TrustedSec Playing With Old Hacks
Por um escritor misterioso
Last updated 02 março 2025


Russian government officials charged in cyber-attacks targeting US and other energy companies around the world

Gaming the game: Popular video games can be vulnerable to hackers

Hackers' at 20

We're Surrounded by Billions of Internet-connected Devices. Can We Trust Them?

Dr. Alvaro Cárdenas Discusses His Lab's Recent IoT Hacks with Newsweek - Computer Science

A Chat With Justin Elze, Director of Innovation, Research, and Advanced Testing at TrustedSec

Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo
Ethical Hacking - Email Hijacking

Hackers, Trolls, and Bots Ready For Election Day - TheStreet

Oldsmar's water supply attack is a warning, experts say. It could've been worse.

FireEye CEO: Reckless Microsoft hack unusual for China

Raspberry Pi – Page 2 – CYBER ARMS – Computer Security
Recomendado para você
-
 How to use CMD.exe (Command Prompt)02 março 2025
How to use CMD.exe (Command Prompt)02 março 2025 -
 Executing Command Prompt commands in SSIS – SQL Server Rider02 março 2025
Executing Command Prompt commands in SSIS – SQL Server Rider02 março 2025 -
 Export the output of the command prompt (cmd.exe) TXT, RTF, HTML02 março 2025
Export the output of the command prompt (cmd.exe) TXT, RTF, HTML02 março 2025 -
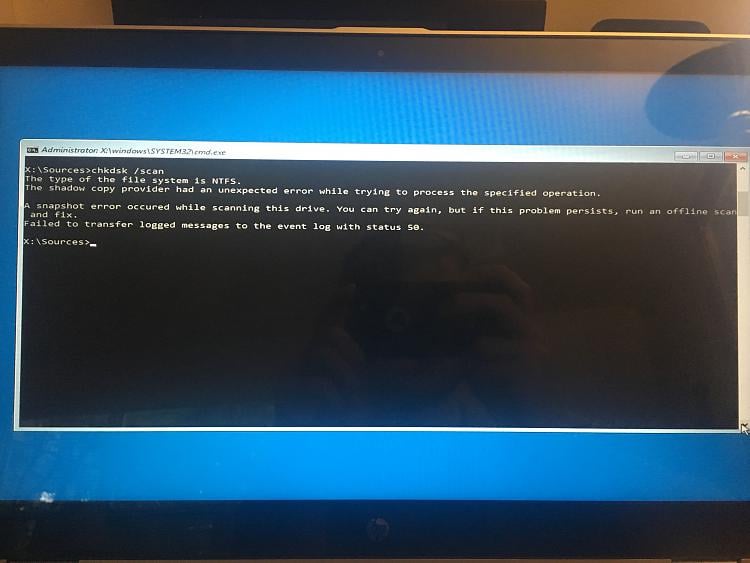 Windows 10 Help Forums02 março 2025
Windows 10 Help Forums02 março 2025 -
 command line - Is there a keyboard shortcut to pause the output of a CMD window while it's running? - Super User02 março 2025
command line - Is there a keyboard shortcut to pause the output of a CMD window while it's running? - Super User02 março 2025 -
 Mastering the Command Prompt: Windows Beginners' Guide in 2023 - EaseUS02 março 2025
Mastering the Command Prompt: Windows Beginners' Guide in 2023 - EaseUS02 março 2025 -
 cmd.exe - Cannot `cd` to E: drive using Windows CMD command line - Super User02 março 2025
