsoj - Blog24 janeiro 2025 -
 Speed Run 4 Script Pastebin Hacks - December 202324 janeiro 2025
Speed Run 4 Script Pastebin Hacks - December 202324 janeiro 2025 -
 Community Wishlist Survey 2016/Categories/Miscellaneous - Meta24 janeiro 2025
Community Wishlist Survey 2016/Categories/Miscellaneous - Meta24 janeiro 2025 -
2023 Hp Omen Ssd Install it24 janeiro 2025
-
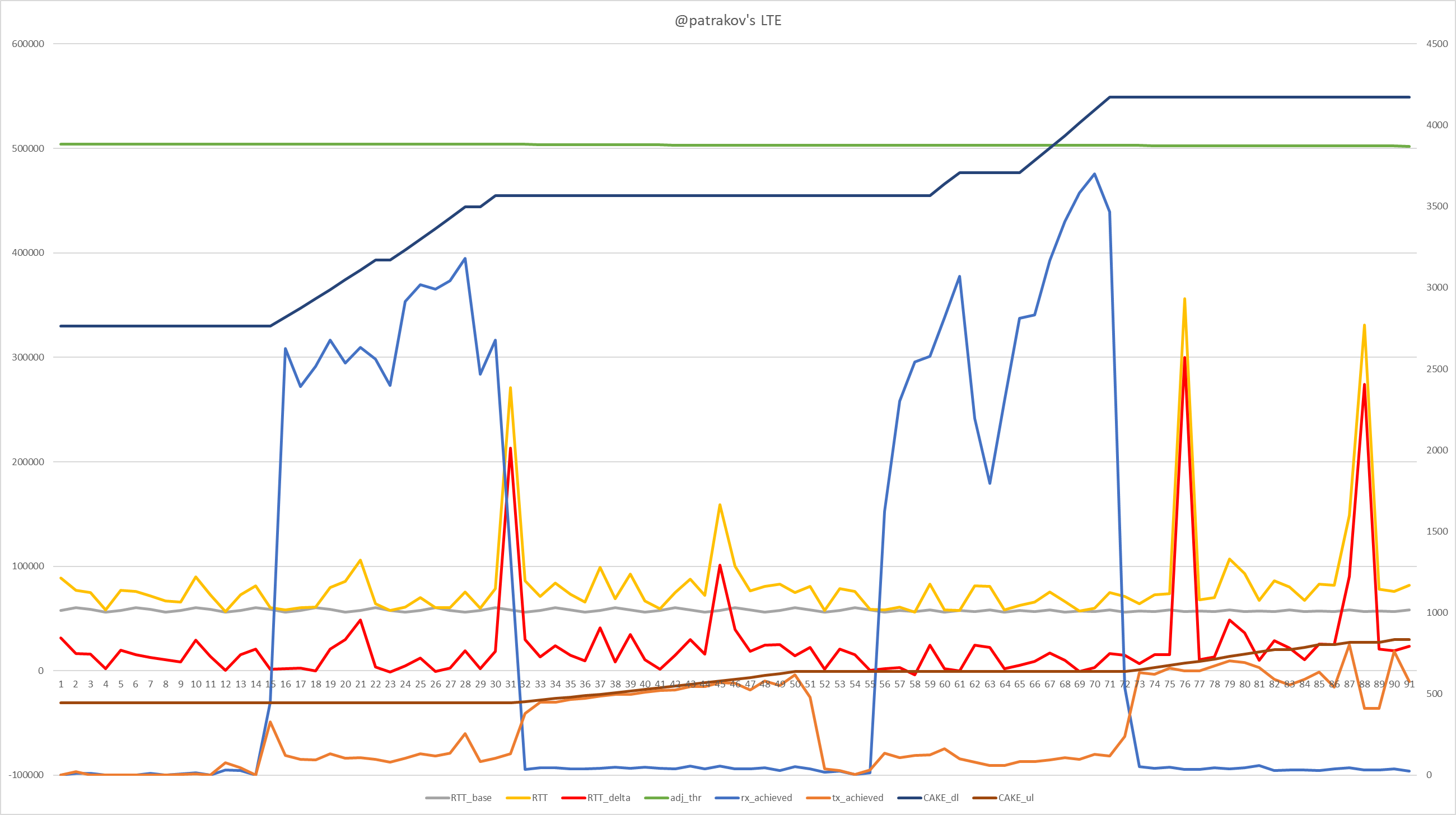 CAKE w/ Adaptive Bandwidth - Community Builds, Projects & Packages - OpenWrt Forum24 janeiro 2025
CAKE w/ Adaptive Bandwidth - Community Builds, Projects & Packages - OpenWrt Forum24 janeiro 2025 -
GitHub - Exunys/Aimbot-V2: ROBLOX Script - Universal Aimbot Script24 janeiro 2025
você pode gostar
-
Biografia de Rockefeller. ., PDF, John D. Rockefeller24 janeiro 2025
-
 ADACHI AND SHIMAMURA VOL 06 NOVEL – Anime Pop24 janeiro 2025
ADACHI AND SHIMAMURA VOL 06 NOVEL – Anime Pop24 janeiro 2025 -
 GIGANT 1 by Hiroya Oku24 janeiro 2025
GIGANT 1 by Hiroya Oku24 janeiro 2025 -
 Aproximadamente 1000 alunos prestigiam o 5º Racha Cuca do Rui24 janeiro 2025
Aproximadamente 1000 alunos prestigiam o 5º Racha Cuca do Rui24 janeiro 2025 -
Games Like Salon de Bailes 🥵 [chat de voz]24 janeiro 2025
-
Seishun Buta Yarou wa Yumemiru Shoujo no Yume wo Minai - trailer do filme de Bunny Girl que vai adaptar o 6° e 7° volumes da light novel. O filme vai24 janeiro 2025
-
 Deaimon Recipe for Happiness24 janeiro 2025
Deaimon Recipe for Happiness24 janeiro 2025 -
 MC Teteu - Dingo Bell (GR6 Explode) Perera DJ24 janeiro 2025
MC Teteu - Dingo Bell (GR6 Explode) Perera DJ24 janeiro 2025 -
 Jumping Dino - Download do APK para Android24 janeiro 2025
Jumping Dino - Download do APK para Android24 janeiro 2025 -
 SG Choice: Our Recommended Nintendo 3DS & Wii U Software – Source24 janeiro 2025
SG Choice: Our Recommended Nintendo 3DS & Wii U Software – Source24 janeiro 2025


