Malware analysis Malicious activity
Por um escritor misterioso
Last updated 28 fevereiro 2025
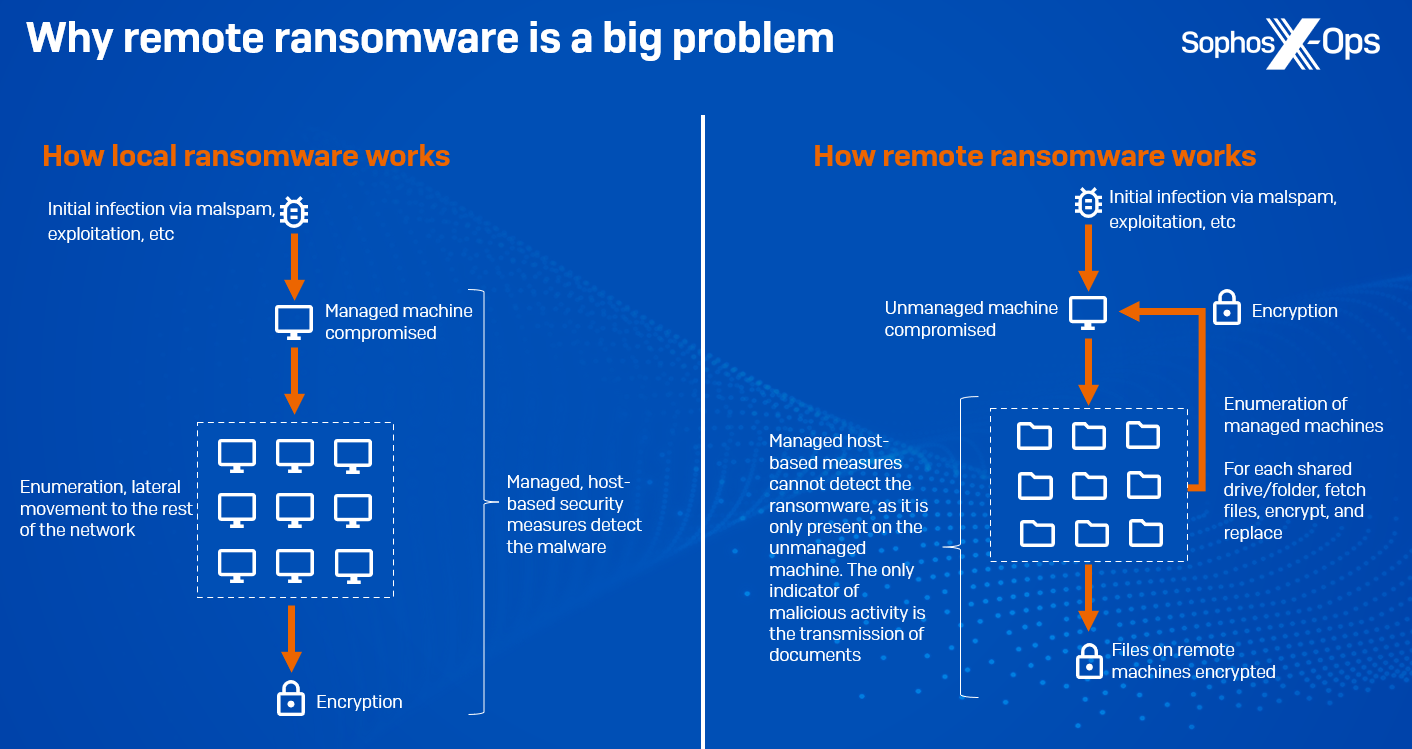
CryptoGuard: An asymmetric approach to the ransomware battle – Sophos News

Interactive Online Malware Sandbox

Malware Analysis: Steps & Examples - CrowdStrike

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

How to build a malware analysis sandbox with Elastic Security

How to Do Malware Analysis?

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks
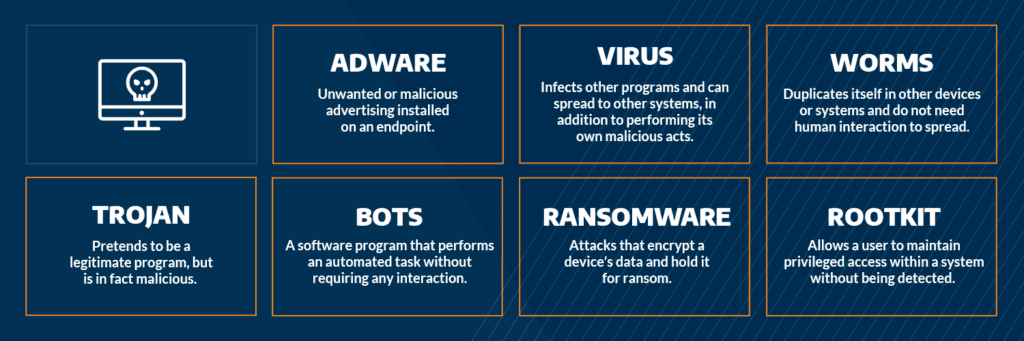
Most Common Malware Attacks

