Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 15 fevereiro 2025

The Top 10 Malware Analysis Tools

How to Analyze Malware Infections?

Malware Analysis Framework v1.0
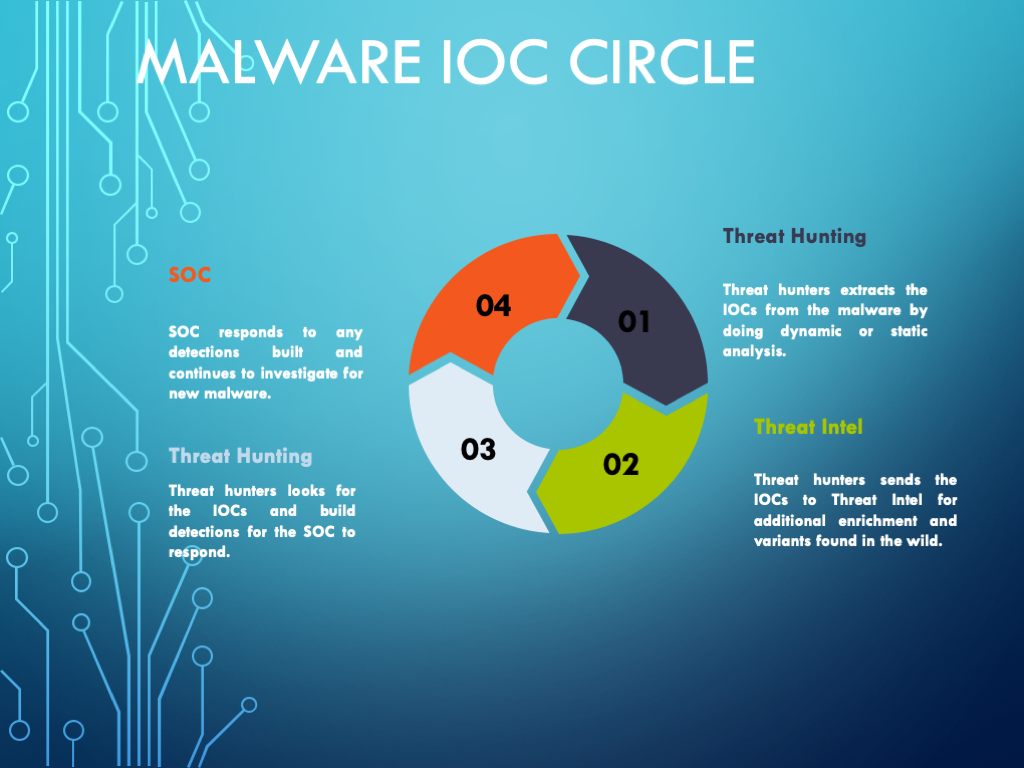
Malware Analysis Framework v1.0

Malware Analysis - What is, Benefits & Types (Easily Explained)

Behavioral blocking and containment: Transforming optics into
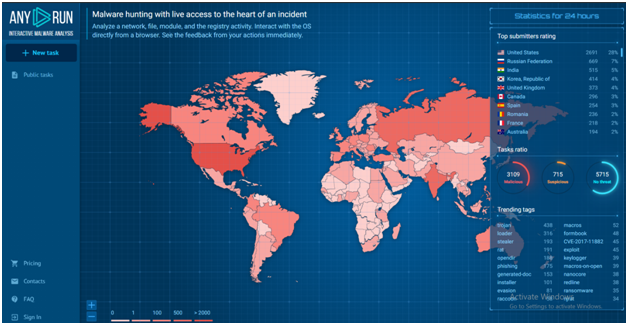
Free Automated Malware Analysis Sandboxes for Incident Response

