— Proton Exploit
Por um escritor misterioso
Last updated 23 maio 2024
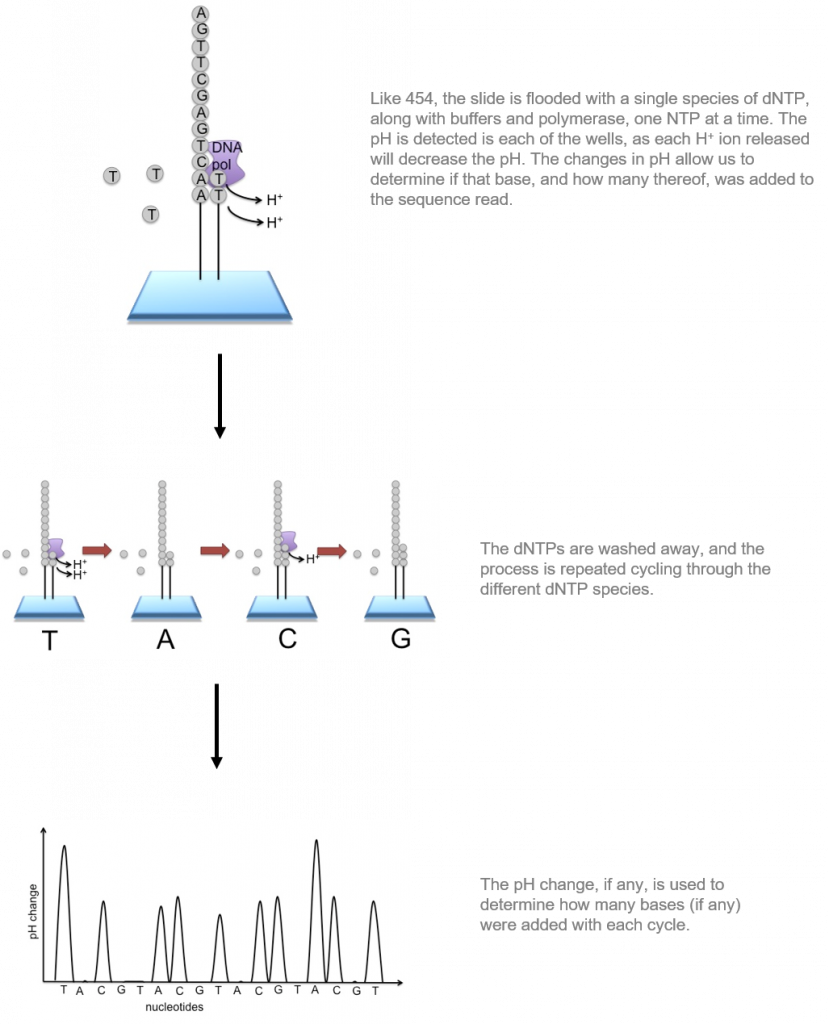
Ion Torrent: Proton / PGM sequencing
