Ransomware: Build Your Own Ransomware, Part 1
Por um escritor misterioso
Last updated 11 fevereiro 2025

Welcome back, my aspiring cyberwarriors! Ransomware is rapidly becoming the most important form of malware afflicting our digital systems. Companies across the globe are being hit with various forms of malware including the new variant, Snake, designed specifically for SCADA/ICS systems. The Colonial Pipeline in the US was shutdown for nearly a week before paying a $5 million ransom, demonstrating the danger of this ransomware to industrial systems and a nation

Shifr RaaS lets create a simple ransomware with just 3 steps

Evergreen//One Offers the 1st STaaS Ransomware Recovery SLA

What is ransomware-as-a-service (RaaS)?

Ransomware + Data Leak Extortion: Origins and Adversaries, Pt. 1
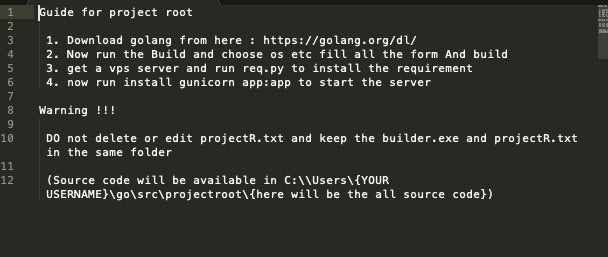
Build Your Own Ransomware (Project Root) Behind Enemy Lines Part 2 - SentinelOne
What Is Ransomware? - Cisco

Ransomware: Publicly Reported Incidents are only the tip of the iceberg — ENISA

Ransomware: Build Your Own Ransomware, Part 1

Blueprint for Ransomware Defense
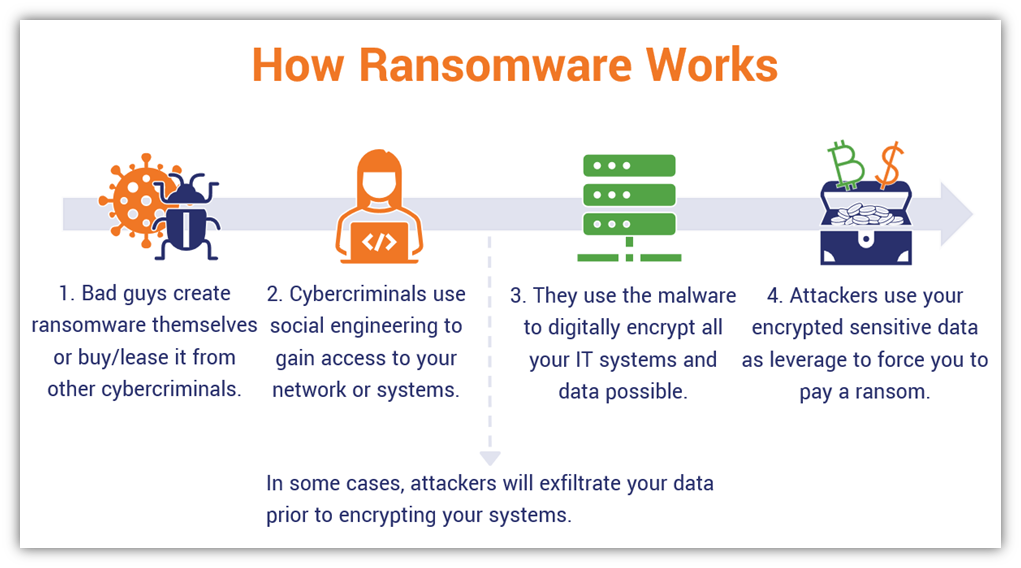
What Is Ransomware & How Does Ransomware Work? - Hashed Out by The SSL Store™
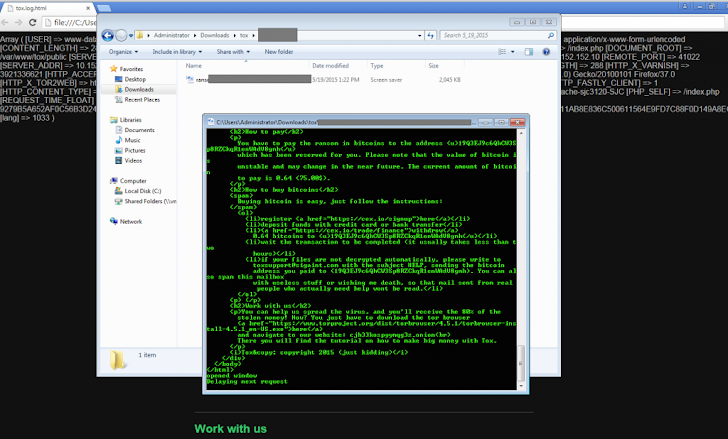
Tox' Offers Free build-your-own Ransomware Malware Toolkit
Ransomware is on the rise – here's how you can prepare – Middle East & Africa News Center

