Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Last updated 26 fevereiro 2025
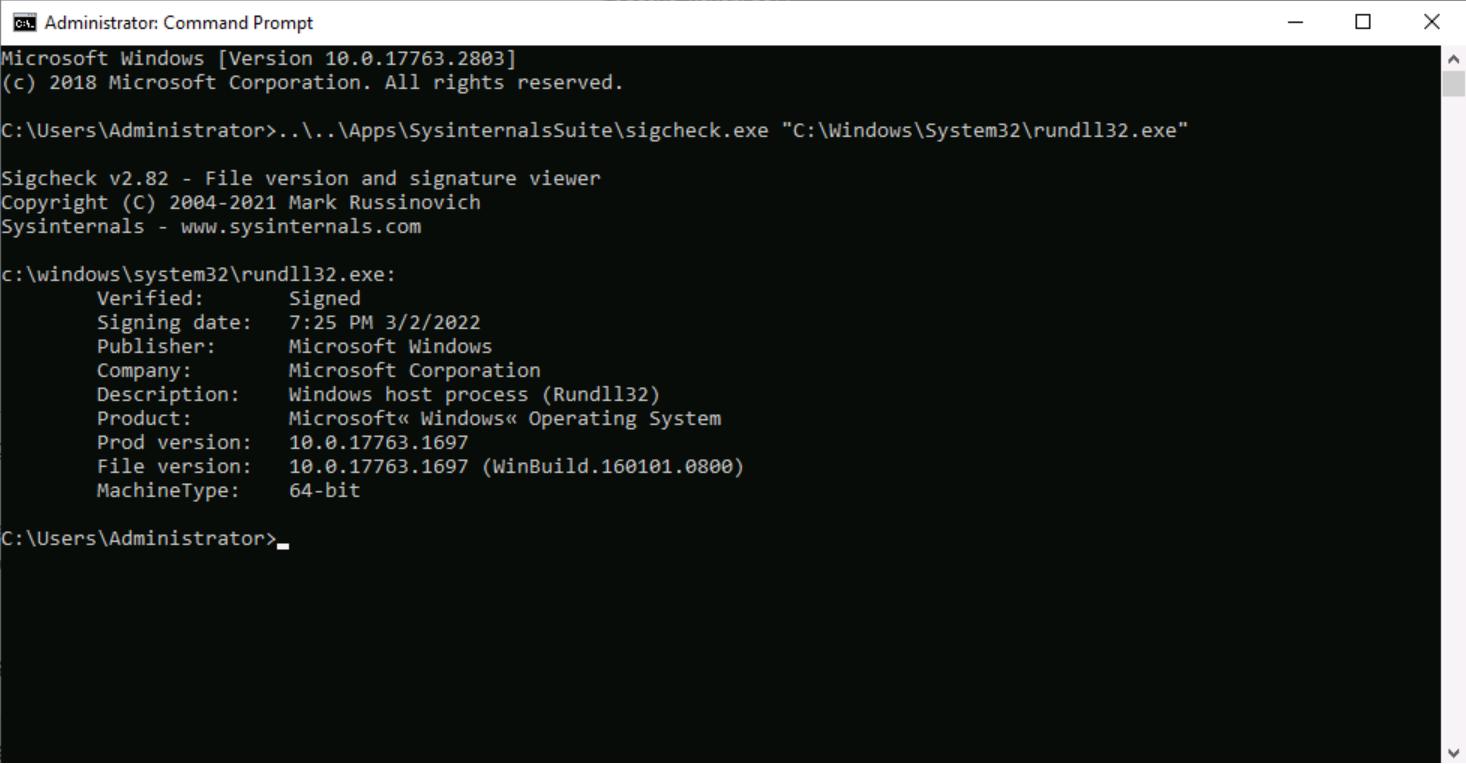
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

Detect PlugX Trojan Masquerading as a Legitimate Windows Debugger Tool to Fly Under the Radar - SOC Prime
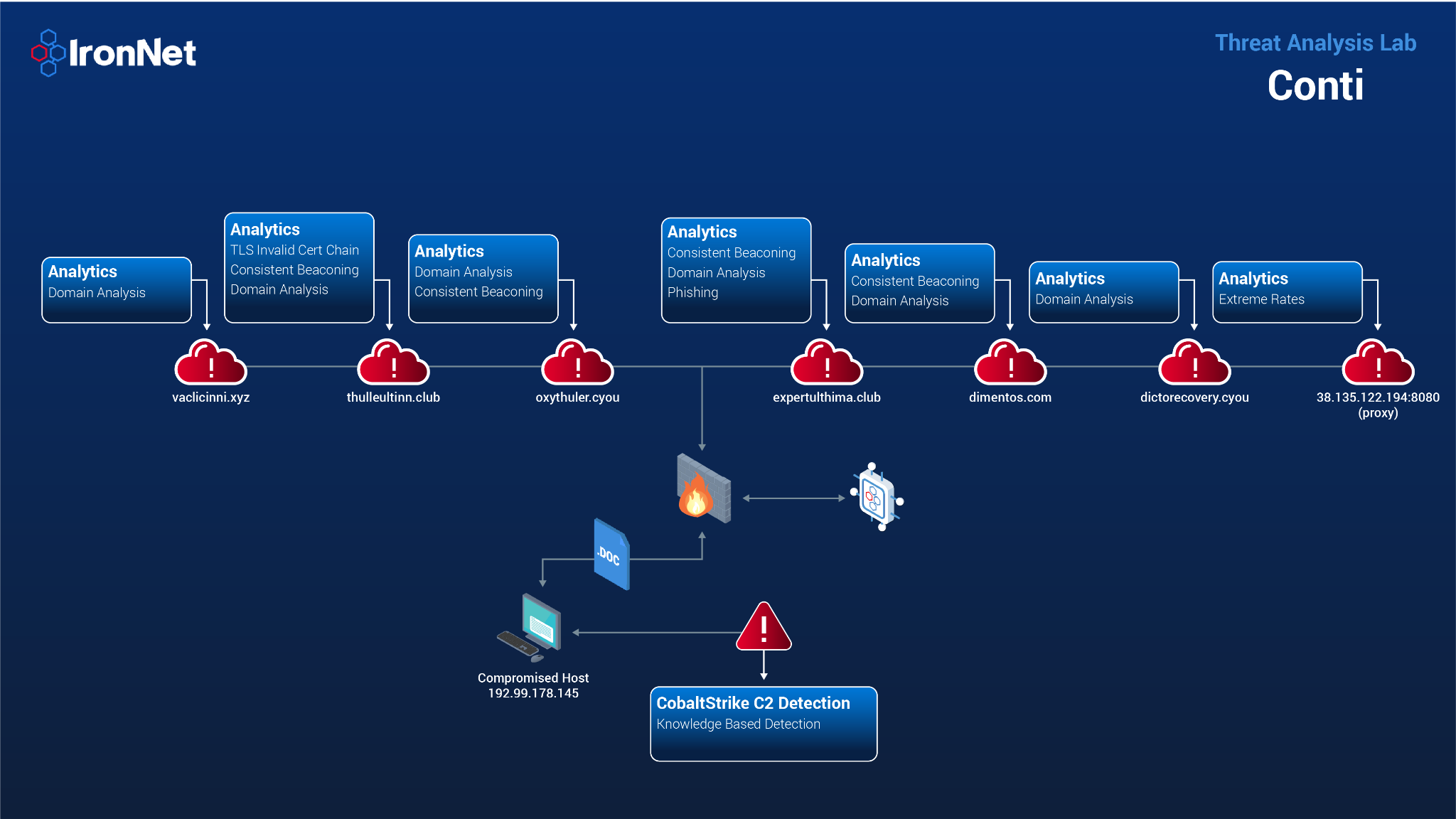
How IronNet's Behavioral Analytics Detect REvil and Conti Ransomware
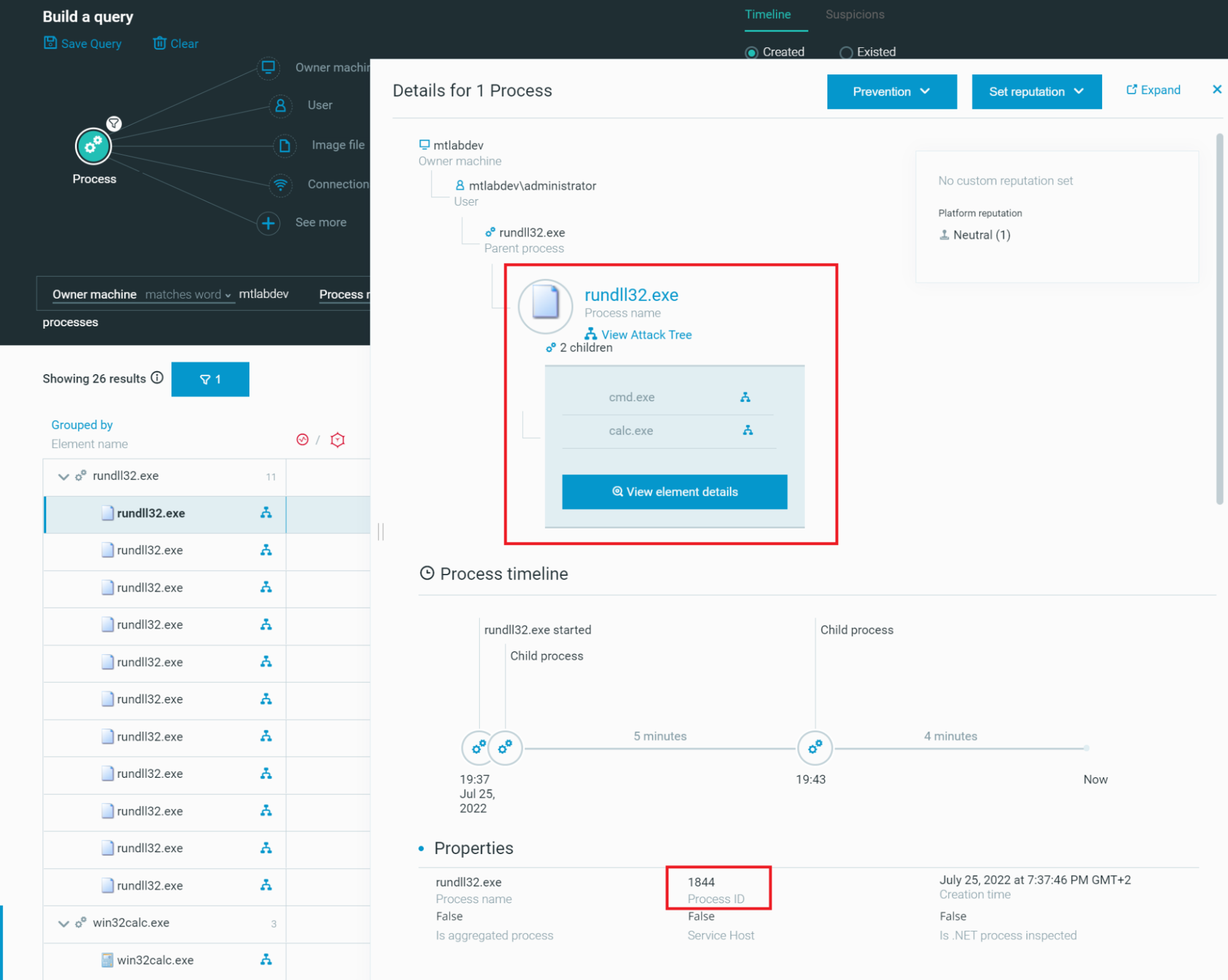
Rundll32: The Infamous Proxy for Executing Malicious Code

Rundll32: The Infamous Proxy for Executing Malicious Code
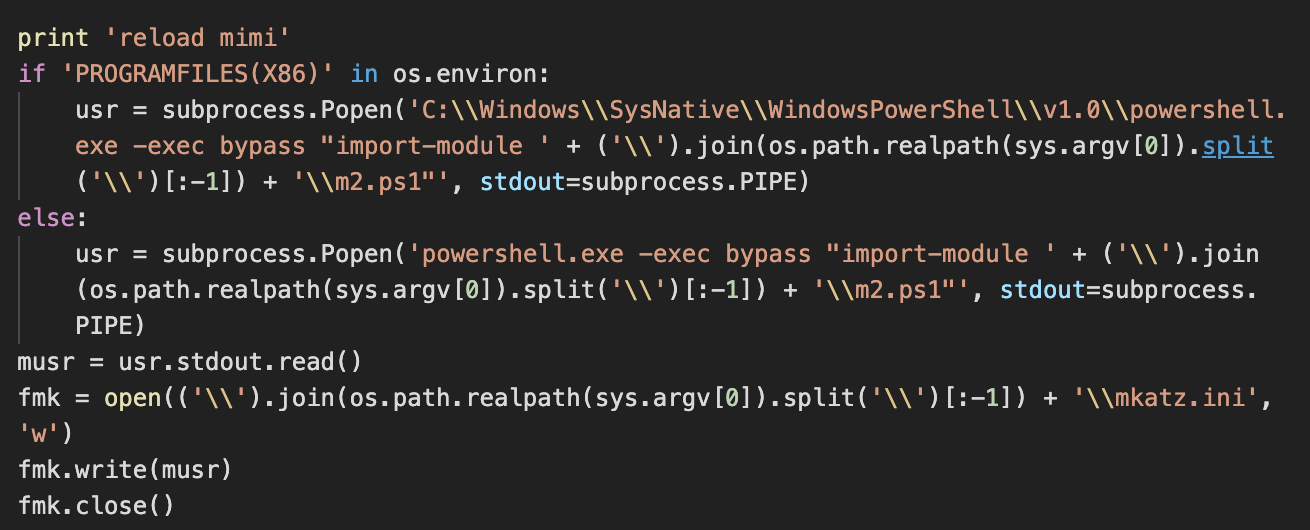
Lemon Duck brings cryptocurrency miners back into the spotlight

Microsoft experts linked Raspberry Robin malware to Evil Corp