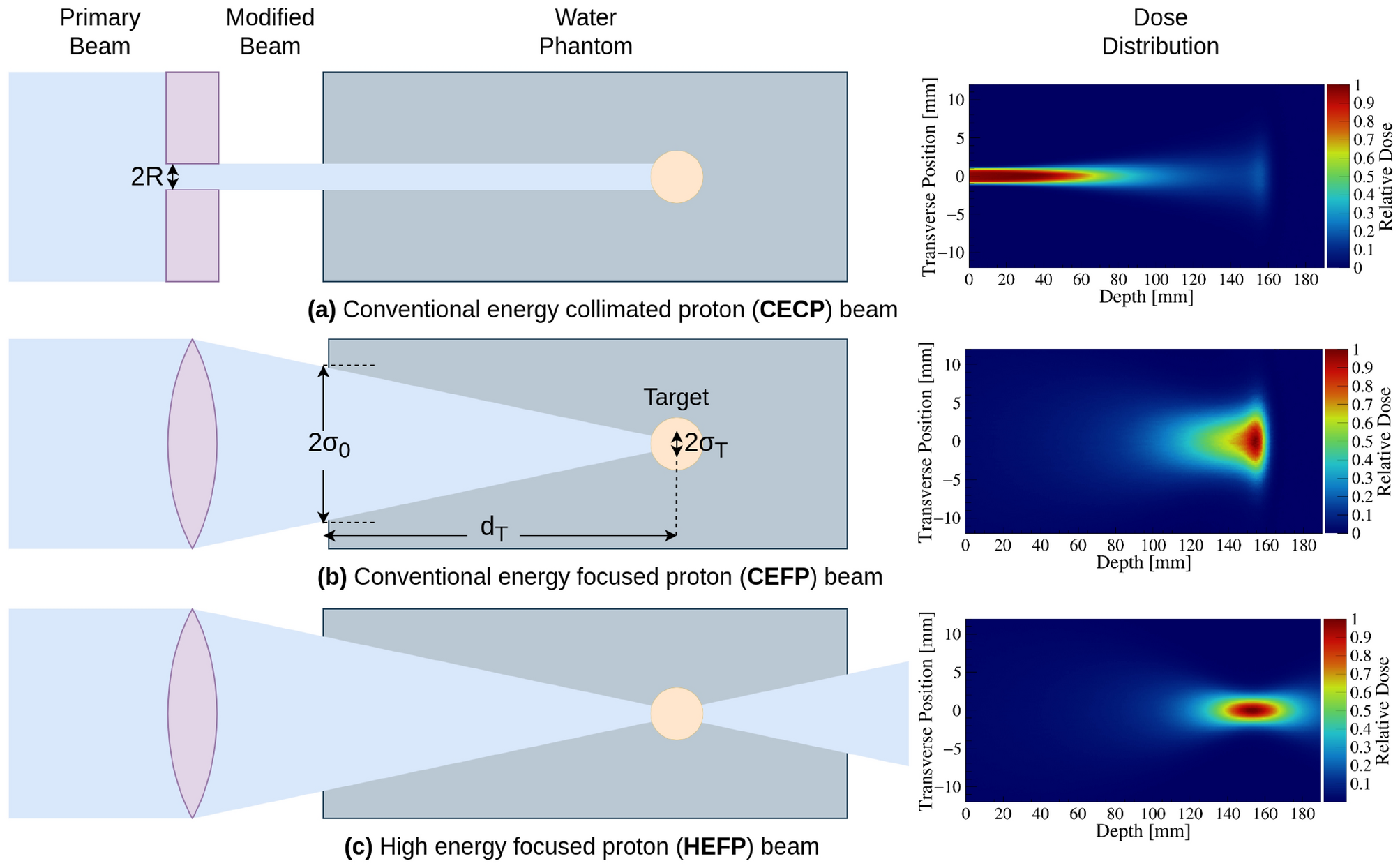
Sharp dose profiles for high precision proton therapy using strongly focused proton beams