A flow chart of malware detection approaches and features
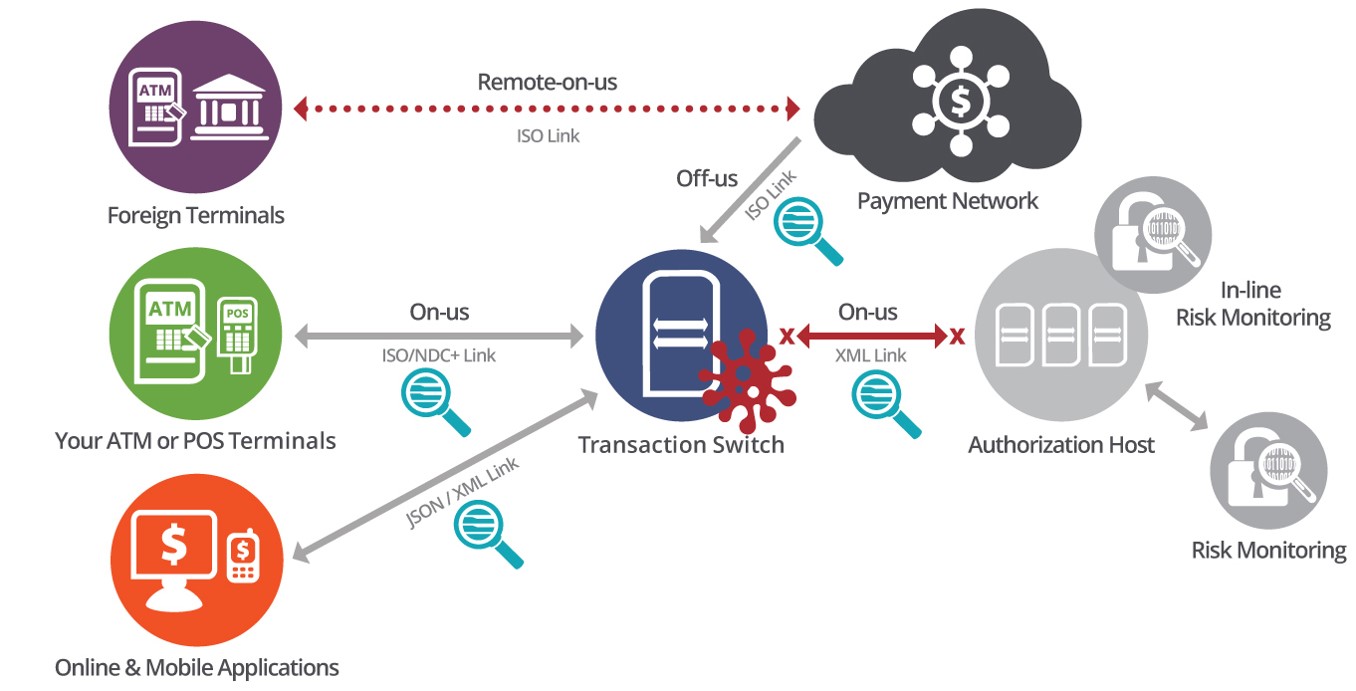
Malware Detection: One transaction at a time, INETCO Blog
How to Detect Running Malware - Intro to Incident Response Triage 2021

Unusual Activity Detection – Identifying and Flagging Security
Recomendado para você
-
 Play Roblox on PC - Download for Free at15 fevereiro 2025
Play Roblox on PC - Download for Free at15 fevereiro 2025 -
roblox-hack · GitHub Topics · GitHub15 fevereiro 2025
-
RoSploit (Roblox Exploit Hub) - Microsoft Apps15 fevereiro 2025
-
 ArtStation - Roblox Hack Mod APk 2.533.256 Download Artwork For Android 202215 fevereiro 2025
ArtStation - Roblox Hack Mod APk 2.533.256 Download Artwork For Android 202215 fevereiro 2025 -
 Master mod menu for roblox APK for Android Download15 fevereiro 2025
Master mod menu for roblox APK for Android Download15 fevereiro 2025 -
roblox-executor · GitHub Topics · GitHub15 fevereiro 2025
-
FREE ADMIN] - Roblox15 fevereiro 2025
-
 7 Hacks ideas roblox, roblox gifts, create an avatar15 fevereiro 2025
7 Hacks ideas roblox, roblox gifts, create an avatar15 fevereiro 2025 -
 Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link15 fevereiro 2025
Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link15 fevereiro 2025 -
 Electron x FREE Executor 2023, Roblox x Electron Script Menu15 fevereiro 2025
Electron x FREE Executor 2023, Roblox x Electron Script Menu15 fevereiro 2025
você pode gostar
-
Nintendo Switch – OLED Model Pokémon Scarlet & Violet Edition15 fevereiro 2025
-
 Arquivo BARBIE SEREIA – Fofurices Digitais15 fevereiro 2025
Arquivo BARBIE SEREIA – Fofurices Digitais15 fevereiro 2025 -
 Tanjiro Kamado (usually ver.)' Theatrical version of Demon Slayer: Kimetsu no Yaiba Mugen Train Series, Orchestra Concert, Oni-no-so, Drawing of Oni-no-so, Kabuki, Random metal badge', Goods / Accessories15 fevereiro 2025
Tanjiro Kamado (usually ver.)' Theatrical version of Demon Slayer: Kimetsu no Yaiba Mugen Train Series, Orchestra Concert, Oni-no-so, Drawing of Oni-no-so, Kabuki, Random metal badge', Goods / Accessories15 fevereiro 2025 -
 How To Draw Rainbow Friends Easy Blue15 fevereiro 2025
How To Draw Rainbow Friends Easy Blue15 fevereiro 2025 -
 Titanfall 2, Northstar15 fevereiro 2025
Titanfall 2, Northstar15 fevereiro 2025 -
 Como se diz “Bater na Mesma Tecla” em inglês?15 fevereiro 2025
Como se diz “Bater na Mesma Tecla” em inglês?15 fevereiro 2025 -
 Blue Lock ganha imagens do Episódio 1815 fevereiro 2025
Blue Lock ganha imagens do Episódio 1815 fevereiro 2025 -
Kanye West lyrics - Kanye West lyrics posted randomly15 fevereiro 2025
-
 Lua Scripts For Roblox Studio & Your Games15 fevereiro 2025
Lua Scripts For Roblox Studio & Your Games15 fevereiro 2025 -
 Kangaskhan EX Flashfire 103/106 Values - MAVIN15 fevereiro 2025
Kangaskhan EX Flashfire 103/106 Values - MAVIN15 fevereiro 2025

![FREE ADMIN] - Roblox](https://tr.rbxcdn.com/72fb2913d0ce11c89858adb553a37e80/500/280/Image/Jpeg)

