Malware analysis Malicious activity
Por um escritor misterioso
Last updated 24 janeiro 2025

Malware Analysis: Steps & Examples - CrowdStrike

How to Analyze Malware's Network Traffic in A Sandbox

How to build a malware analysis sandbox with Elastic Security

How to Do Malware Analysis?

StopRansomware: Rhysida Ransomware

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware Analysis Benefits Incident Response

How to Analyze Malware's Network Traffic in A Sandbox
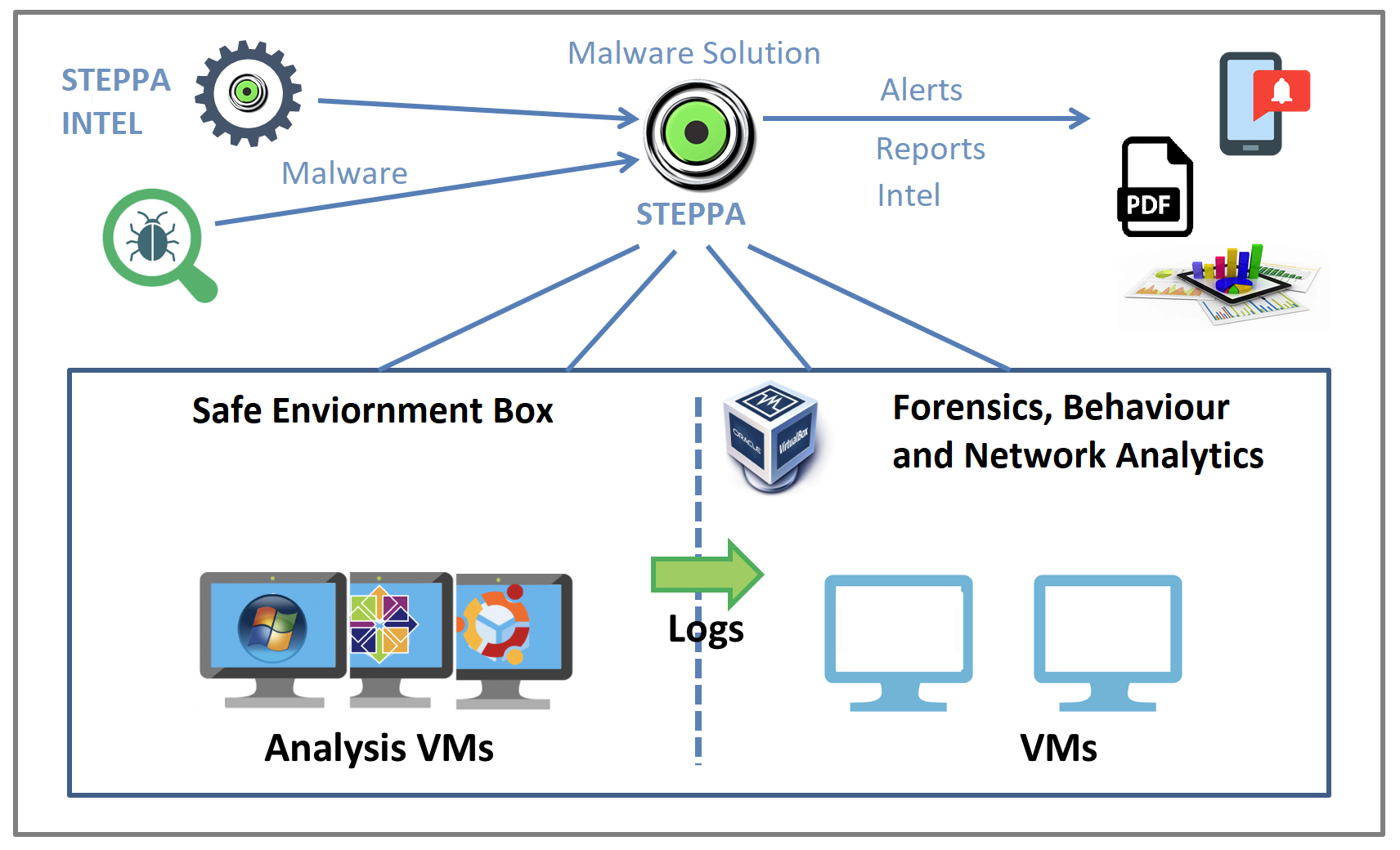
Malware Analysis Solution: Analyze, Detect, and Protect

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus
Malware analysis Malicious activity

Endpoint Detection and Response, Free - What is EDR Security?