Proton Hyperpolarization Relay from Nanocrystals to Liquid Water

Cascaded Excited‐State Intramolecular Proton Transfer Towards Near‐Infrared Organic Lasers Beyond 850 nm - Wu - 2021 - Angewandte Chemie International Edition - Wiley Online Library

WannaCry - Important lessons from the first NSA-powered ransomware cyberattack

Exploit Kit (EK) - Security Intelligence

Code Vulnerabilities Put Proton Mails at Risk

WinRAR Vulnerability Puts Illicit Content Consumers at Risk of Apanyan Stealer, Murk-Stealer & AsyncRAT — Cyble
Will on X: 🔎 Somewhat interesting software pirating site enesoftware[.]com that targets other cybercriminals too, offering builders & panels for sought after #malware like MarsStealer, Anubis, and Alien Actor: uhogiwubi5 (enesoftware[.]com/writer

a) Pulse sequence utilized for the SMT experiment, involving long (800

De-Anonymization attacks against Proton services

— Proton Exploit

What is a zero-day exploit and why are they dangerous? - Proton VPN Blog
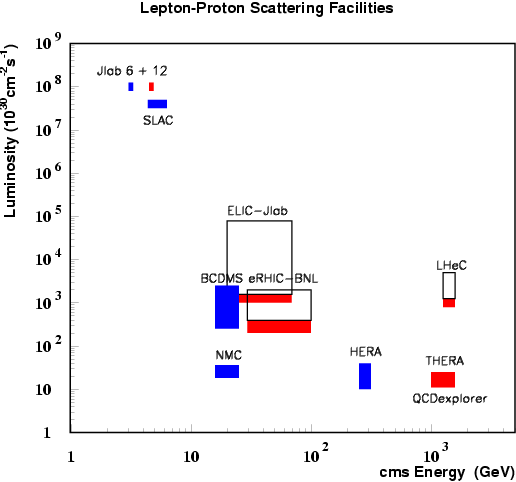
accelep.png
Recomendado para você
-
 jjsploit queries - WRD Community23 maio 2024
jjsploit queries - WRD Community23 maio 2024 -
Roblox Free Executor 202223 maio 2024
-
 ELECTRON ON FRONT PAGE YAYAYAYAY - WRD Community23 maio 2024
ELECTRON ON FRONT PAGE YAYAYAYAY - WRD Community23 maio 2024 -
Replying to @eli tut on how to install fluxus23 maio 2024
-
electron executor|TikTok Search23 maio 2024
-
 After downloading these 3 exploits and writing a review on them, my PC started acting weird. It was slowing down, my FPS in roblox was dipping, and the performance became extremely slow23 maio 2024
After downloading these 3 exploits and writing a review on them, my PC started acting weird. It was slowing down, my FPS in roblox was dipping, and the performance became extremely slow23 maio 2024 -
 WeAreDevelopers World Congress23 maio 2024
WeAreDevelopers World Congress23 maio 2024 -
 ChloeGarcia (@ChloeGarciaYT) / X23 maio 2024
ChloeGarcia (@ChloeGarciaYT) / X23 maio 2024 -
 Igigi shopper's assistant – SerbianTech23 maio 2024
Igigi shopper's assistant – SerbianTech23 maio 2024 -
Mohsen Esmailpour on LinkedIn: #developer #developerlife #github #chatgpt #stackoverflow #23 maio 2024
você pode gostar
-
 Feliz Boruto para colorir23 maio 2024
Feliz Boruto para colorir23 maio 2024 -
 Fuuto Tantei Dublado - Episódio 11 - Animes Online23 maio 2024
Fuuto Tantei Dublado - Episódio 11 - Animes Online23 maio 2024 -
 Desenho de Kakashi e Naruto para colorir - Tudodesenhos23 maio 2024
Desenho de Kakashi e Naruto para colorir - Tudodesenhos23 maio 2024 -
os povo tá com muita inveja no Roblox aí agr mim denunciaram 😫😫😫23 maio 2024
-
 Screenshot Archive: Street Fighter Alpha 323 maio 2024
Screenshot Archive: Street Fighter Alpha 323 maio 2024 -
 Marca de cerveja promoverá final da Champions League e tira23 maio 2024
Marca de cerveja promoverá final da Champions League e tira23 maio 2024 -
 10 dicas de jogo para God of War Ragnarök: Níveis de Poder, Trabalhos de Habilidade, Bônus de Conjuntos de Armadura e mais – PlayStation.Blog BR23 maio 2024
10 dicas de jogo para God of War Ragnarök: Níveis de Poder, Trabalhos de Habilidade, Bônus de Conjuntos de Armadura e mais – PlayStation.Blog BR23 maio 2024 -
 Read Goddess Café Terrace Chapter 89: Departure - Manganelo23 maio 2024
Read Goddess Café Terrace Chapter 89: Departure - Manganelo23 maio 2024 -
 25 projetos de banheiros escuros para se inspirar - Revestindo a Casa23 maio 2024
25 projetos de banheiros escuros para se inspirar - Revestindo a Casa23 maio 2024 -
 Novo Jogo de Caminhão Brasileiro para PC+Download23 maio 2024
Novo Jogo de Caminhão Brasileiro para PC+Download23 maio 2024



