Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 04 junho 2024

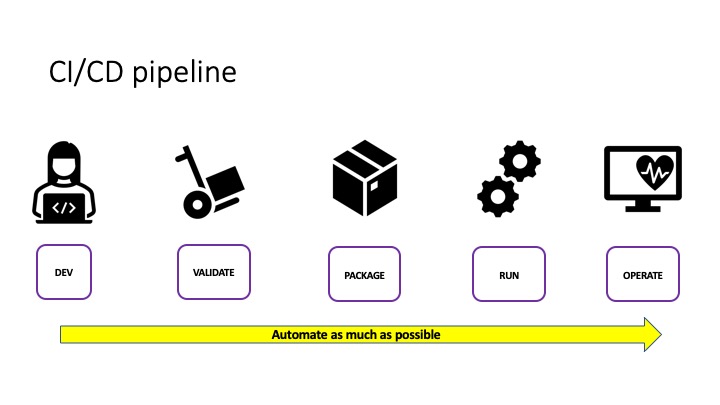
Building a security-conscious CI/CD pipeline

Getting Started With CI/CD Pipeline Security - DZone Refcardz

How to Add Application Security Tests to Your CI/CD Pipeline

Vulnerability Scanning in GitHub CI/CD Workflow using Grype
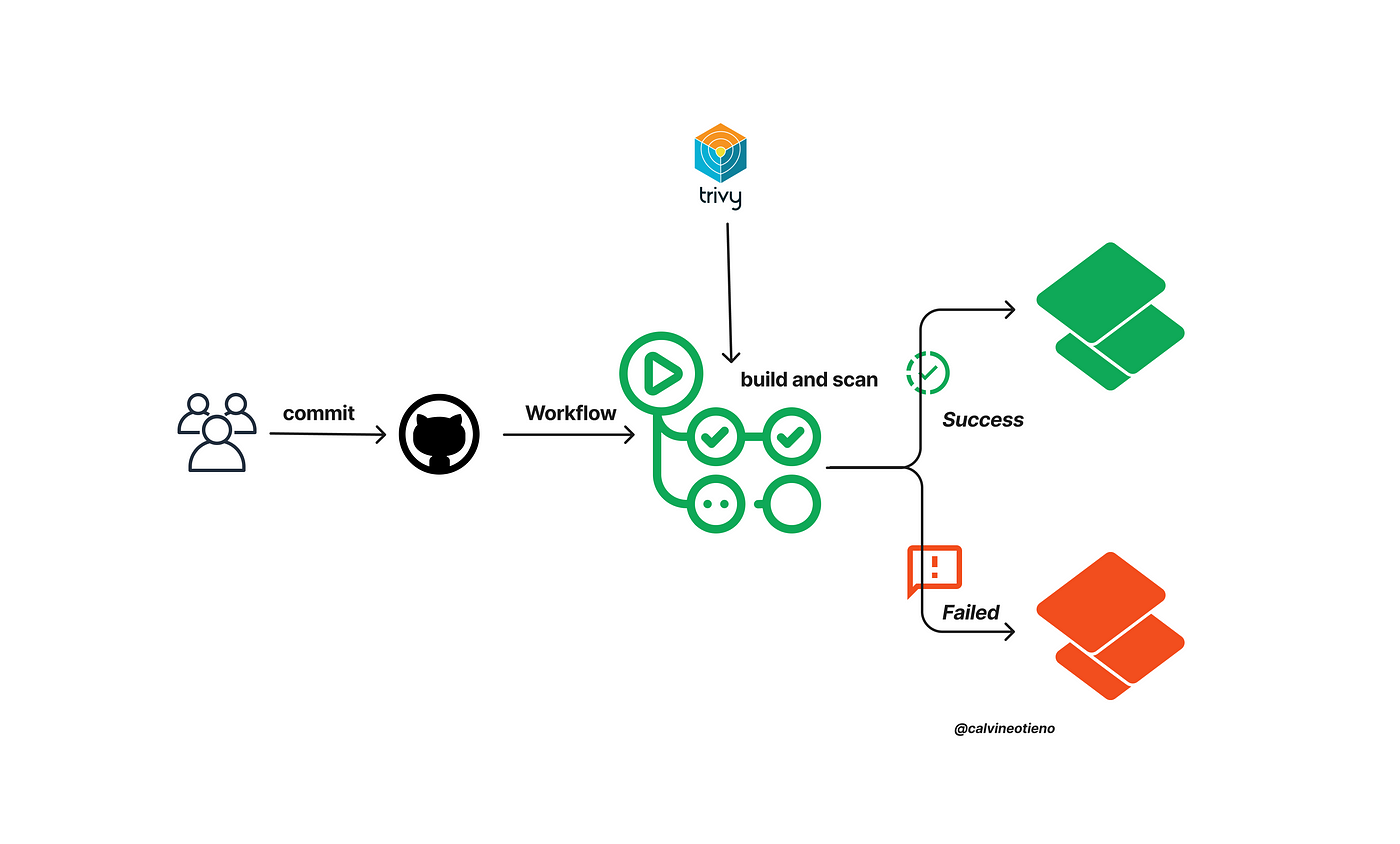
Improving your CI/CD Pipeline: Helm Charts Security Scanning with Trivy and GitHub Actions, by Calvine Otieno
DevSecOps in AWS using different security tools Part-I, by Rakesh Chatla

