Malware analysis Malicious activity
Por um escritor misterioso
Last updated 24 fevereiro 2025
Most Common Malware Attacks
CryptoGuard: An asymmetric approach to the ransomware battle

UK and allies support Ukraine calling out Russia's GRU for

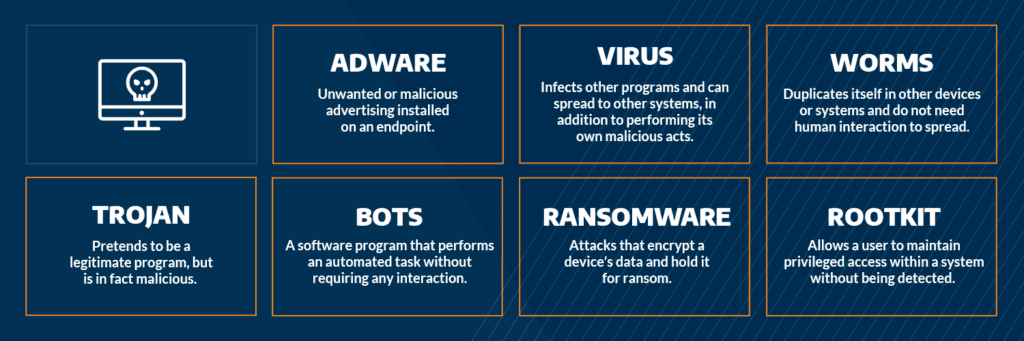
What is Malware? Definition, Types, Prevention - TechTarget
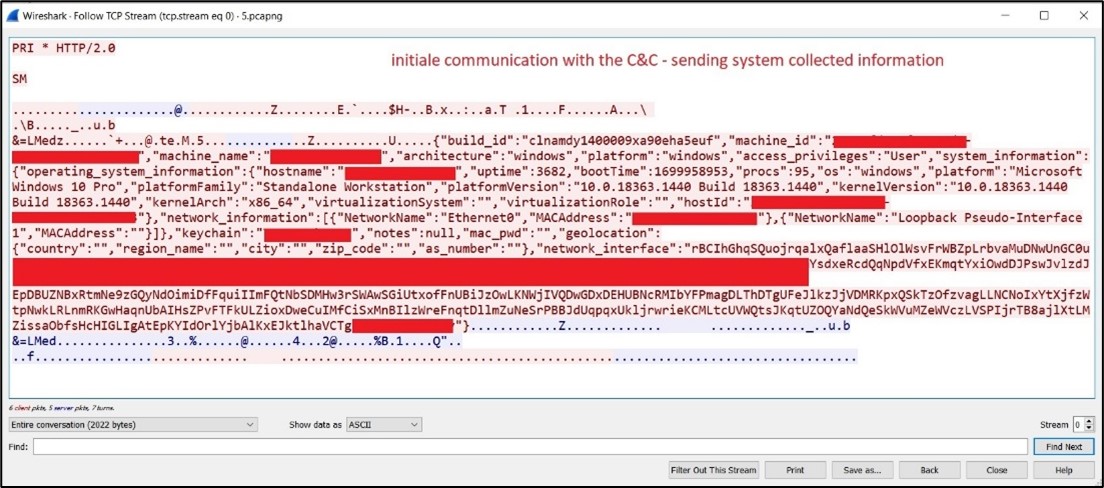
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

AlienVault - Open Threat Exchange
Lab 6-1 Solutions - Practical Malware Analysis [Book]

How to Do Malware Analysis?

