Phishing Analysis. Ojectives Phishing Internet Protocol (IP) addresses Domain Name System (DNS) names Analyse “From” addresses Analyse URL's Trace the. - ppt download
Por um escritor misterioso
Last updated 30 janeiro 2025
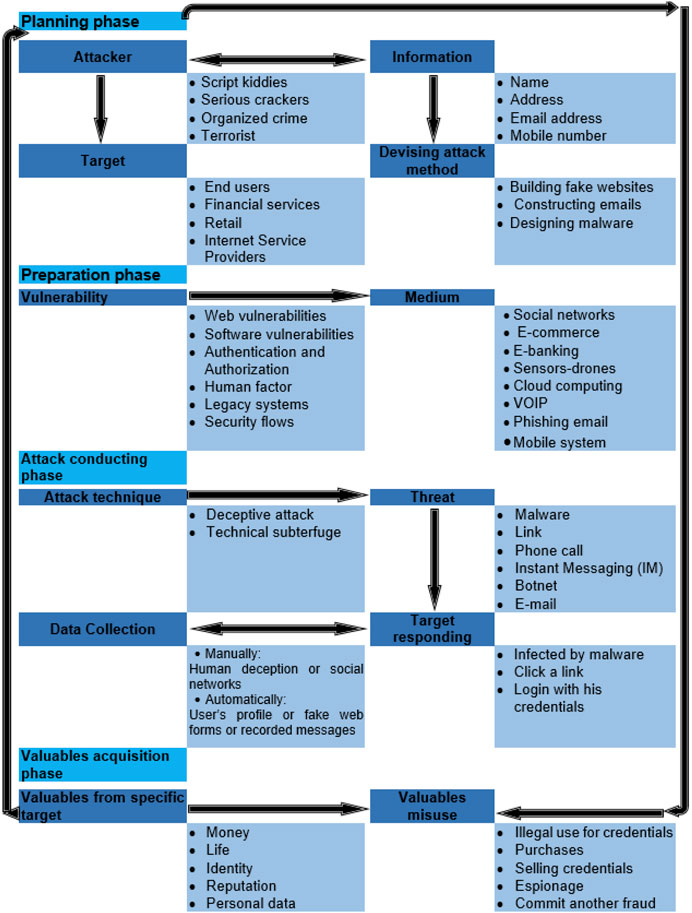
Phishing utilizing social engineering Induces the recipient to reveal desired personal information Bank account SSN Address Etc. Sometimes entices the recipient to go to a malicious web site
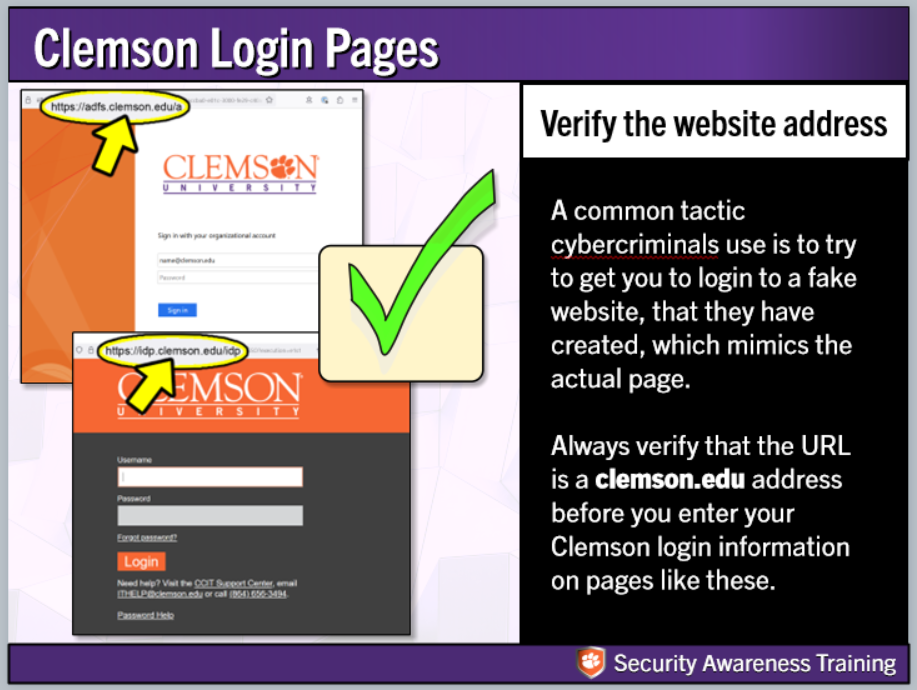
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the
Summary IANA assigns IP addresses Regional Registries assign addresses for regions Start with ARIN when researching –ARIN will tell you where to go for non- American addresses Turn on long headers in Don t fall for silly stuff in the body of the