Enhance your CI/CD deployment by using Vulnerability Assessments from Azure Defender for ACR – Azure Aggregator

Vulnerability Scanning in your CI/CD Pipeline - Part Two
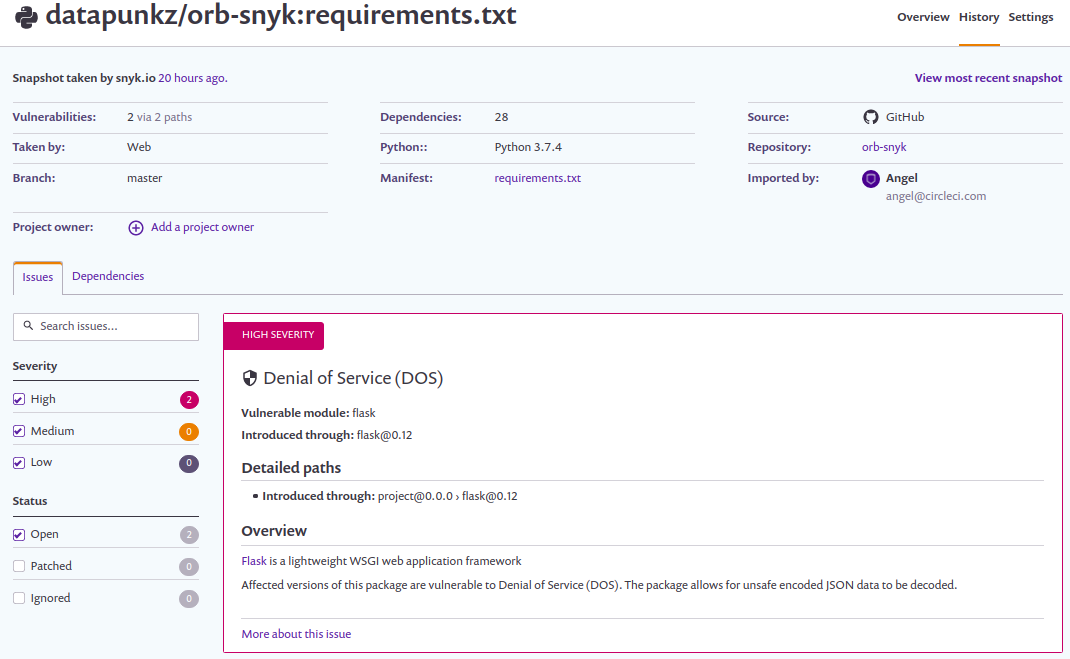
Adding application and image scans to your CI/CD pipeline