Security Orchestration Use Case: Automating Malware Analysis

TryHackMe Hacktivities

Malware Analysis: Steps & Examples - CrowdStrike

StopRansomware: Rhysida Ransomware

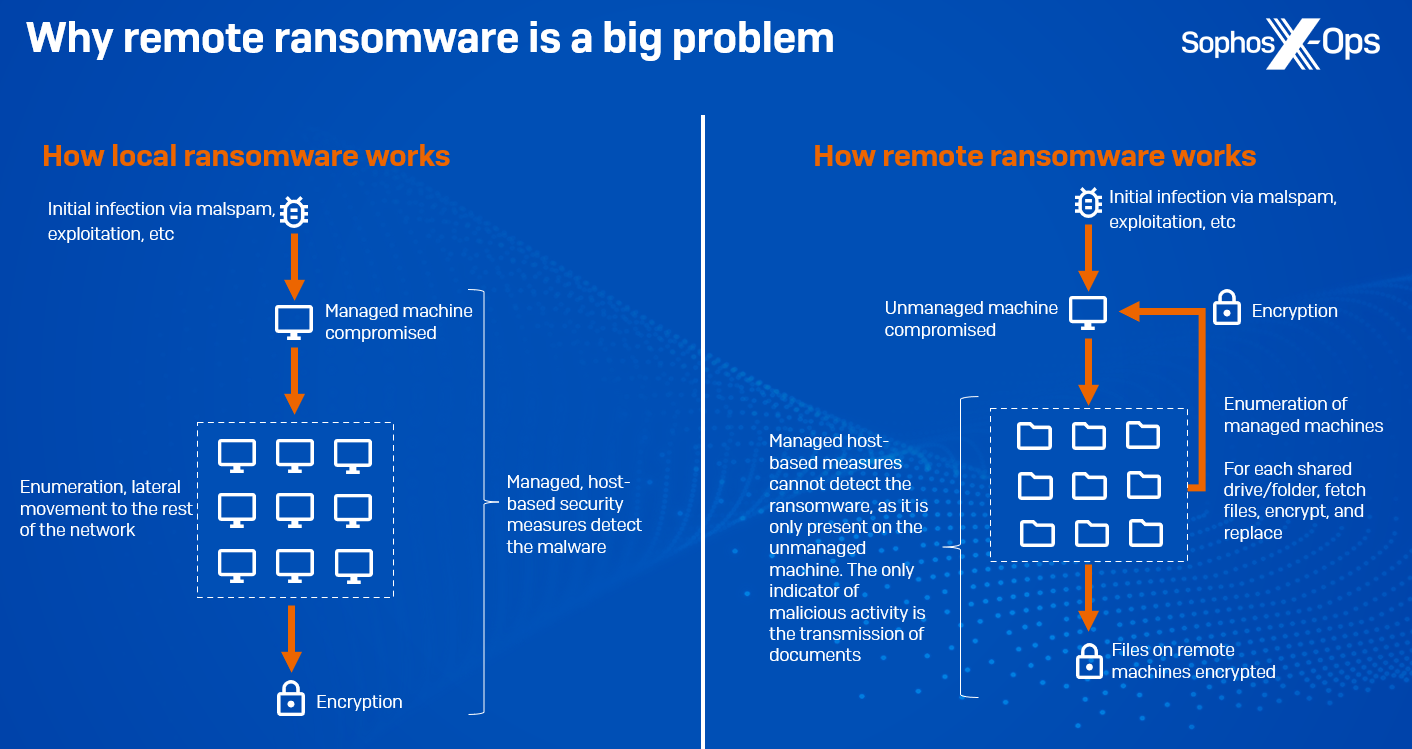
Routers Roasting on an Open Firewall: the KV-botnet Investigation
Recomendado para você
-
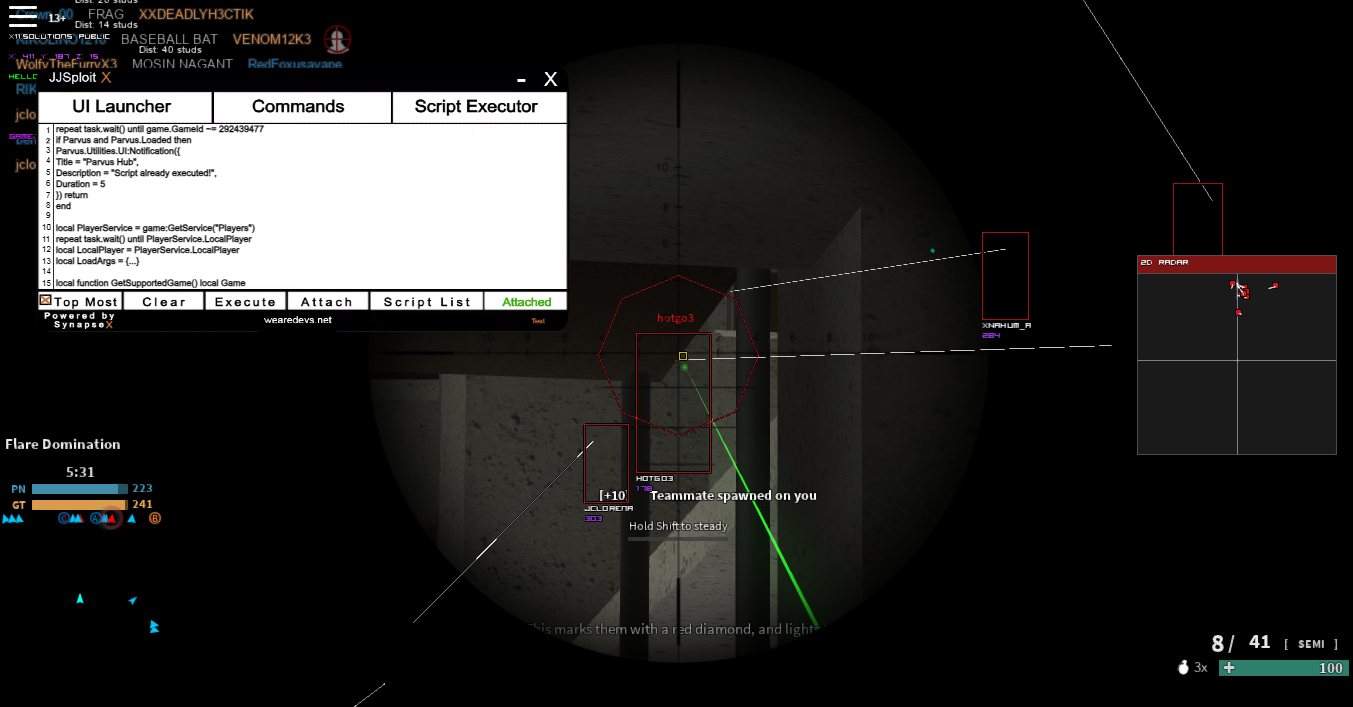
JJSploit - WeAreDevs (@JjSploit) / X24 fevereiro 2025
-
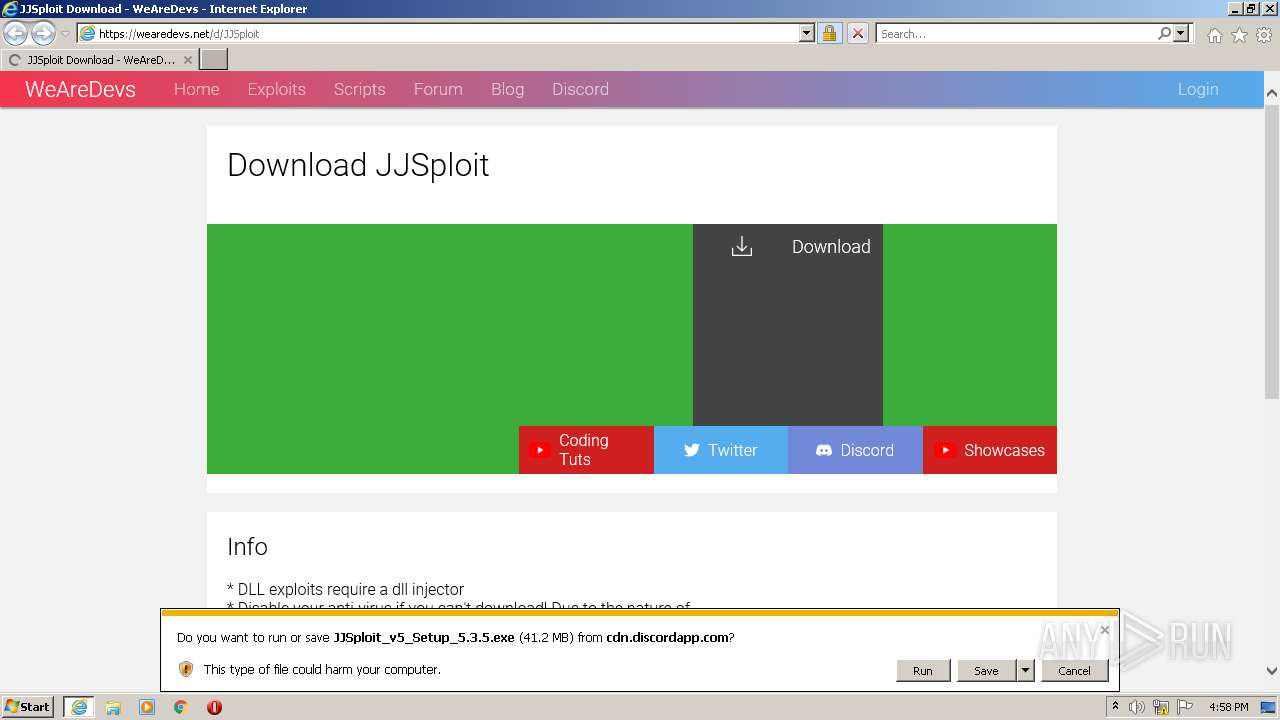
 Jjsploit V4-Www.Wearedevs.Net - Colaboratory24 fevereiro 2025
Jjsploit V4-Www.Wearedevs.Net - Colaboratory24 fevereiro 2025 -
 UnKnoWnCheaTs - Multiplayer Game Hacking and Cheats - View Single24 fevereiro 2025
UnKnoWnCheaTs - Multiplayer Game Hacking and Cheats - View Single24 fevereiro 2025 -
 Roblox Executor - The Ultimate Tool for Dominating Roblox Games24 fevereiro 2025
Roblox Executor - The Ultimate Tool for Dominating Roblox Games24 fevereiro 2025 -
 A Guide to Exploiting (Post-Byfron) : r/robloxhackers24 fevereiro 2025
