Google Vulnerability Rewards Program, XSS, Best Practices
Por um escritor misterioso
Last updated 02 março 2025
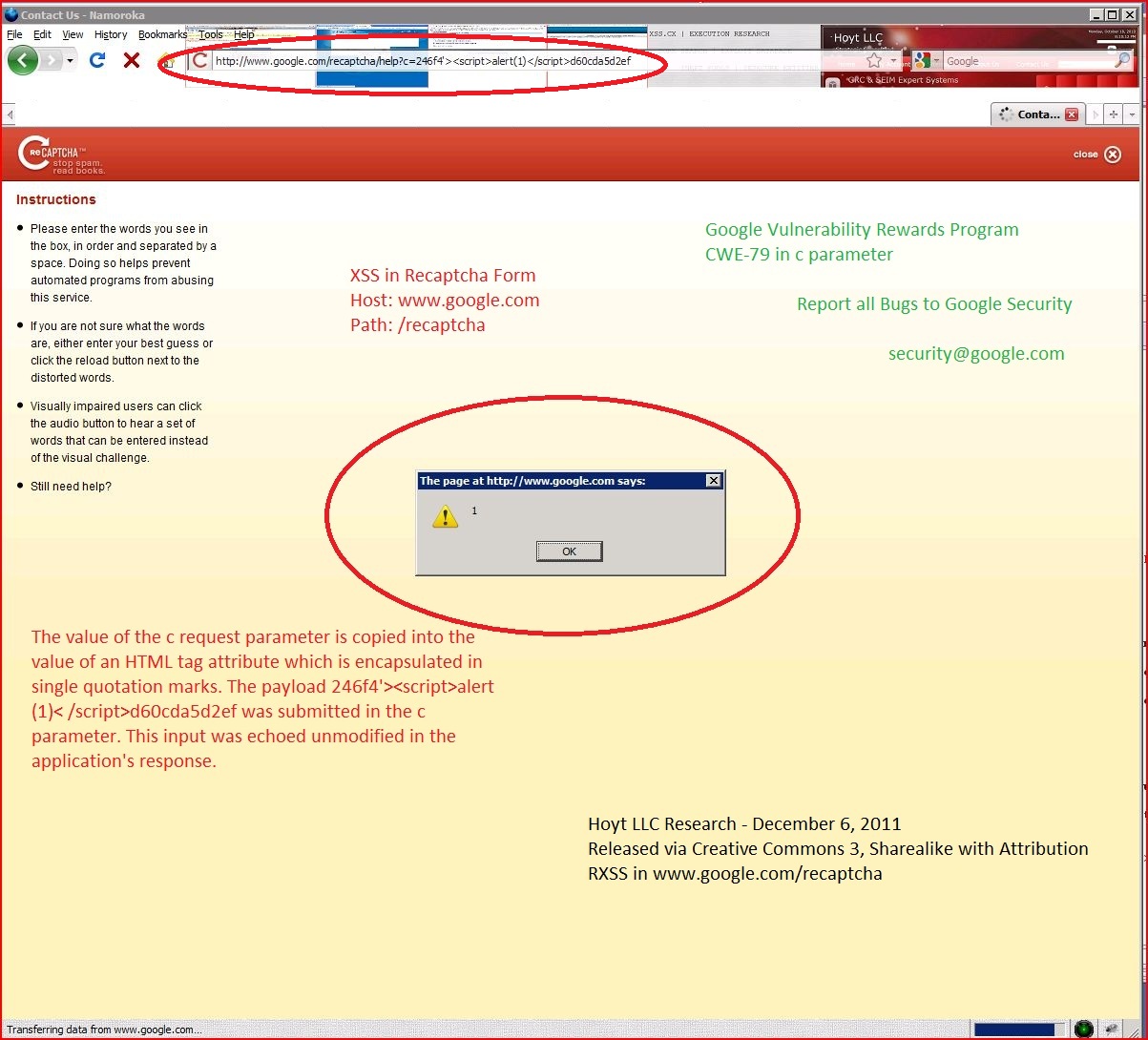
Phishing, Insecure Configuration, XSS, Cross Site Scripting, Best Practices, Vulnerability Management, Captcha Form, vulnerability rewards program, google.com, CWE-79, CAPEC-86, DORK, GHDB Report by

How Chrome DevTools helps to defend against self-XSS attacks, Blog

How to Prevent XSS Attacks: What DoubleClick Advertisers Need to Know

$3133.7 Google Bug Bounty Writeup- XSS Vulnerability! - Pethuraj's Blog
Chapter 21: Building Secure and Reliable Systems

A Detailed Guide to Cross-Site Scripting (XSS)

XSS- an application security vulnerability

Figure 1 from Preventing persistent Cross-Site Scripting (XSS) attack by applying pattern filtering approach

Ben Hayak - Security Blog: Google Mail Hacking - Gmail Stored XSS - 2012!