Implement DevSecOps to Secure Your CI/CD Pipeline

10 Steps to Automate Container Security Into the CI/CD Pipeline
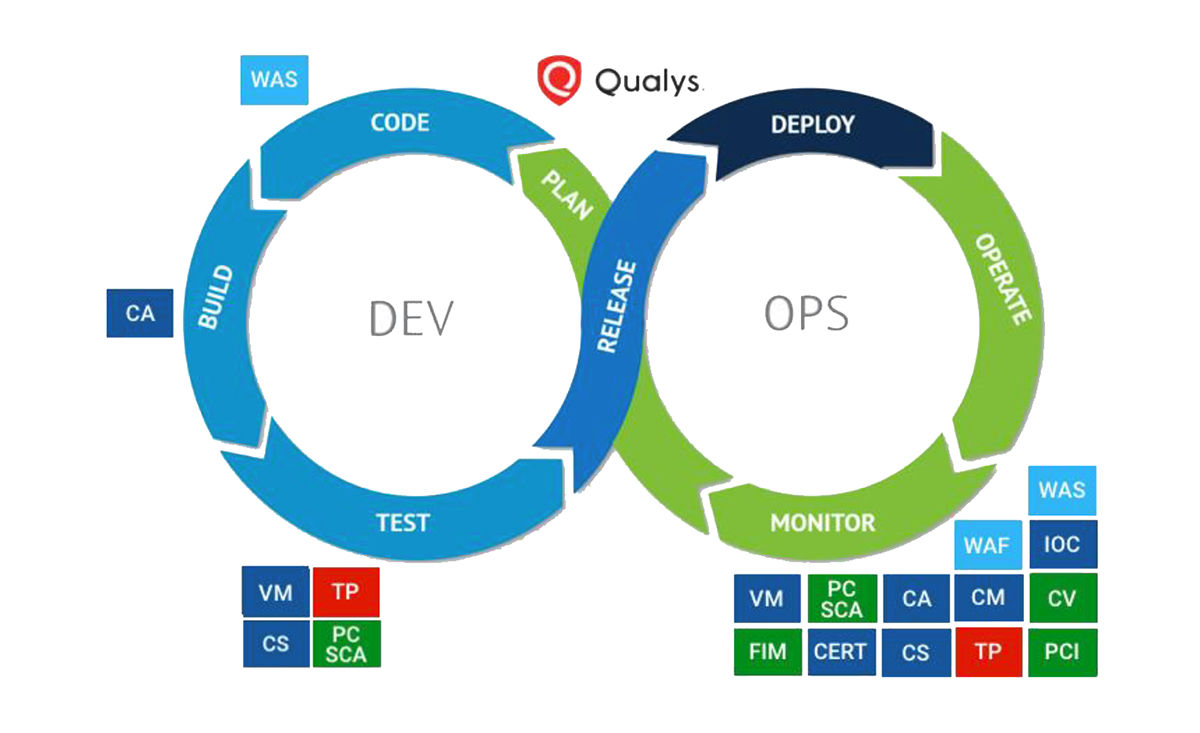
Assess Vulnerabilities, Misconfigurations in CI/CD Pipeline
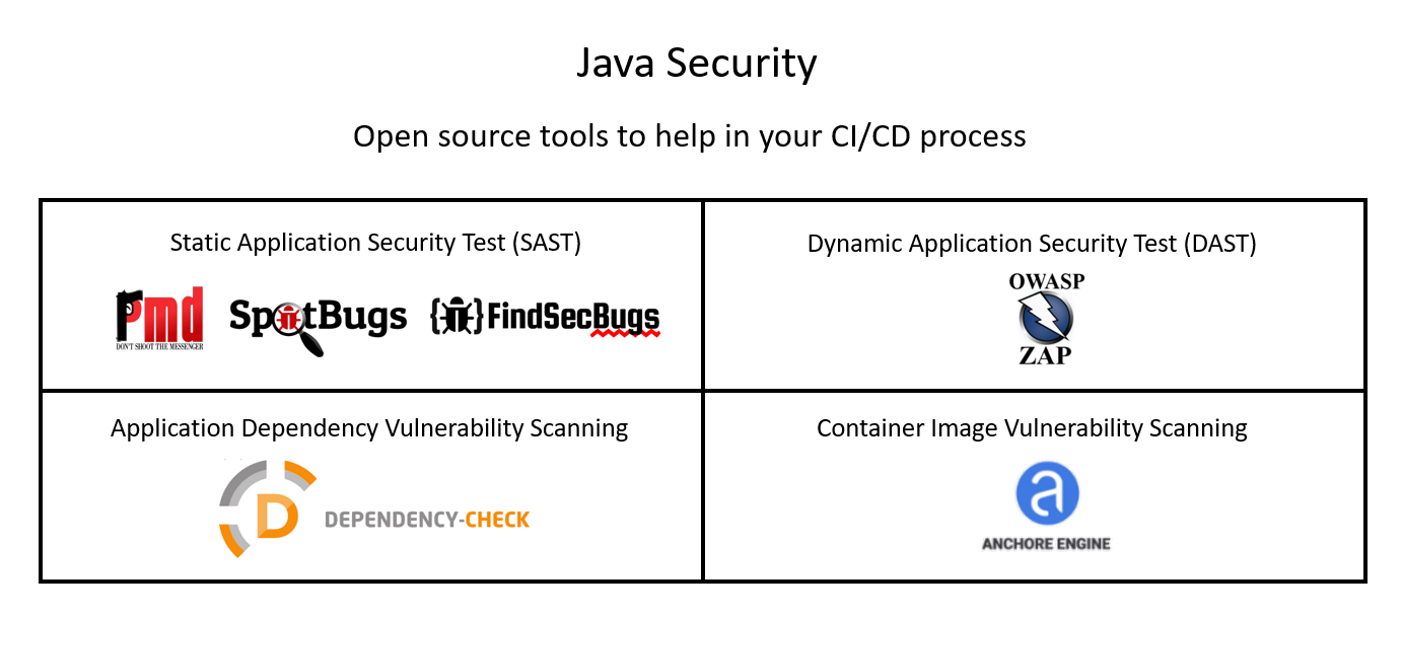
Java Security: Open Source tools for use in CI/CD pipelines