A Guide to Exploiting (Post-Byfron) : r/robloxhackers24 fevereiro 2025 -
 PalXploits24 fevereiro 2025
PalXploits24 fevereiro 2025 -
 WeAreDevs.net review pt.1 I exploits on wearedevs24 fevereiro 2025
WeAreDevs.net review pt.1 I exploits on wearedevs24 fevereiro 2025 -
 Exploits :: PalXploits24 fevereiro 2025
Exploits :: PalXploits24 fevereiro 2025 -
how to download jj exploit roblox|TikTok Search24 fevereiro 2025
-
 🤑ROBLOX HACK TUTORIAL🤑 (GERMAN)24 fevereiro 2025
🤑ROBLOX HACK TUTORIAL🤑 (GERMAN)24 fevereiro 2025
você pode gostar
-
 ID, Roblox Navy Simulator Wiki24 fevereiro 2025
ID, Roblox Navy Simulator Wiki24 fevereiro 2025 -
Classic Female - Face Roblox Item Leak - Rolimon's24 fevereiro 2025
-
 Spider-Man 2 The Game PC 2004 Marvel Activision Video Game Collectible CIB24 fevereiro 2025
Spider-Man 2 The Game PC 2004 Marvel Activision Video Game Collectible CIB24 fevereiro 2025 -
