Malware analysis Malicious activity
Por um escritor misterioso
Last updated 04 março 2025

Brute Force Attacks: Password Protection

How to Remove Windows Defender Security Warning Scam

Endpoint Detection and Response, Free - What is EDR Security?

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

How to Do Malware Analysis?
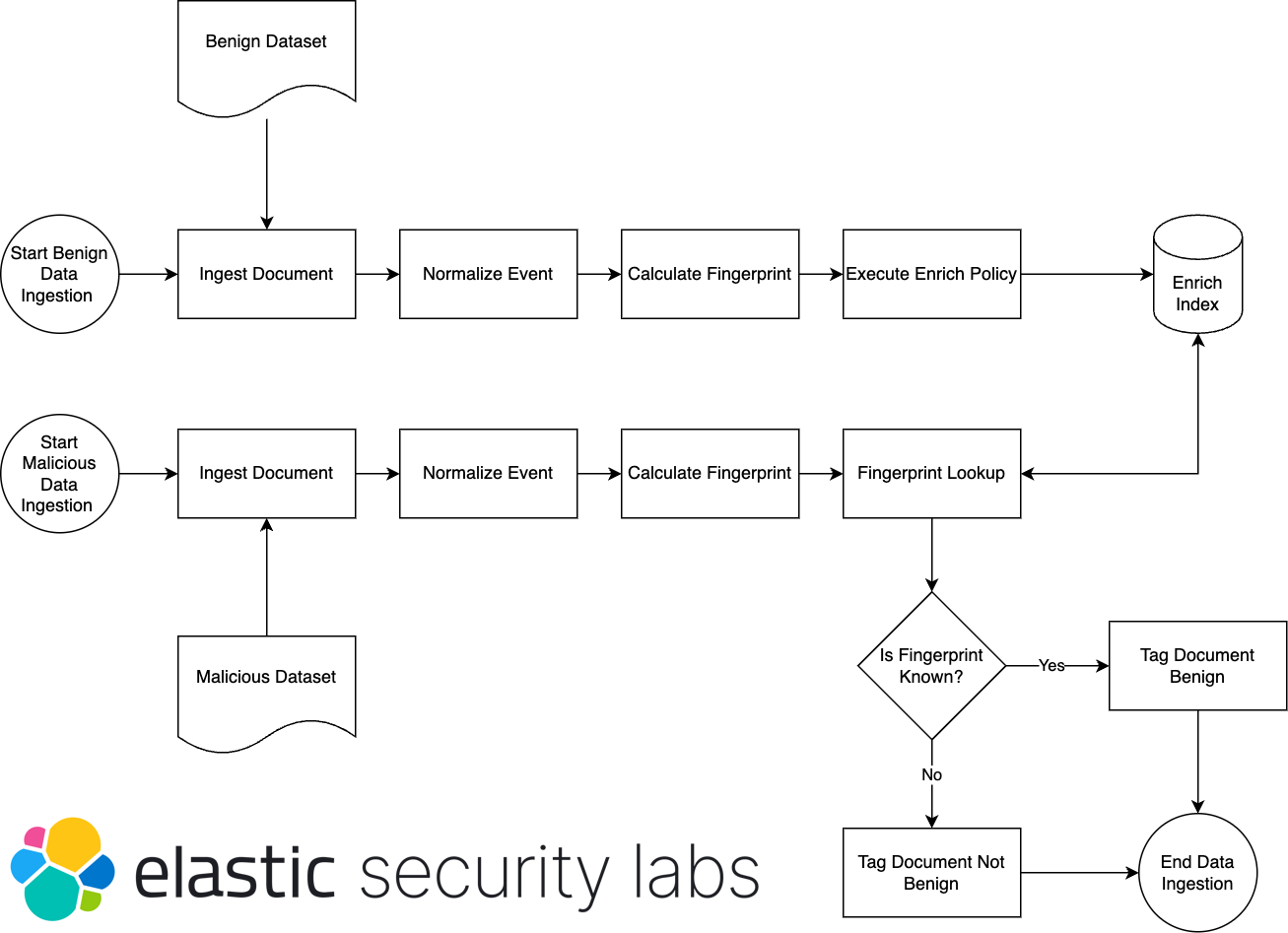
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog

Detail procedure of malware analysis
Recomendado para você
-
How to block ads on AnimeSuge? And Alternatives04 março 2025
-
 Every KissAnime Replacement worth Visiting in 2023- 100% Working04 março 2025
Every KissAnime Replacement worth Visiting in 2023- 100% Working04 março 2025 -
 it has been two-week since I stopped using animesuge to see if you guys removed this. so I'm when will this be gone (I'm not rage-hating) love this website, but this is04 março 2025
it has been two-week since I stopped using animesuge to see if you guys removed this. so I'm when will this be gone (I'm not rage-hating) love this website, but this is04 março 2025 -
 Is Animesuge Safe And Legit? - Let's Find Out04 março 2025
Is Animesuge Safe And Legit? - Let's Find Out04 março 2025 -
 Anime Suge - BiliBili04 março 2025
Anime Suge - BiliBili04 março 2025 -
my phone Themes - Miraculous Ladybug - Wattpad04 março 2025
-
 Animesuge - Watch Anime Free APK for Android Download04 março 2025
Animesuge - Watch Anime Free APK for Android Download04 março 2025 -
Anilab - alternative for Crunchyroll, Funimation, KissAnime, 9anime, AnimeSUge, 4anime and other anime streaming site04 março 2025
-
I need help fr drop some anime sites04 março 2025
-
 AnimeSuge got terminated, and now has a new website. : r/AnimeSuge04 março 2025
AnimeSuge got terminated, and now has a new website. : r/AnimeSuge04 março 2025
você pode gostar
-
 Gênero: Ação - Animes Online04 março 2025
Gênero: Ação - Animes Online04 março 2025 -
 Subway Surfers +4 Trainer Download04 março 2025
Subway Surfers +4 Trainer Download04 março 2025 -
 POKÉMON SUN - EXTRA - QUEST ULTRA BEASTS04 março 2025
POKÉMON SUN - EXTRA - QUEST ULTRA BEASTS04 março 2025 -
 Wrestle Tours & Club PROGRESS - PROGRESS Wrestling - Watch on Demand PROGRESS PLUS04 março 2025
Wrestle Tours & Club PROGRESS - PROGRESS Wrestling - Watch on Demand PROGRESS PLUS04 março 2025 -
 List Harborfields Public Library04 março 2025
List Harborfields Public Library04 março 2025 -
 Como criar um JOGO DE TABULEIRO PERSONALIZADO - Atividade Interativa Digital04 março 2025
Como criar um JOGO DE TABULEIRO PERSONALIZADO - Atividade Interativa Digital04 março 2025 -
 Pin em CSGO Wallpapers04 março 2025
Pin em CSGO Wallpapers04 março 2025 -
 Conheça o Novo Anime Record Of Ragnarok - Nova Era Geek04 março 2025
Conheça o Novo Anime Record Of Ragnarok - Nova Era Geek04 março 2025 -
 I sorteio da Promoção Sorte na Conta BRK04 março 2025
I sorteio da Promoção Sorte na Conta BRK04 março 2025 -
 5 NEW* CODES PROJECT NEW WORLD ROBLOX04 março 2025
5 NEW* CODES PROJECT NEW WORLD ROBLOX04 março 2025