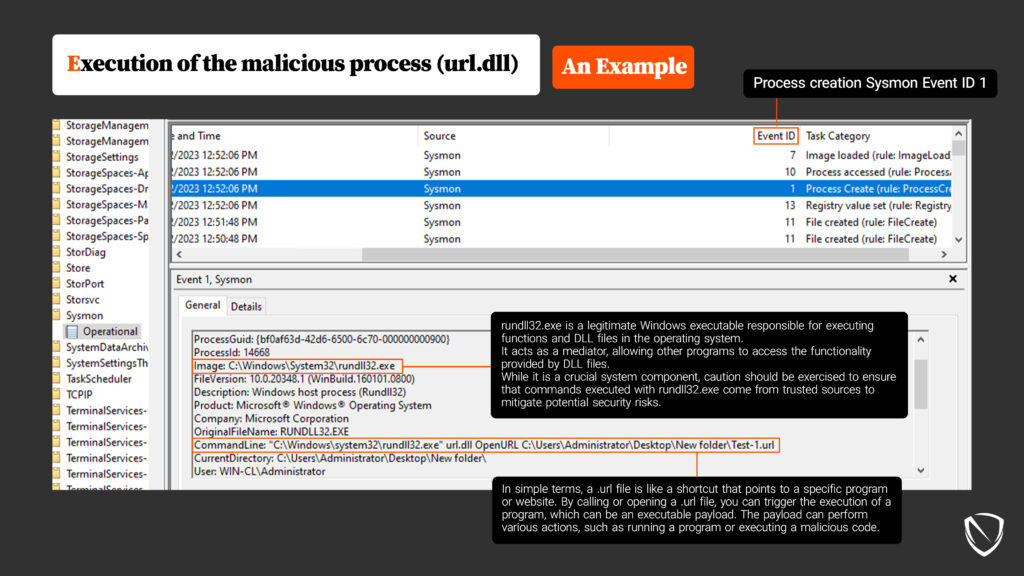
System Binary Proxy Execution Rundll32, Nordic Defender

Microsoft and FireEye Reveal New Malware Samples Tied to SolarWinds Attackers - SOC Prime

Hackers use a new technique in malspam campaigns to disable Macro security warnings in weaponized docs
Threat Intelligence Report
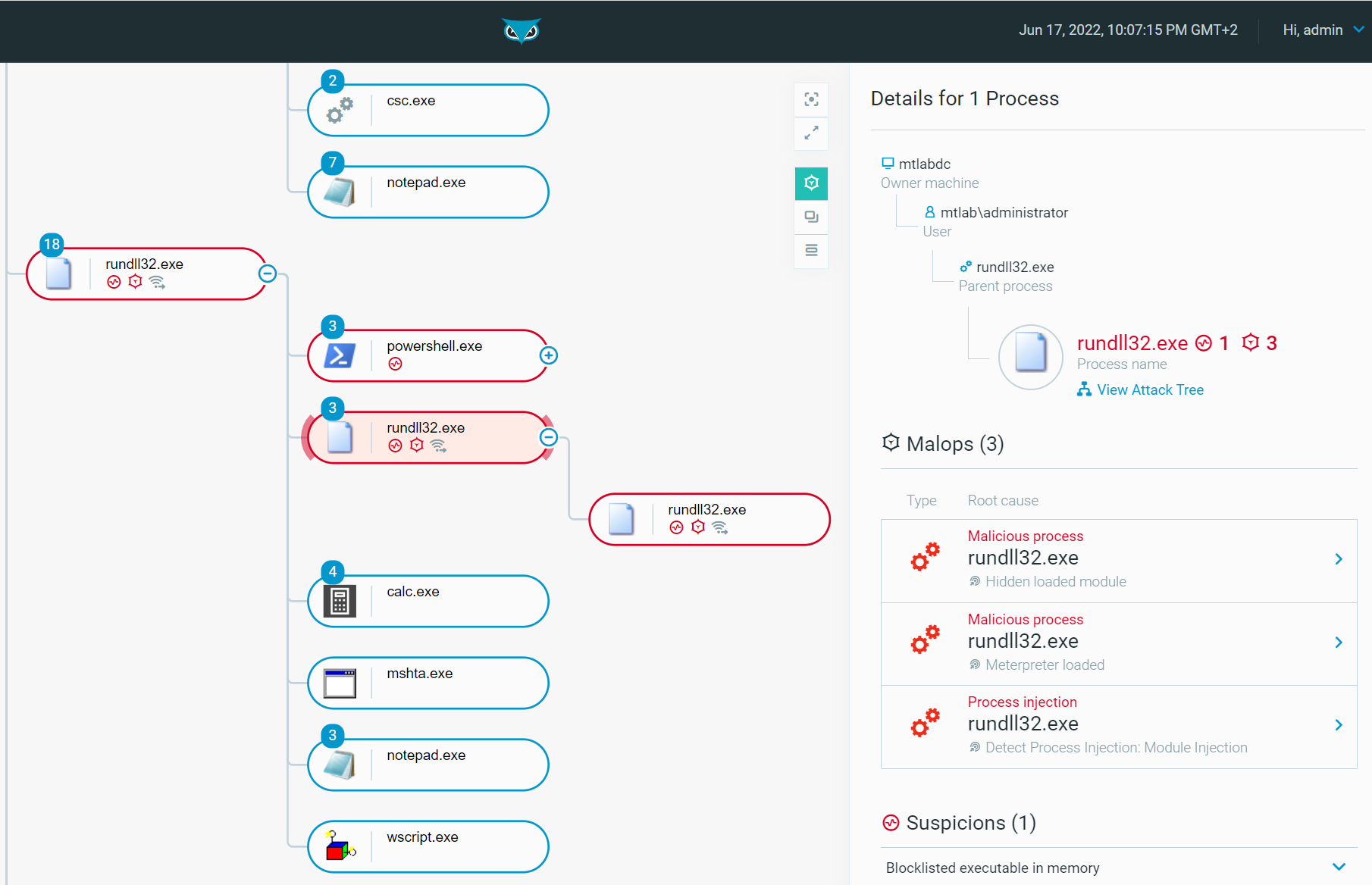
Rundll32: The Infamous Proxy for Executing Malicious Code
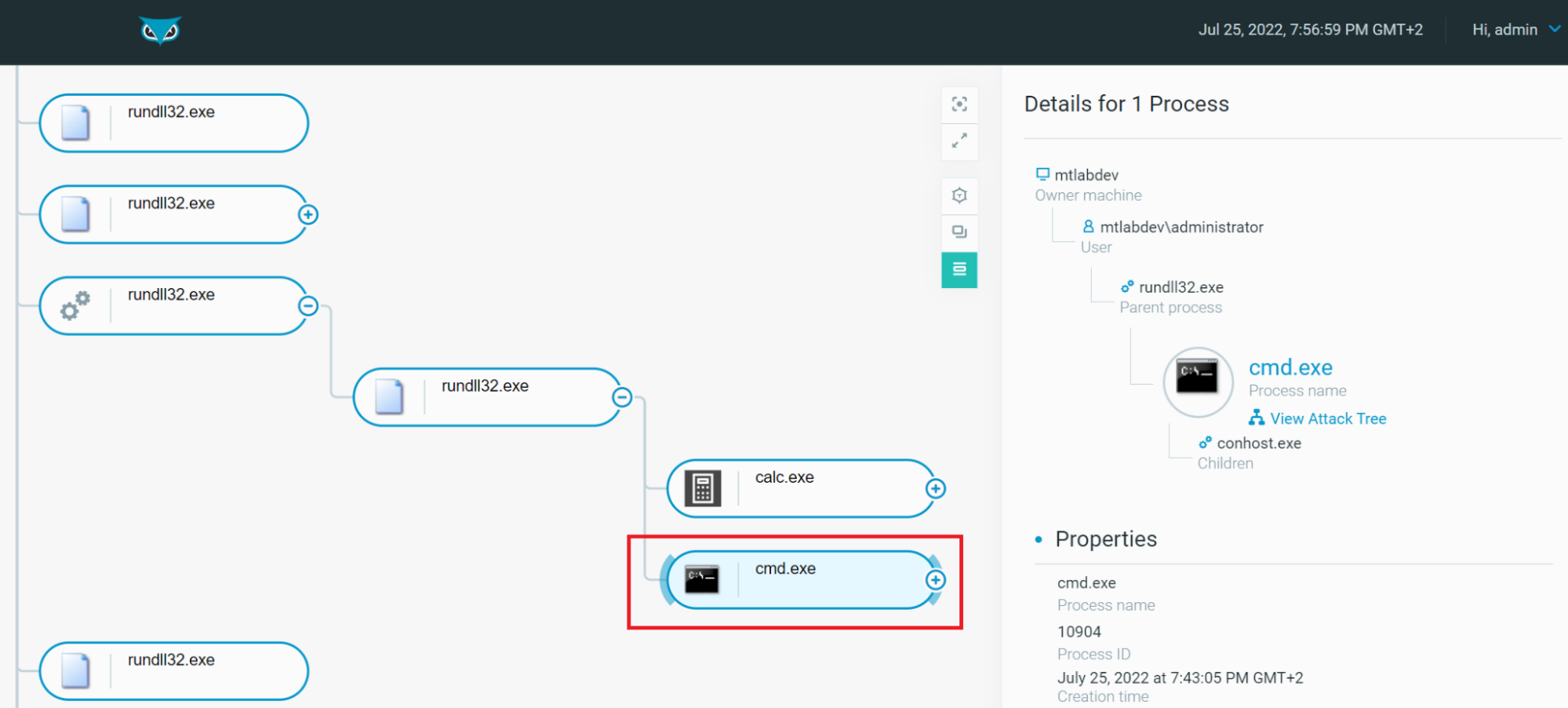
Rundll32: The Infamous Proxy for Executing Malicious Code
Recomendado para você
-
 Executing Command Prompt commands in SSIS – SQL Server Rider26 fevereiro 2025
Executing Command Prompt commands in SSIS – SQL Server Rider26 fevereiro 2025 -