Checkov enables developer-first CI/CD security with new supply chain security policies - Bridgecrew Blog
Recomendado para você
-
 Top 5 Alternatives to Nexus Vulnerability Scanner (December 2023)04 junho 2024
Top 5 Alternatives to Nexus Vulnerability Scanner (December 2023)04 junho 2024 -
 NEXUS iOS Generation 2.0 Scan Gauges Walk-Thru with Michael Tuckman04 junho 2024
NEXUS iOS Generation 2.0 Scan Gauges Walk-Thru with Michael Tuckman04 junho 2024 -
Nexus iOS Scan Example on Vimeo04 junho 2024
-
 DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server04 junho 2024
DevSecOps Delivered: Scan a Docker Image with Nexus IQ Server04 junho 2024 -
 Scan to Win Big with Nexus Appliances while watching Big Brother Naija!04 junho 2024
Scan to Win Big with Nexus Appliances while watching Big Brother Naija!04 junho 2024 -
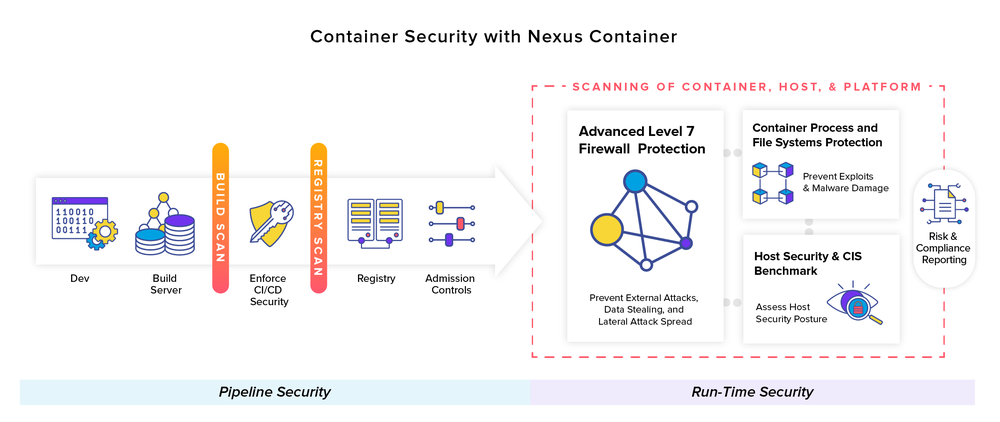 Nexus Container Reviews - 202304 junho 2024
Nexus Container Reviews - 202304 junho 2024 -
Nexus iOS - Nexus iOS Scan Gauges provide the most04 junho 2024
-
Nexus Scanning not working if application has defined build variants · Issue #31 · sonatype-nexus-community/scan-gradle-plugin · GitHub04 junho 2024
-
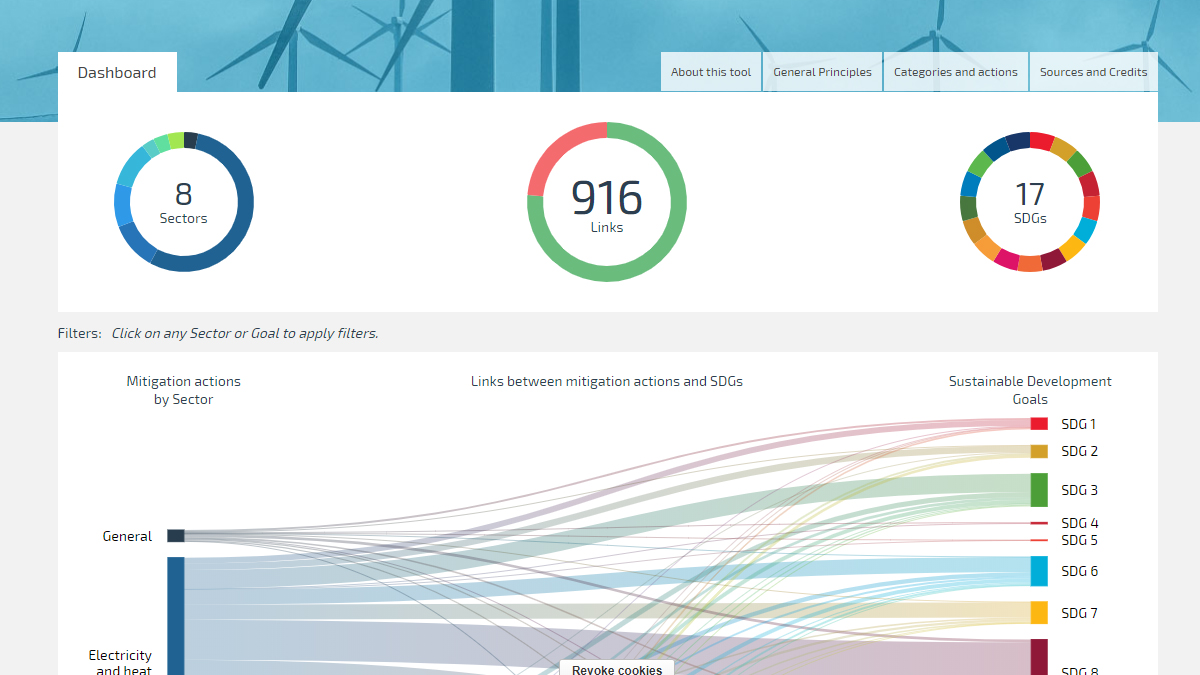 SCAN tool NewClimate Institute04 junho 2024
SCAN tool NewClimate Institute04 junho 2024 -
 Nessus04 junho 2024
Nessus04 junho 2024
você pode gostar
-
 Bora jogar? Portal Capoeira04 junho 2024
Bora jogar? Portal Capoeira04 junho 2024 -
Death Note Caderno da Morte para Cosplay Anime L Kira Ryuk Anime Livro Manga Misa Amane | Item de Decoração Flufi Nunca Usado 74332227 | enjoei04 junho 2024
-