6 Common Phishing Attacks and How to Protect Against Them

Web Filtering Blog

What is Data Exfiltration and How Can You Prevent It?

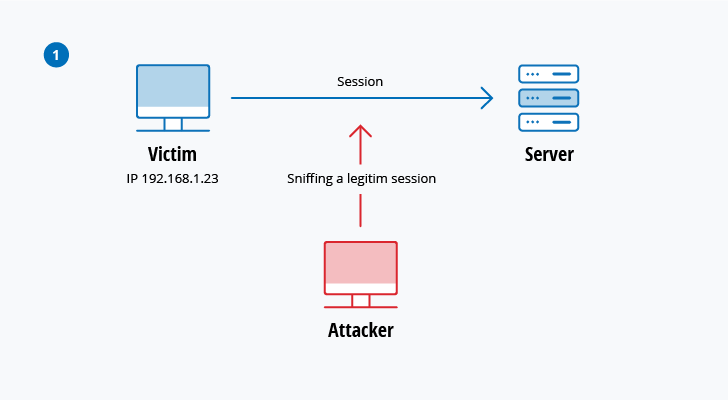
DNS Advanced Attacks and Analysis

Denial-of-service attack - Wikipedia

Page 2 – Hornetsecurity – Cloud Security Services for Businesses

Phishing Attacks And Strategies To Mitigate Them Powerpoint
Frontiers Phishing Attacks: A Recent Comprehensive Study and a