Dangerous XSS bug in Google Chrome's 'New Tab' page bypassed security features
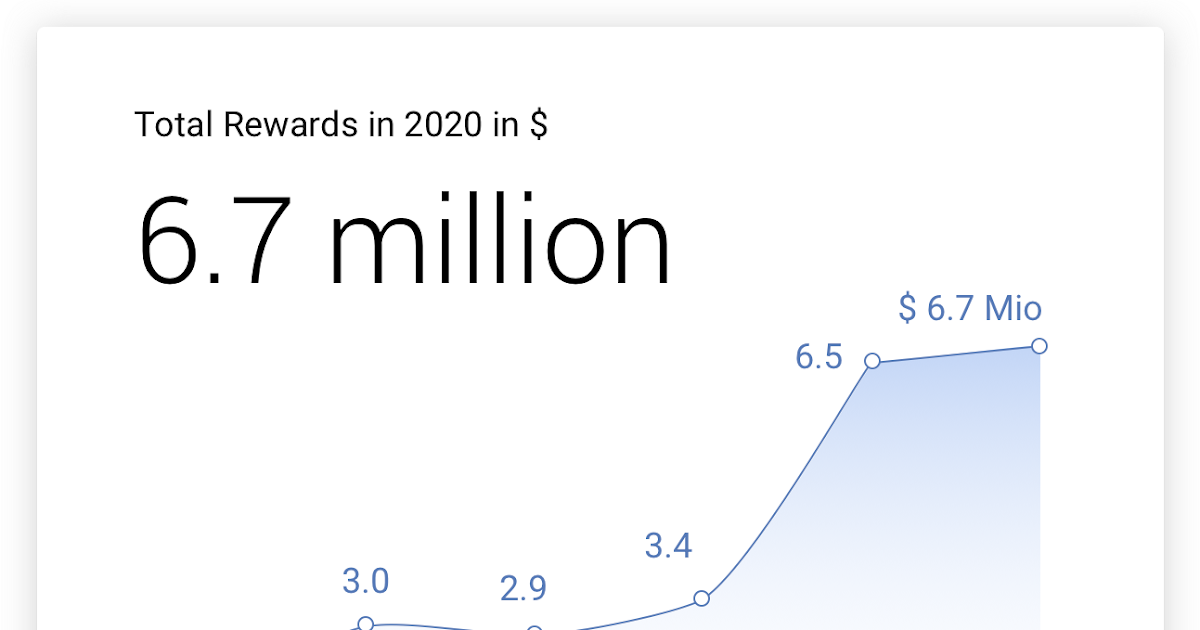
Google Online Security Blog: Vulnerability Reward Program: 2020 Year in Review
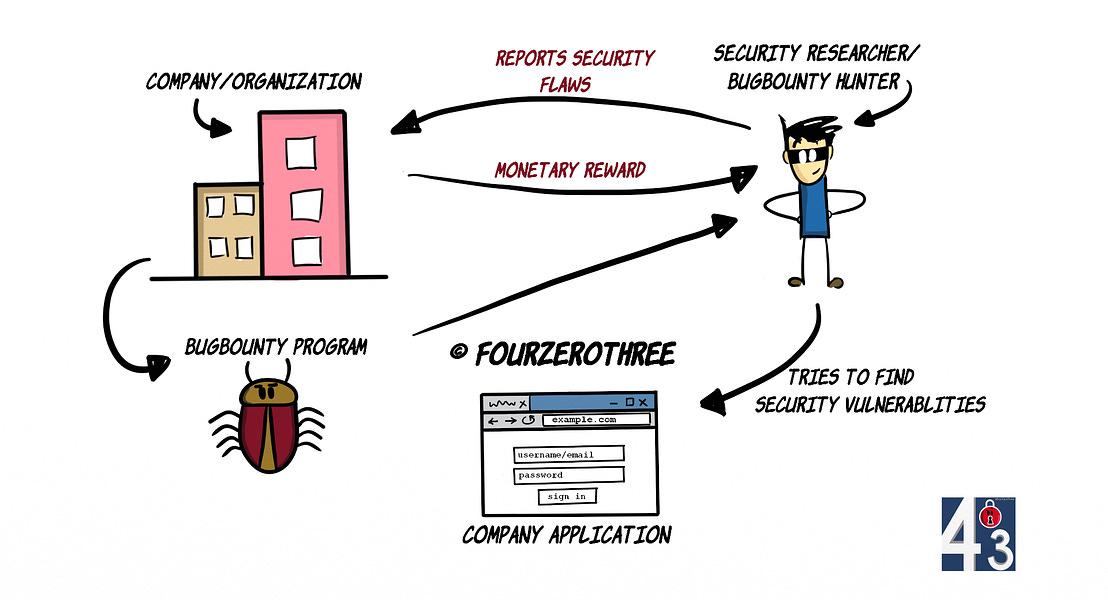
The fascinating World of Bug Bounty hunting - What it is and how you could get your feet wet
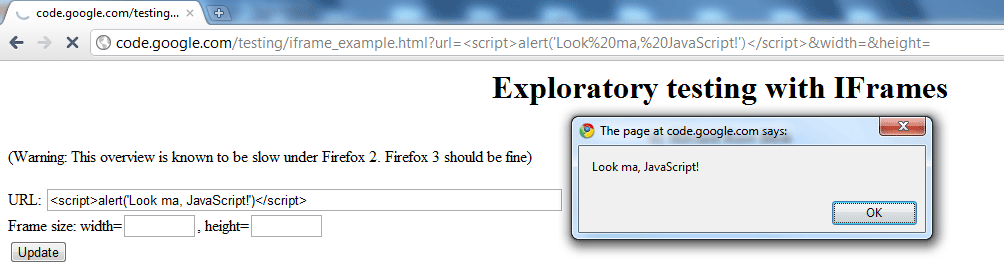
Google Vulnerability Reward Program: XSS Vulnerability in Google Code Static HTML » Neal Poole
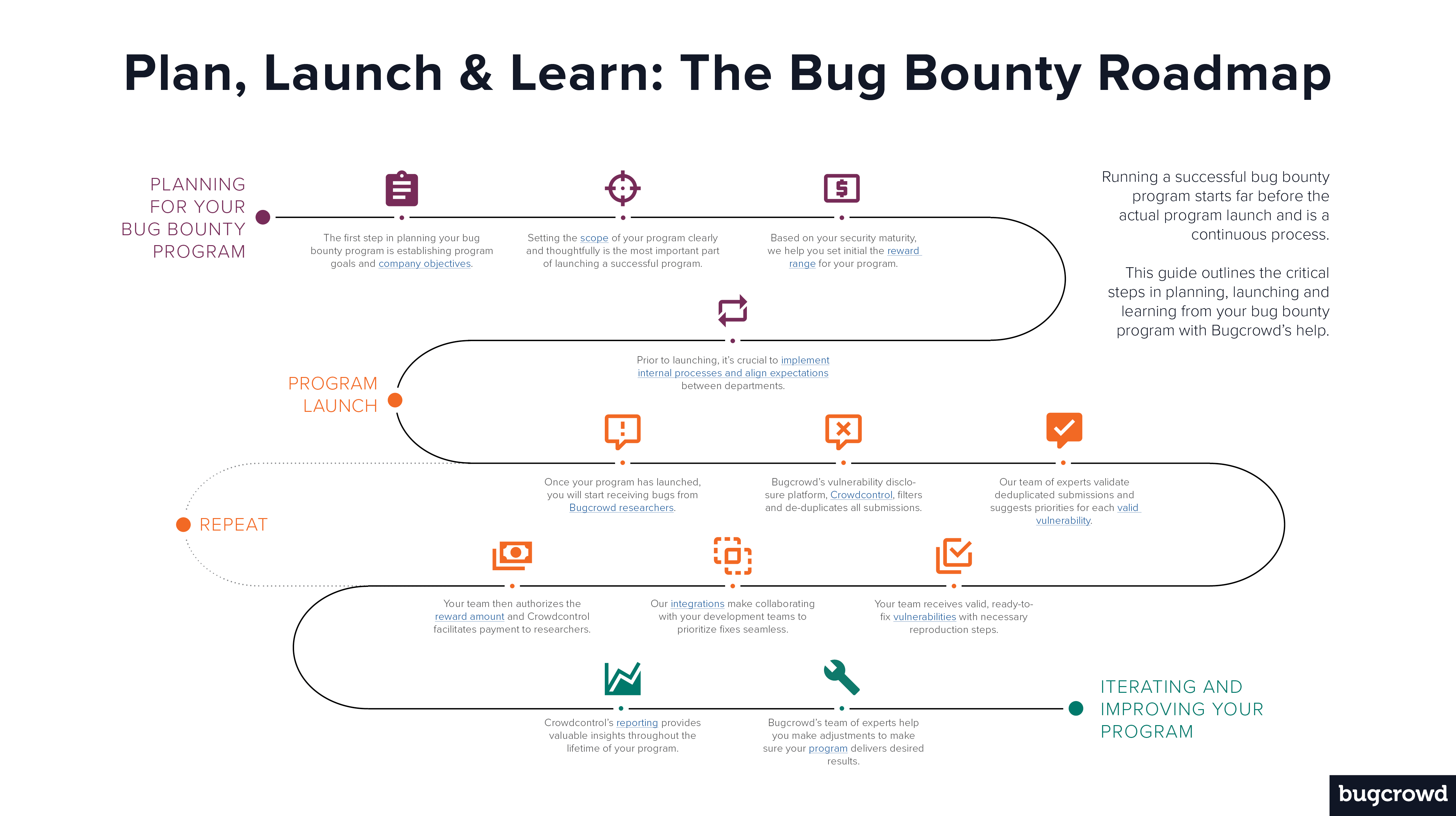
Illustrated Guide to Bug Bounties Step #3: Learnings

Google's Bug Bounty Hits $12 Million: What About the Risks?

The process of reflected XSS Attack
Recomendado para você
-
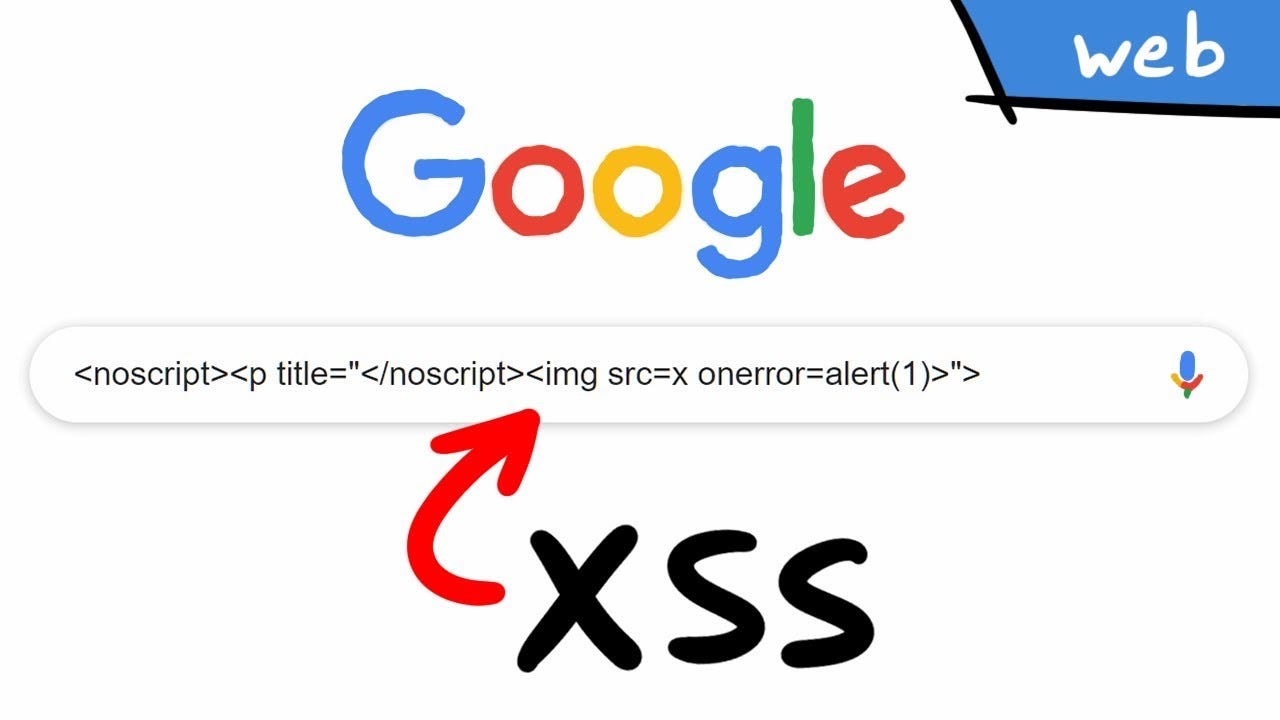 Cross Site Scripting ( XSS ) Vulnerability Payload List02 março 2025