 Fotos: Beyoncé e Jay Z assistem a jogo de basquete em NY - 03/1124 fevereiro 2025
Fotos: Beyoncé e Jay Z assistem a jogo de basquete em NY - 03/1124 fevereiro 2025 -
 Big Inventory Space for Diablo 2 Plugy - Arqade24 fevereiro 2025
Big Inventory Space for Diablo 2 Plugy - Arqade24 fevereiro 2025 -
 IziGames (u/izigamesnet) - Reddit24 fevereiro 2025
IziGames (u/izigamesnet) - Reddit24 fevereiro 2025 -
 JOGO do HOMEM ARANHA Que Roda Em PC Fraco 2gb de RAM Intel HD24 fevereiro 2025
JOGO do HOMEM ARANHA Que Roda Em PC Fraco 2gb de RAM Intel HD24 fevereiro 2025 -
 The Last of Us TV show, Critical Consensus24 fevereiro 2025
The Last of Us TV show, Critical Consensus24 fevereiro 2025 -
 Flat pastel pink cat icon Royalty Free Vector Image24 fevereiro 2025
Flat pastel pink cat icon Royalty Free Vector Image24 fevereiro 2025 -
 Camiseta HIGH POPEYE - Roupas e Acessórios24 fevereiro 2025
Camiseta HIGH POPEYE - Roupas e Acessórios24 fevereiro 2025