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

The Guide to Ransomware Solutions in 2023 - Security Boulevard
Recomendado para você
-
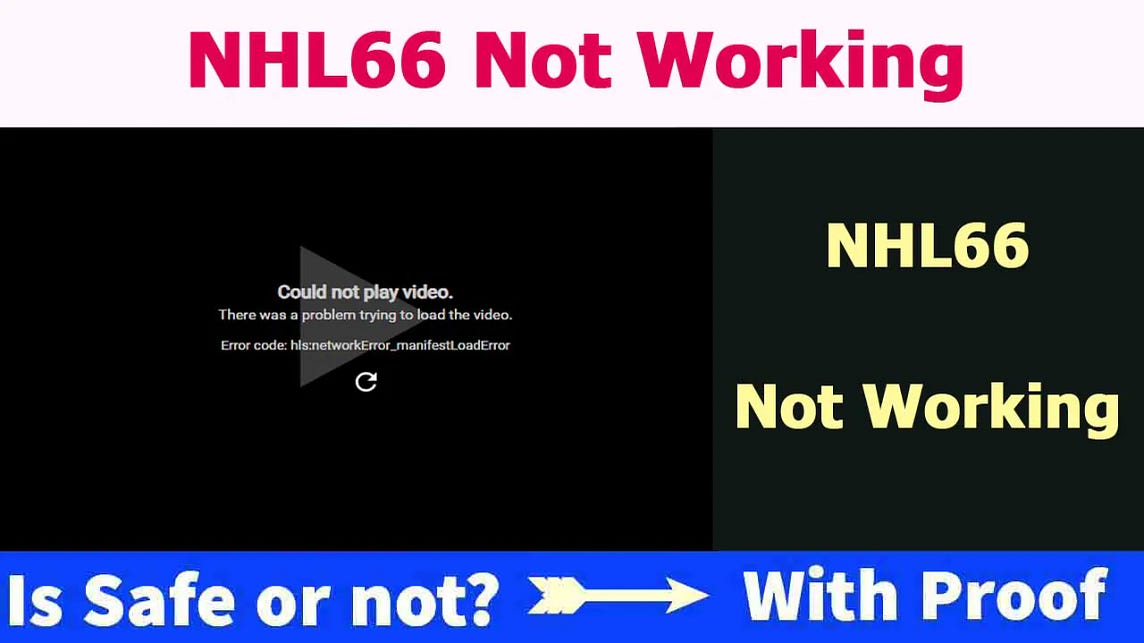
 NHL66 Popup extension - Opera add-ons24 janeiro 2025
NHL66 Popup extension - Opera add-ons24 janeiro 2025 -
 The most insightful stories about Live Streaming Service - Medium24 janeiro 2025
The most insightful stories about Live Streaming Service - Medium24 janeiro 2025 -
 NHL66 _ NHL Streams - Google Chrome 2022-01-13 20-32-4724 janeiro 2025
NHL66 _ NHL Streams - Google Chrome 2022-01-13 20-32-4724 janeiro 2025 -
NHL66 - Free NHL Live Stream 202324 janeiro 2025
-
nhl66.ir Traffic Analytics, Ranking Stats & Tech Stack24 janeiro 2025
-
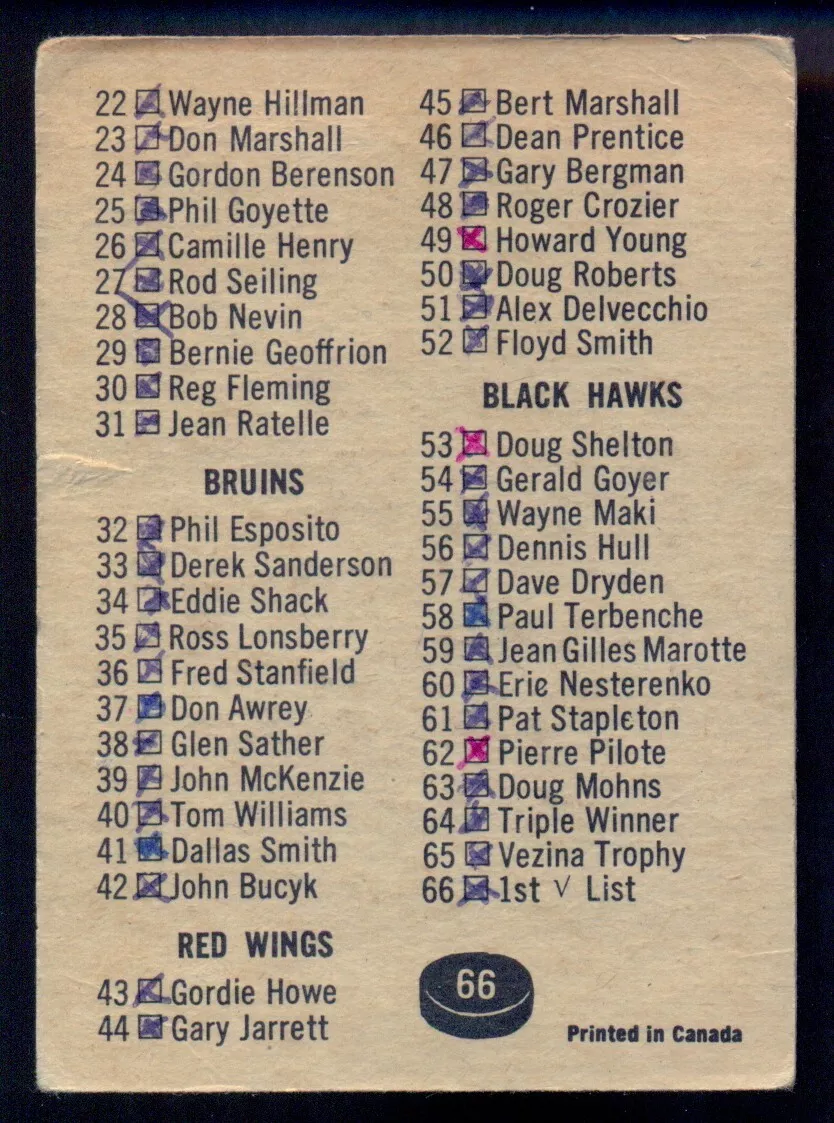 1967-68 TOPPS HOCKEY NHL #66 First Checklist marked (1-66) VG-EX24 janeiro 2025
1967-68 TOPPS HOCKEY NHL #66 First Checklist marked (1-66) VG-EX24 janeiro 2025 -
 5) NHL66 in 2023 What is quran, True friends, Bible passages24 janeiro 2025
5) NHL66 in 2023 What is quran, True friends, Bible passages24 janeiro 2025 -
 OPI Nail Polish 15ml - My Gecko Does Tricks NHL66 - QH Clothing24 janeiro 2025
OPI Nail Polish 15ml - My Gecko Does Tricks NHL66 - QH Clothing24 janeiro 2025 -