CSC586 Network Forensics IP Tracing/Domain Name Tracing. - ppt
Cybersecurity Alerts
The 12 Most Common Types of Cybersecurity Attacks Today
Recomendado para você
-
After exchanging my SWITCH to a ROUTER, I… - Apple Community30 janeiro 2025
-
 CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center30 janeiro 2025
CloudConnexa: Connected WPC User and Host Connector Egress to DigitalOcean Network Connector Use Cases – OpenVPN Support Center30 janeiro 2025 -
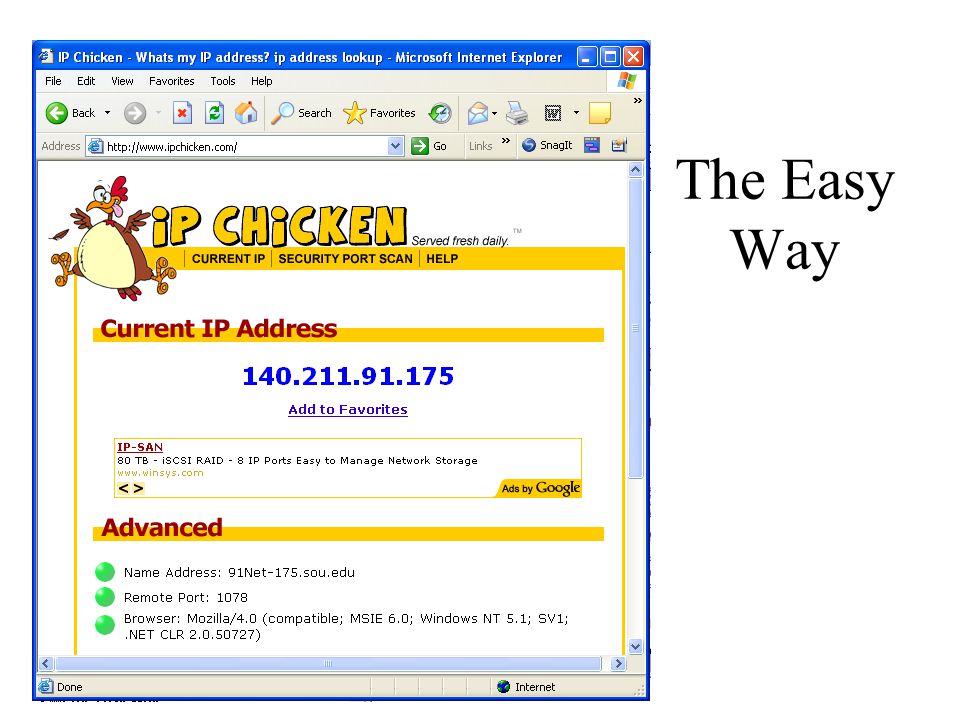
 IP Chicken - What is my IP address Free public IP lookup30 janeiro 2025
IP Chicken - What is my IP address Free public IP lookup30 janeiro 2025 -
 Block ads on all your devices using pfSense, Squid & SquidGuard30 janeiro 2025
Block ads on all your devices using pfSense, Squid & SquidGuard30 janeiro 2025 -
 8 Sites That Show Your IP Address –30 janeiro 2025
8 Sites That Show Your IP Address –30 janeiro 2025 -
 chicken Memes & GIFs - Imgflip30 janeiro 2025
chicken Memes & GIFs - Imgflip30 janeiro 2025 -
 Anonymous Security Scanning and Browsing30 janeiro 2025
Anonymous Security Scanning and Browsing30 janeiro 2025 -
 What is port scanning and how does it work?30 janeiro 2025
What is port scanning and how does it work?30 janeiro 2025 -
 Port Scanner - an overview30 janeiro 2025
Port Scanner - an overview30 janeiro 2025 -
 What is Tor Browser & How to Setup Tor30 janeiro 2025
What is Tor Browser & How to Setup Tor30 janeiro 2025
você pode gostar
-
 GoldenEye: Rogue Agent Multiplayer Hands-On - GameSpot30 janeiro 2025
GoldenEye: Rogue Agent Multiplayer Hands-On - GameSpot30 janeiro 2025 -
 Fruits Basket (2019) S2 Episode 230 janeiro 2025
Fruits Basket (2019) S2 Episode 230 janeiro 2025 -
 40 Best Games Like Wordle That Are Equally Challenging30 janeiro 2025
40 Best Games Like Wordle That Are Equally Challenging30 janeiro 2025 -
 Pokemon Generation III Checklists - Pokedex Checklist - POKÉDEX30 janeiro 2025
Pokemon Generation III Checklists - Pokedex Checklist - POKÉDEX30 janeiro 2025 -
 Details about Satou Kazuma Cosplay Costume KonoSuba God's Blessing30 janeiro 2025
Details about Satou Kazuma Cosplay Costume KonoSuba God's Blessing30 janeiro 2025 -
 Dead Island 2 special edition, pre-order bonus detailed30 janeiro 2025
Dead Island 2 special edition, pre-order bonus detailed30 janeiro 2025 -
Casa da Matemática30 janeiro 2025
-
 Winning Moves of Igors Rausis30 janeiro 2025
Winning Moves of Igors Rausis30 janeiro 2025 -
 Hamburgueria River Burguer no Rio Vermelho30 janeiro 2025
Hamburgueria River Burguer no Rio Vermelho30 janeiro 2025 -
 Cadeira de Barbeiro Antiga Ferrante - Sanremo Magazine30 janeiro 2025
Cadeira de Barbeiro Antiga Ferrante - Sanremo Magazine30 janeiro 2025