A detailed analysis of the Menorah malware used by APT34
Recomendado para você
-
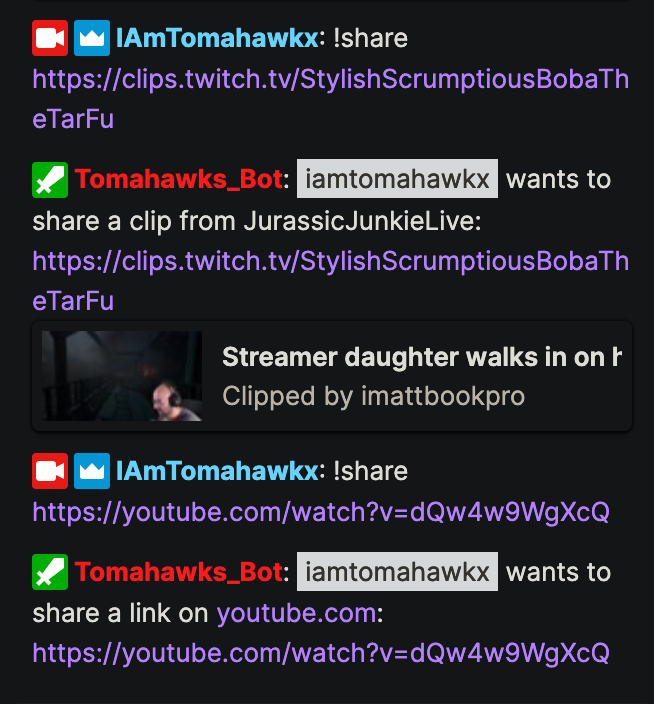 Commands Ext - TwitchIO 2.8.2 documentation28 fevereiro 2025
Commands Ext - TwitchIO 2.8.2 documentation28 fevereiro 2025 -
Morise.ai for (@MoriseAI) / X28 fevereiro 2025
-
 FriendsOfFlarum Formatting - Flarum Community28 fevereiro 2025
FriendsOfFlarum Formatting - Flarum Community28 fevereiro 2025 -
All posts by Wyatt poling28 fevereiro 2025
-
Use minified links when sharing video URL · Issue #1556 · TeamNewPipe/NewPipe · GitHub28 fevereiro 2025
-
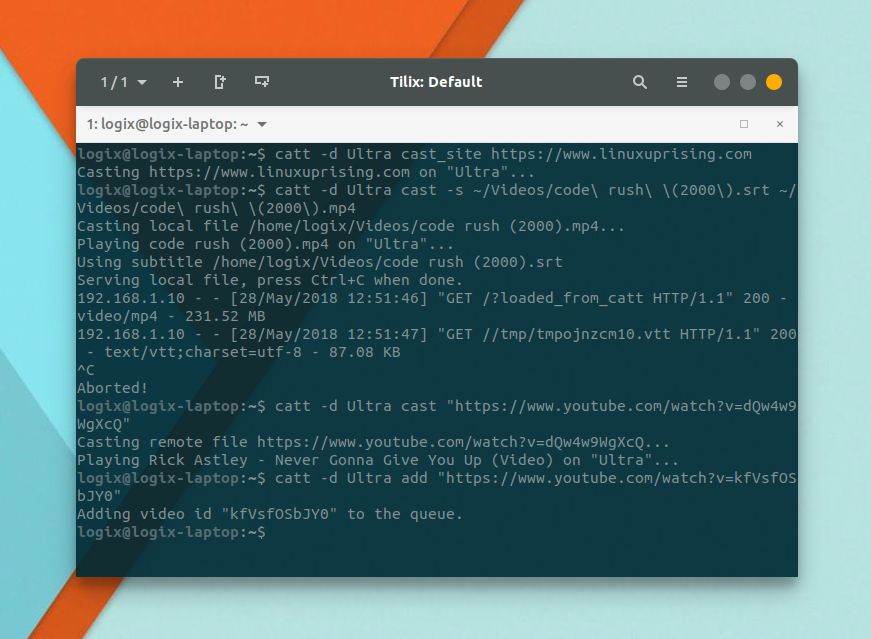 Command Line Chromecast Player CATT Gets Support For Subtitles And Website Casting - Linux Uprising Blog28 fevereiro 2025
Command Line Chromecast Player CATT Gets Support For Subtitles And Website Casting - Linux Uprising Blog28 fevereiro 2025 -
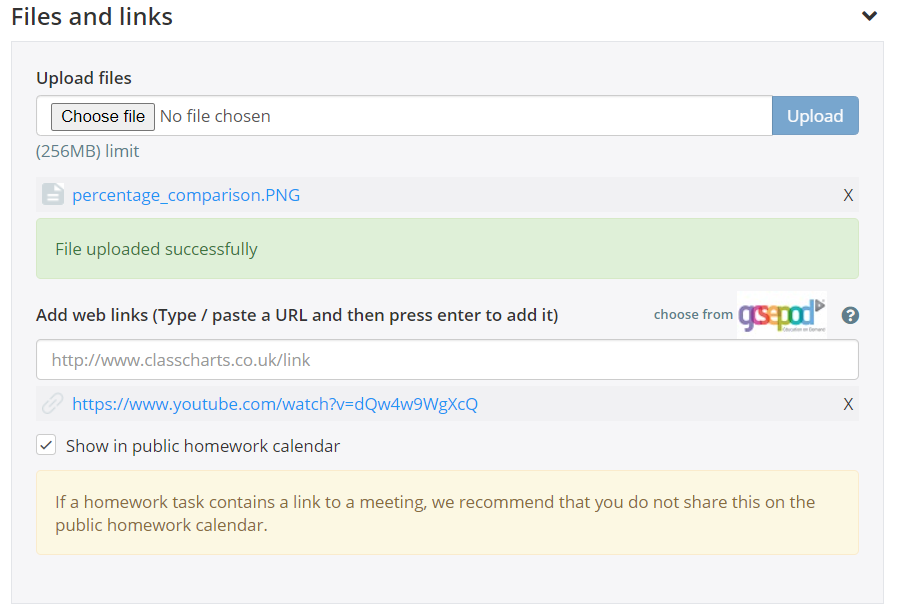 How to set a homework task - ClassCharts28 fevereiro 2025
How to set a homework task - ClassCharts28 fevereiro 2025 -
 Why SonarQube 9.9 LTS is a must-have for PHP Developers28 fevereiro 2025
Why SonarQube 9.9 LTS is a must-have for PHP Developers28 fevereiro 2025 -
 Ellipses, Three Dots, …, or Three Periods in Javascript — A Primer to the Spread Operator, by Daniel Wagener, The Startup28 fevereiro 2025
Ellipses, Three Dots, …, or Three Periods in Javascript — A Primer to the Spread Operator, by Daniel Wagener, The Startup28 fevereiro 2025 -
 javascript - How do I get the video ID from a URL? - Stack Overflow28 fevereiro 2025
javascript - How do I get the video ID from a URL? - Stack Overflow28 fevereiro 2025
