Malware analysis Malicious activity
Por um escritor misterioso
Last updated 25 fevereiro 2025

Routers Roasting on an Open Firewall: the KV-botnet Investigation
Malware analysis file Malicious activity

Malware analysis metasploit.bat Malicious activity

StopRansomware: Rhysida Ransomware

Detail procedure of malware analysis

Robust Malware Detection Models: Learning From Adversarial Attacks

Malware Analysis: Steps & Examples - CrowdStrike
Lab 6-1 Solutions - Practical Malware Analysis [Book]
Interactive Online Malware Sandbox

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1
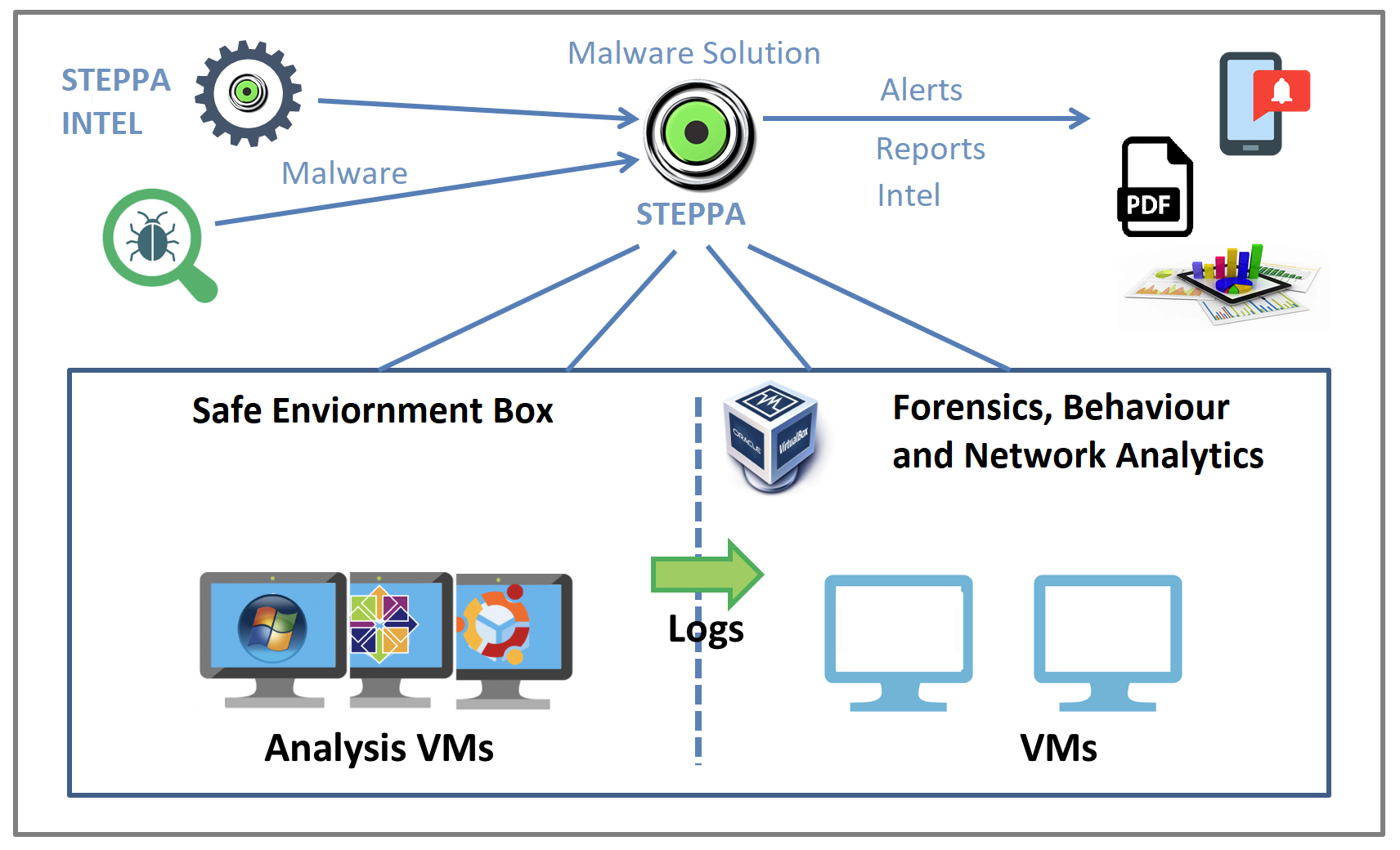
Malware Analysis Solution: Analyze, Detect, and Protect