 Command line switches for Outlook 365, 2021, 2019, 2016, 2013, and previous - HowTo-Outlook26 fevereiro 2025
Command line switches for Outlook 365, 2021, 2019, 2016, 2013, and previous - HowTo-Outlook26 fevereiro 2025 -
 How do I use Command Line Options in PBRS?26 fevereiro 2025
How do I use Command Line Options in PBRS?26 fevereiro 2025 -
 Silently Install EXE and MSI setup applications (Unattended) - How26 fevereiro 2025
Silently Install EXE and MSI setup applications (Unattended) - How26 fevereiro 2025 -
 Getting command line arguments in a Unity executable26 fevereiro 2025
Getting command line arguments in a Unity executable26 fevereiro 2025 -
Invalid argument when executing Windows commands on Ubuntu 20.0426 fevereiro 2025
-
 System Exec - not possible to recognize program or batch file26 fevereiro 2025
System Exec - not possible to recognize program or batch file26 fevereiro 2025 -
 The Visual Studio Code command-line interface26 fevereiro 2025
The Visual Studio Code command-line interface26 fevereiro 2025 -
 executable - How can I find out if an .EXE has Command-Line26 fevereiro 2025
executable - How can I find out if an .EXE has Command-Line26 fevereiro 2025 -
 command line - Passing parameters to SSIS Execute process task26 fevereiro 2025
command line - Passing parameters to SSIS Execute process task26 fevereiro 2025
