Malware analysis Malicious activity
Por um escritor misterioso
Last updated 10 março 2025
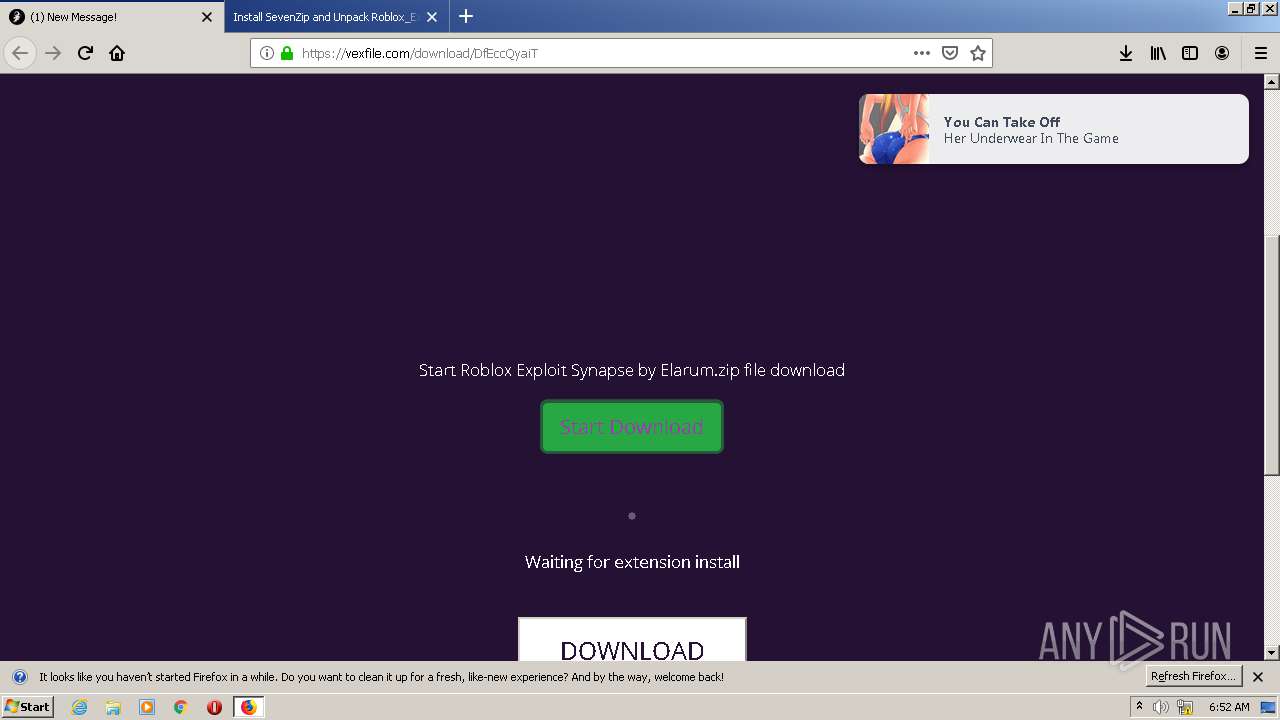
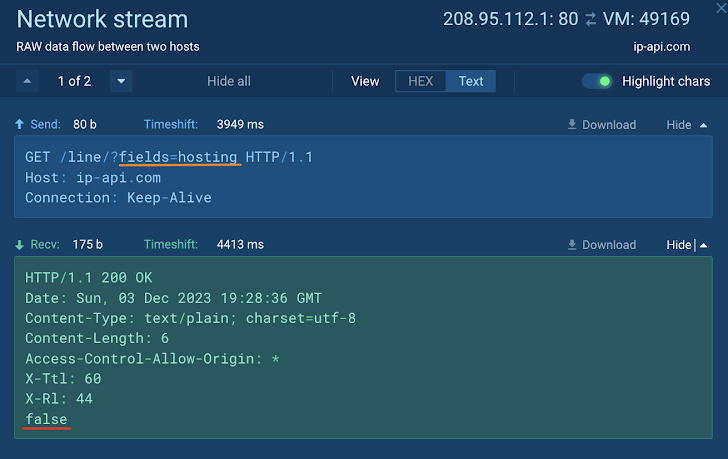
How to Analyze Malware's Network Traffic in A Sandbox

Security Orchestration Use Case: Automating Malware Analysis

PROUD-MAL: static analysis-based progressive framework for deep

Endpoint Detection and Response, Free - What is EDR Security?