 Who the hell is Steve Jobs? / G-Man :: Half-Life :: приколы для даунов со знанием английского :: без перевода :: анимация :: freeman :: Игры / картинки, гифки, прикольные комиксы, интересные статьи по теме.04 junho 2024
Who the hell is Steve Jobs? / G-Man :: Half-Life :: приколы для даунов со знанием английского :: без перевода :: анимация :: freeman :: Игры / картинки, гифки, прикольные комиксы, интересные статьи по теме.04 junho 2024 -
 POD Clothing Anime Roblox Girls for Kids Child Love Roblox Character Print T shirt Teens Age Girls Friendship Tops Tees (as4, age, 9_years, 10_years, regular): Buy Online at Best Price in UAE04 junho 2024
POD Clothing Anime Roblox Girls for Kids Child Love Roblox Character Print T shirt Teens Age Girls Friendship Tops Tees (as4, age, 9_years, 10_years, regular): Buy Online at Best Price in UAE04 junho 2024 -
 Trailer - Rebel Moon04 junho 2024
Trailer - Rebel Moon04 junho 2024 -
 WCA 2016 first season EU open qualifiers - Dota Blast Dota Blast04 junho 2024
WCA 2016 first season EU open qualifiers - Dota Blast Dota Blast04 junho 2024 -
 Jogo Real Flight Simulator no Jogos 36004 junho 2024
Jogo Real Flight Simulator no Jogos 36004 junho 2024 -
 Angels of Death, RPG Maker Wiki04 junho 2024
Angels of Death, RPG Maker Wiki04 junho 2024 -
 Rumor: The Rings Of Power Season 2 Makes A Huge Change To Upcoming Sauron Battle04 junho 2024
Rumor: The Rings Of Power Season 2 Makes A Huge Change To Upcoming Sauron Battle04 junho 2024 -
 Ao Ashi Episódio 20: Data de Lançamento, Assistir Online, Discussão04 junho 2024
Ao Ashi Episódio 20: Data de Lançamento, Assistir Online, Discussão04 junho 2024