Cross Site Scripting ( XSS ) Vulnerability Payload List02 março 2025 -
 What is DOM-based XSS (cross-site scripting)?02 março 2025
What is DOM-based XSS (cross-site scripting)?02 março 2025 -
Xsss02 março 2025
-
now.eloqua.com, XSS, Javascript Injection, Cross Site Scripting02 março 2025
-
 ExScal Topology. Dots represent XSMs and triangles represent XSSs02 março 2025
ExScal Topology. Dots represent XSMs and triangles represent XSSs02 março 2025 -
 MFSs and XSSs of our threshold query example on the lattice of02 março 2025
MFSs and XSSs of our threshold query example on the lattice of02 março 2025 -
Xsss store02 março 2025
-
 XSSS-ZC Universal Tile Hole Opener, Adjustable Positioning Ruler, Engineering Measurement T-Ruler, Woodworking Long Ruler, Multi-Functional Drilling02 março 2025
XSSS-ZC Universal Tile Hole Opener, Adjustable Positioning Ruler, Engineering Measurement T-Ruler, Woodworking Long Ruler, Multi-Functional Drilling02 março 2025 -
 XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*8m02 março 2025
XSSS-ZC Transparent Rain Cloth, Rain Tarpaulin, PVC Windshield Cloth, Balcony Plastic Cloth, Canvas, Oil Cloth,4m*8m02 março 2025 -
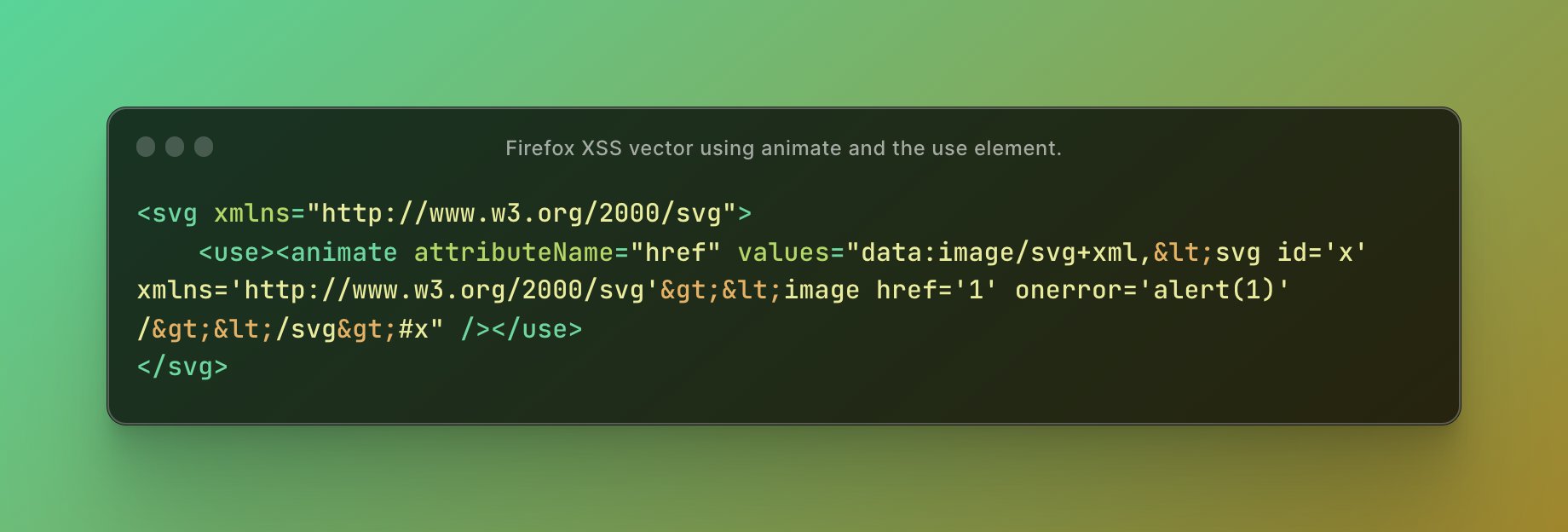 Gareth Heyes on X: A quite wonderful Firefox only XSS vector02 março 2025
Gareth Heyes on X: A quite wonderful Firefox only XSS vector02 março 2025
você pode gostar
-
 Quem você seria em fnaf 102 março 2025
Quem você seria em fnaf 102 março 2025 -