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Security Orchestration Use Case: Automating Malware Analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Brute Force Attacks: Password Protection
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware
Malware analysis index.html Malicious activity
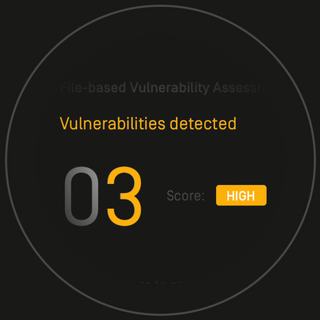
MetaDefender Cloud Advanced threat prevention and detection
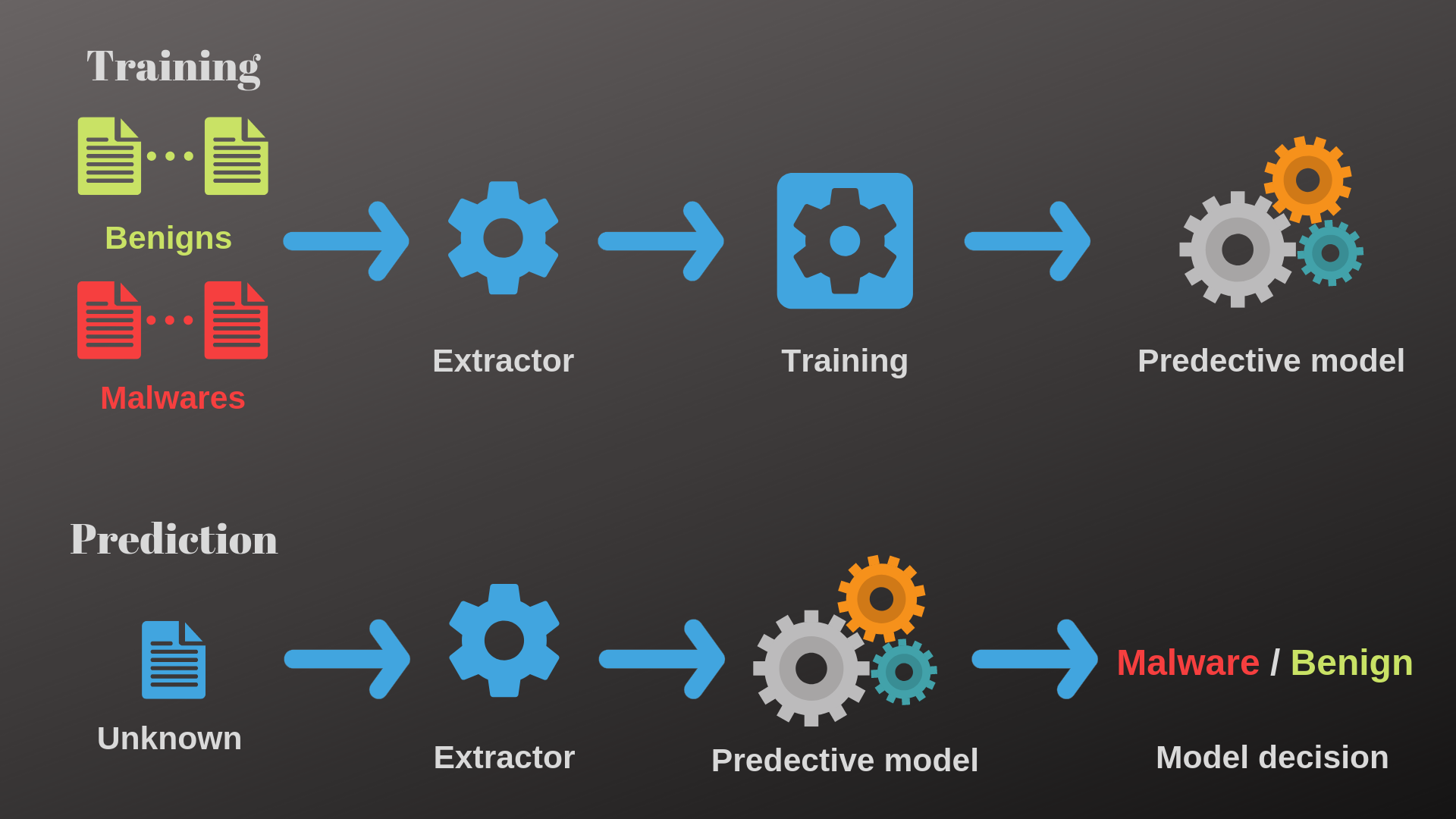
Feature Extraction and Detection of Malwares Using Machine