Security Orchestration Use Case: Automating Malware Analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation
Recomendado para você
-
Steam Workshop::Baldi's Basics Plus Model Pack [WIP]25 fevereiro 2025
-
![0.3.8) Baldi's Basics Plus: Banana Mayham [Baldi's Basics] [Mods]](https://images.gamebanana.com/img/ss/mods/60e949ff36bdd.jpg) 0.3.8) Baldi's Basics Plus: Banana Mayham [Baldi's Basics] [Mods]25 fevereiro 2025
0.3.8) Baldi's Basics Plus: Banana Mayham [Baldi's Basics] [Mods]25 fevereiro 2025 -
 Baldi's Basics Plus PC Game - Free Download Full Version25 fevereiro 2025
Baldi's Basics Plus PC Game - Free Download Full Version25 fevereiro 2025 -
 Stream Baldi 39;s Basics Online from Jon Liek25 fevereiro 2025
Stream Baldi 39;s Basics Online from Jon Liek25 fevereiro 2025 -
![Baldi's Basics And A Bunch Of New Items [Baldi's Basics] [Mods]](https://images.gamebanana.com/img/ss/mods/5d0fa0edc3ebd.webp) Baldi's Basics And A Bunch Of New Items [Baldi's Basics] [Mods]25 fevereiro 2025
Baldi's Basics And A Bunch Of New Items [Baldi's Basics] [Mods]25 fevereiro 2025 -
 Every open source of Baldi's Basics Plus is personalized : r/BaldisBasicsEdu25 fevereiro 2025
Every open source of Baldi's Basics Plus is personalized : r/BaldisBasicsEdu25 fevereiro 2025 -
 Baldi's Basics Full Game Public Demo Minecraft Map25 fevereiro 2025
Baldi's Basics Full Game Public Demo Minecraft Map25 fevereiro 2025 -
 BALDI'S FINISHED!! The Ending To Baldi's Basics Plus +25 fevereiro 2025
BALDI'S FINISHED!! The Ending To Baldi's Basics Plus +25 fevereiro 2025 -
 Baldi's Basics in Education and Crafting ~ Bedrock Multiplayer Minecraft Map25 fevereiro 2025
Baldi's Basics in Education and Crafting ~ Bedrock Multiplayer Minecraft Map25 fevereiro 2025 -
 Games like Baldi Basics Plus v0.1 • Games similar to Baldi Basics Plus v0.1 • RAWG25 fevereiro 2025
Games like Baldi Basics Plus v0.1 • Games similar to Baldi Basics Plus v0.1 • RAWG25 fevereiro 2025
você pode gostar
-
 Cyberpunk Girl Neon Colors Mobile Wallpaper 3 by gam3sd3an on DeviantArt25 fevereiro 2025
Cyberpunk Girl Neon Colors Mobile Wallpaper 3 by gam3sd3an on DeviantArt25 fevereiro 2025 -
 Rion Steiner リオン・シュタイナー on X: Hunter x Hunter - Succession War Opening (Fanmade) #anime #SuccessionWar #hxh #hunterxhunter #fanmade #opening / X25 fevereiro 2025
Rion Steiner リオン・シュタイナー on X: Hunter x Hunter - Succession War Opening (Fanmade) #anime #SuccessionWar #hxh #hunterxhunter #fanmade #opening / X25 fevereiro 2025 -
 Evolution of PlayStation Handhelds (Animation)25 fevereiro 2025
Evolution of PlayStation Handhelds (Animation)25 fevereiro 2025 -
 Projeto Trânsito Legal: conhecendo as regras - Educa Criança25 fevereiro 2025
Projeto Trânsito Legal: conhecendo as regras - Educa Criança25 fevereiro 2025 -
 Hamster's Life Cycle: From Pup to Senior25 fevereiro 2025
Hamster's Life Cycle: From Pup to Senior25 fevereiro 2025 -
 Parques em Brasília: estrutura e belezas do Cerrado perto de casa25 fevereiro 2025
Parques em Brasília: estrutura e belezas do Cerrado perto de casa25 fevereiro 2025 -
 Ler com prazer: Pokémon Go - Algumas Sugestões Para Trabalhar na25 fevereiro 2025
Ler com prazer: Pokémon Go - Algumas Sugestões Para Trabalhar na25 fevereiro 2025 -
Mortal kombat e personagens25 fevereiro 2025
-
DriveClub [ First Print Blue Case ] (PS4) NEW25 fevereiro 2025
-
 Coluna Social Helio Dórea - Folha Vitória25 fevereiro 2025
Coluna Social Helio Dórea - Folha Vitória25 fevereiro 2025
![Steam Workshop::Baldi's Basics Plus Model Pack [WIP]](https://steamuserimages-a.akamaihd.net/ugc/2024968930177269512/3FE0437E3A6F18C46AE1030976C87F2F793E05BD/?imw=637&imh=358&ima=fit&impolicy=Letterbox&imcolor=%23000000&letterbox=true)