What Is Ransomware? Attack Types, Examples, Detection, and Prevention

How to Defend Against Cloud-based Ransomware Attacks - C Solutions IT

18 Examples of Ransomware Attacks - Updated 2022 - Tessian
Recomendado para você
-
 8 Best Google Snake Game Mods You Can Use (2022)11 fevereiro 2025
8 Best Google Snake Game Mods You Can Use (2022)11 fevereiro 2025 -
 Get Google Snake Game Menu Mod - (July, 2022) - FREE11 fevereiro 2025
Get Google Snake Game Menu Mod - (July, 2022) - FREE11 fevereiro 2025 -
.jpg) Google Snake Mods: Use Mods for Snake Games?11 fevereiro 2025
Google Snake Mods: Use Mods for Snake Games?11 fevereiro 2025 -
 Snake Game Using Tkinter - Python - GeeksforGeeks11 fevereiro 2025
Snake Game Using Tkinter - Python - GeeksforGeeks11 fevereiro 2025 -
.png) Create a Snake Game in React - GeeksforGeeks11 fevereiro 2025
Create a Snake Game in React - GeeksforGeeks11 fevereiro 2025 -
 Google Snake Mods: Add Github Mode (2023)11 fevereiro 2025
Google Snake Mods: Add Github Mode (2023)11 fevereiro 2025 -
I enhanced your snake game · Issue #3 · jakesgordon/javascript-snakes · GitHub11 fevereiro 2025
-
 Fitting Snake Into A QR Code11 fevereiro 2025
Fitting Snake Into A QR Code11 fevereiro 2025 -
 9 Best Cool Google Snake Game Mods You Should Try11 fevereiro 2025
9 Best Cool Google Snake Game Mods You Should Try11 fevereiro 2025 -
 How to Mod Google Snake Game 2023? How to Get Mod for Google Snake Game11 fevereiro 2025
How to Mod Google Snake Game 2023? How to Get Mod for Google Snake Game11 fevereiro 2025
você pode gostar
-
/i.s3.glbimg.com/v1/AUTH_da025474c0c44edd99332dddb09cabe8/internal_photos/bs/2022/E/U/U1U9B4T2muYTLESZV2cA/conjunto-roupa-nova.jpg) Roupa Nova comemora quatro décadas em shows no Rio11 fevereiro 2025
Roupa Nova comemora quatro décadas em shows no Rio11 fevereiro 2025 -
 Red Dead Redemption 2 - Versão PC Análise - Gamereactor11 fevereiro 2025
Red Dead Redemption 2 - Versão PC Análise - Gamereactor11 fevereiro 2025 -
 Tell Me Why - Taylor Swift Song Art Print for Sale by bombalurina11 fevereiro 2025
Tell Me Why - Taylor Swift Song Art Print for Sale by bombalurina11 fevereiro 2025 -
 fredbear ucn Memes & GIFs - Imgflip11 fevereiro 2025
fredbear ucn Memes & GIFs - Imgflip11 fevereiro 2025 -
 Tata Steel Chess 2019 poised for a spectacular start with likes of Viswanathan Anand and Magnus Carlsen in fray-Sports News , Firstpost11 fevereiro 2025
Tata Steel Chess 2019 poised for a spectacular start with likes of Viswanathan Anand and Magnus Carlsen in fray-Sports News , Firstpost11 fevereiro 2025 -
Kurnik Ocieplony - Niska cena na11 fevereiro 2025
-
 Download Earth Mobs Mod for Minecraft 1.16.4/1.14.411 fevereiro 2025
Download Earth Mobs Mod for Minecraft 1.16.4/1.14.411 fevereiro 2025 -
 Cross Ange 25 END11 fevereiro 2025
Cross Ange 25 END11 fevereiro 2025 -
Links Apks11 fevereiro 2025
-
Viejo Pastor Ingles de México11 fevereiro 2025