você pode gostar
-
 Black lady side profile hi-res stock photography and images - Alamy28 fevereiro 2025
Black lady side profile hi-res stock photography and images - Alamy28 fevereiro 2025 -
 NEW Hilarious SUNKY GAME! - Sunky's SchoolHouse on Make a GIF28 fevereiro 2025
NEW Hilarious SUNKY GAME! - Sunky's SchoolHouse on Make a GIF28 fevereiro 2025 -
 Resident Evil 7, RE2, & RE3 remakes to get PS5 & Xbox Series X/S28 fevereiro 2025
Resident Evil 7, RE2, & RE3 remakes to get PS5 & Xbox Series X/S28 fevereiro 2025 -
3 to 5 Digit Addition and Subtraction Powerpoint Game by Teacher Gameroom28 fevereiro 2025
-
 Gru's foolproof plan - Imgflip28 fevereiro 2025
Gru's foolproof plan - Imgflip28 fevereiro 2025 -
 2° recomendaciones Anime recommendations, Anime suggestions28 fevereiro 2025
2° recomendaciones Anime recommendations, Anime suggestions28 fevereiro 2025 -
 Gucci hits runway as fashion world awaits new designer28 fevereiro 2025
Gucci hits runway as fashion world awaits new designer28 fevereiro 2025 -
 Folha de conceito de reviravolta de personagem fofa de anime kawaii chibi girl com roupas elegantes e modernas28 fevereiro 2025
Folha de conceito de reviravolta de personagem fofa de anime kawaii chibi girl com roupas elegantes e modernas28 fevereiro 2025 -
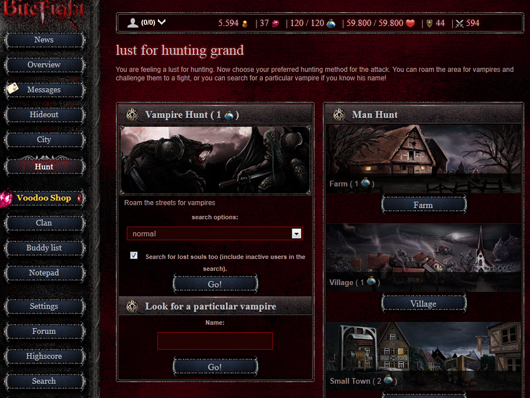 BiteFight - Multiuser - Online Games - Wow Davao City, Philippines28 fevereiro 2025
BiteFight - Multiuser - Online Games - Wow Davao City, Philippines28 fevereiro 2025 -
 12 Best Scary Roblox Horror Games in 202328 fevereiro 2025
12 Best Scary Roblox Horror Games in 202328 fevereiro 2025