 1635041K600898190 san jose sharks hockey nhl (66) NHL Sports24 janeiro 2025
1635041K600898190 san jose sharks hockey nhl (66) NHL Sports24 janeiro 2025 -
 OPI Nagellack 15ml - My Gecko Does Tricks NHL6624 janeiro 2025
OPI Nagellack 15ml - My Gecko Does Tricks NHL6624 janeiro 2025
você pode gostar
-
Waikato Regional Council hunting for rook sightings24 janeiro 2025
-
 Get to Know: The Scottish Highland24 janeiro 2025
Get to Know: The Scottish Highland24 janeiro 2025 -
 Roblox New Menu Tutorial: Get It Now! (Read Description) — Eightify24 janeiro 2025
Roblox New Menu Tutorial: Get It Now! (Read Description) — Eightify24 janeiro 2025 -
ids de musica para roblox reggaeton|Pesquisa do TikTok24 janeiro 2025
-
Jeff The Killer24 janeiro 2025
-
CapCut_cachorro morreu homenagem triste24 janeiro 2025
-
 Tênis - Educação Física Enem24 janeiro 2025
Tênis - Educação Física Enem24 janeiro 2025 -
 Batman: Arkham City—A Knight to Remember24 janeiro 2025
Batman: Arkham City—A Knight to Remember24 janeiro 2025 -
 Metaverso na decoração: Como isso irá funcionar? - La Decora24 janeiro 2025
Metaverso na decoração: Como isso irá funcionar? - La Decora24 janeiro 2025 -
 Maze Runner: The Death Cure (film), Logopedia24 janeiro 2025
Maze Runner: The Death Cure (film), Logopedia24 janeiro 2025