cmd.exe - Cannot `cd` to E: drive using Windows CMD command line - Super User02 março 2025 -
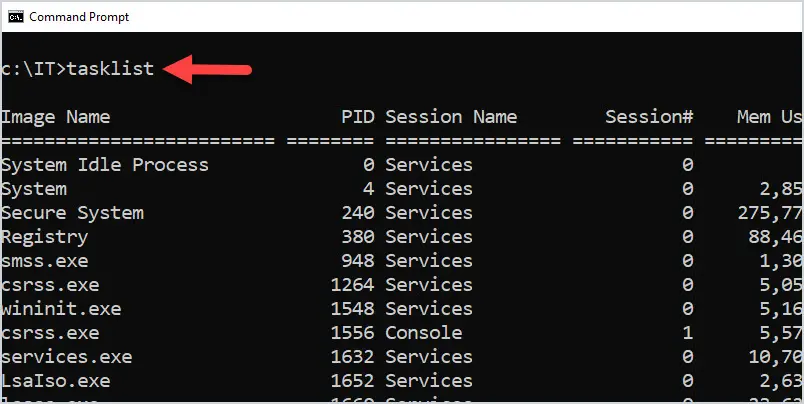 50 Basic Windows Commands with Examples - Active Directory Pro02 março 2025
50 Basic Windows Commands with Examples - Active Directory Pro02 março 2025 -
Why does the command prompt open on Startup Windows 10? - Quora02 março 2025
-
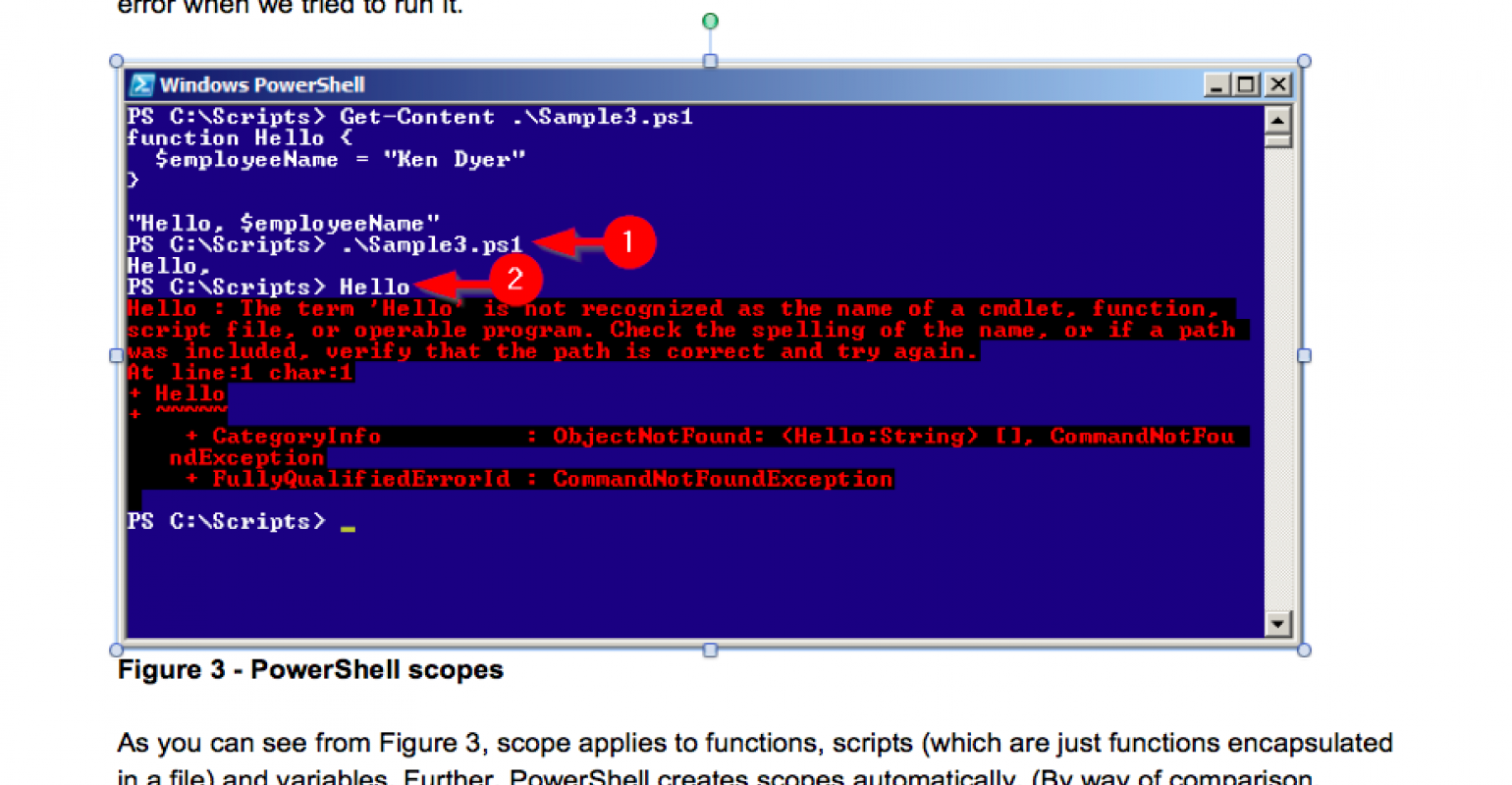 PowerShell: Why You'll Never Go Back to Cmd.exe Batch Files02 março 2025
PowerShell: Why You'll Never Go Back to Cmd.exe Batch Files02 março 2025
você pode gostar
-
 The Maze Runner Author Interview, James Dashner02 março 2025
The Maze Runner Author Interview, James Dashner02 março 2025 -
 Calico Cat Icons - Free SVG & PNG Calico Cat Images - Noun Project02 março 2025
Calico Cat Icons - Free SVG & PNG Calico Cat Images - Noun Project02 março 2025 -
 ZachPlayzRoblox on X: Roblox meme that u said / X02 março 2025
ZachPlayzRoblox on X: Roblox meme that u said / X02 março 2025 -
 NVIDIA Unleashes GeForce RTX 4060 Ti In 8 GB & 16 GB Flavors, $399 & $499 US Pricing, 70% Faster Than 3060 Ti02 março 2025
NVIDIA Unleashes GeForce RTX 4060 Ti In 8 GB & 16 GB Flavors, $399 & $499 US Pricing, 70% Faster Than 3060 Ti02 março 2025 -
 Toxel - Shiny Star V #57 Pokemon Card02 março 2025
Toxel - Shiny Star V #57 Pokemon Card02 março 2025 -
 The Desperado Days — Trnsfr02 março 2025
The Desperado Days — Trnsfr02 março 2025 -
 Berserk: The Golden Age Arc – Memorial Edition Streaming: Watch & Stream Online via Crunchyroll02 março 2025
Berserk: The Golden Age Arc – Memorial Edition Streaming: Watch & Stream Online via Crunchyroll02 março 2025 -
 Apple Watch Series 8 review02 março 2025
Apple Watch Series 8 review02 março 2025 -
 I got a Rat King piece but I feel like it's missing something. Anything i can add to this? : r/tattooadvice02 março 2025
I got a Rat King piece but I feel like it's missing something. Anything i can add to this? : r/tattooadvice02 março 2025 -
pou bebe - Roblox02 março 2025