 Getsuyoubi no Tawawa / Tawawa on Monday 1-8 set Manga Comic Japanese version02 março 2025
Getsuyoubi no Tawawa / Tawawa on Monday 1-8 set Manga Comic Japanese version02 março 2025 -
 Uruguay 2-0 Cuba: Muchas pruebas, pocos goles y escaso fútbol - La Oral Deportiva02 março 2025
Uruguay 2-0 Cuba: Muchas pruebas, pocos goles y escaso fútbol - La Oral Deportiva02 março 2025 -
 Roblox Kaizen codes December 2023 (Geto update): Double XP, free02 março 2025
Roblox Kaizen codes December 2023 (Geto update): Double XP, free02 março 2025 -
 Conjuntos Comerciais e Salas à venda na Avenida Nações Unidas em Bauru, SP - ZAP Imóveis02 março 2025
Conjuntos Comerciais e Salas à venda na Avenida Nações Unidas em Bauru, SP - ZAP Imóveis02 março 2025 -
 VÍDEO: o resumo do empate no Sp. Braga-Sporting - CNN Portugal02 março 2025
VÍDEO: o resumo do empate no Sp. Braga-Sporting - CNN Portugal02 março 2025 -
 Cracker's Wither Storm Mod Bare Bones Compatibility - Minecraft Resource Packs - CurseForge02 março 2025
Cracker's Wither Storm Mod Bare Bones Compatibility - Minecraft Resource Packs - CurseForge02 março 2025 -
 Pibby Annoying Orange (SlightlyCreative)02 março 2025
Pibby Annoying Orange (SlightlyCreative)02 março 2025 -
 Halo Infinite Season 2: All known issues, bugs, and workarounds02 março 2025
Halo Infinite Season 2: All known issues, bugs, and workarounds02 março 2025 -
 Bridget walk transparent GIF : r/Guiltygear02 março 2025
Bridget walk transparent GIF : r/Guiltygear02 março 2025