você pode gostar
-
 Anime Dubs on X: The English Dub Episodes 232-255 for Boruto: Naruto Next Generation The Funato War Arc have launched today, November 14th, via Blu-ray/DVD and Digitally by @VizMedia. : Viz26 fevereiro 2025
Anime Dubs on X: The English Dub Episodes 232-255 for Boruto: Naruto Next Generation The Funato War Arc have launched today, November 14th, via Blu-ray/DVD and Digitally by @VizMedia. : Viz26 fevereiro 2025 -
 Karasuno Vs Wakunan Haikyuu!! Season 2 Episode 18 Reaction & Review!26 fevereiro 2025
Karasuno Vs Wakunan Haikyuu!! Season 2 Episode 18 Reaction & Review!26 fevereiro 2025 -
Pedro Espinosa no LinkedIn: Ambição pelo trabalho! Agradeço todos os dias pelas oportunidades! Que…26 fevereiro 2025
-
 Buy Microsoft Flight Simulator: Premium Deluxe PC Steam key! Cheap price26 fevereiro 2025
Buy Microsoft Flight Simulator: Premium Deluxe PC Steam key! Cheap price26 fevereiro 2025 -
 Zelda Breath Of The Wild 2 - 7 Features that may improve Legend of Zelda sequel - Daily Star26 fevereiro 2025
Zelda Breath Of The Wild 2 - 7 Features that may improve Legend of Zelda sequel - Daily Star26 fevereiro 2025 -
Fide Candidate's 2022 ⭐ 📸 FIDE / Stev Bonhage @stevbonhage @fide_chess # FIDE #fidecandidates2022 #candidates #Chess #chessnews26 fevereiro 2025
-
 Invisible Fruit / Suke Suke no Mi (Shiryu of the Rain) - One Piece Episode 91726 fevereiro 2025
Invisible Fruit / Suke Suke no Mi (Shiryu of the Rain) - One Piece Episode 91726 fevereiro 2025 -
 Gian Lawrence “The Black Stonefly” shares his passion for fishing, hunting, and community, by The Washington Department of Fish and Wildlife26 fevereiro 2025
Gian Lawrence “The Black Stonefly” shares his passion for fishing, hunting, and community, by The Washington Department of Fish and Wildlife26 fevereiro 2025 -
 Deadpool 2 – Wikipédia, a enciclopédia livre26 fevereiro 2025
Deadpool 2 – Wikipédia, a enciclopédia livre26 fevereiro 2025 -
 Vegeta Posters for Sale (Page #3 of 25) - Fine Art America26 fevereiro 2025
Vegeta Posters for Sale (Page #3 of 25) - Fine Art America26 fevereiro 2025