Interactive Online Malware Sandbox

Cybersecurity News, Insights and Analysis
Recomendado para você
-
 2014-esque Roblox10 março 2025
2014-esque Roblox10 março 2025 -
 Roblox Load All Badges – Get this Extension for 🦊 Firefox (en-US)10 março 2025
Roblox Load All Badges – Get this Extension for 🦊 Firefox (en-US)10 março 2025 -
 Top 10 Firefox Screen Recorders and Add-Ons10 março 2025
Top 10 Firefox Screen Recorders and Add-Ons10 março 2025 -
 RoGold - Development Tools - #72 by Marius198016 - Community Resources - Developer Forum10 março 2025
RoGold - Development Tools - #72 by Marius198016 - Community Resources - Developer Forum10 março 2025 -
 RTC on X: BREAKING: Roblox+ has been removed from the FireFox addons page. Mozilla (who owns firefox) determined the add on was a insecure extension and malicious. It has now been removed10 março 2025
RTC on X: BREAKING: Roblox+ has been removed from the FireFox addons page. Mozilla (who owns firefox) determined the add on was a insecure extension and malicious. It has now been removed10 março 2025 -
 Readwise Highlighter extension (both Chrome and Firefox) doesn't work - Orion Public Issue Tracker10 março 2025
Readwise Highlighter extension (both Chrome and Firefox) doesn't work - Orion Public Issue Tracker10 março 2025 -
 Google, Mozilla Ban Hundreds of Browser Extensions in Chrome, Firefox10 março 2025
Google, Mozilla Ban Hundreds of Browser Extensions in Chrome, Firefox10 março 2025 -
 Use Chome Extensions in Firefox10 março 2025
Use Chome Extensions in Firefox10 março 2025 -
![How to quickly play Flash, Unity 3D and HTML5 games in Firefox [Tip]](https://dt.azadicdn.com/wp-content/uploads/2015/05/web-games2.png?7653) How to quickly play Flash, Unity 3D and HTML5 games in Firefox [Tip]10 março 2025
How to quickly play Flash, Unity 3D and HTML5 games in Firefox [Tip]10 março 2025 -
 Open Studios event on May 1 to take place inside virtual Carson Center, Hixson-Lied College of Fine and Performing Arts10 março 2025
Open Studios event on May 1 to take place inside virtual Carson Center, Hixson-Lied College of Fine and Performing Arts10 março 2025
você pode gostar
-
 Yamamba: bruxa das montanhas é yokai do período Heian10 março 2025
Yamamba: bruxa das montanhas é yokai do período Heian10 março 2025 -
 Como e Onde Monetizar o Aplicativo Framework - r Android App - Parte 1510 março 2025
Como e Onde Monetizar o Aplicativo Framework - r Android App - Parte 1510 março 2025 -
 Roblox Hair ID Codes Combo (December 2023)10 março 2025
Roblox Hair ID Codes Combo (December 2023)10 março 2025 -
What is the best underrated video game you have ever played? - Quora10 março 2025
-
format(webp)) Attack on Titan Final Season Part 3 revela novo vídeo promocional10 março 2025
Attack on Titan Final Season Part 3 revela novo vídeo promocional10 março 2025 -
 Microsoft Flight Simulator Celebrates Franchise's 40th Anniversary and Introduces Halo Infinite Pelican as Free Add-On - Xbox Wire10 março 2025
Microsoft Flight Simulator Celebrates Franchise's 40th Anniversary and Introduces Halo Infinite Pelican as Free Add-On - Xbox Wire10 março 2025 -
didyouknow 👉🏼 all-new #GenZ - BRB Popped Chips10 março 2025
-
 Apple Support on X: 😊 Give your real email to friends and family 🥸 Give unique, random email aliases to websites and apps Here's how to use Hide My Email included with10 março 2025
Apple Support on X: 😊 Give your real email to friends and family 🥸 Give unique, random email aliases to websites and apps Here's how to use Hide My Email included with10 março 2025 -
 Pin by Charlottes on American Classic Sonic Classic sonic, Hedgehog art, Sonic the hedgehog10 março 2025
Pin by Charlottes on American Classic Sonic Classic sonic, Hedgehog art, Sonic the hedgehog10 março 2025 -
 Boruto episode 231 release date and time explained following delay10 março 2025
Boruto episode 231 release date and time explained following delay10 março 2025
