License to Kill: Leveraging License Management to Attack ICS Networks
Por um escritor misterioso
Last updated 27 dezembro 2024
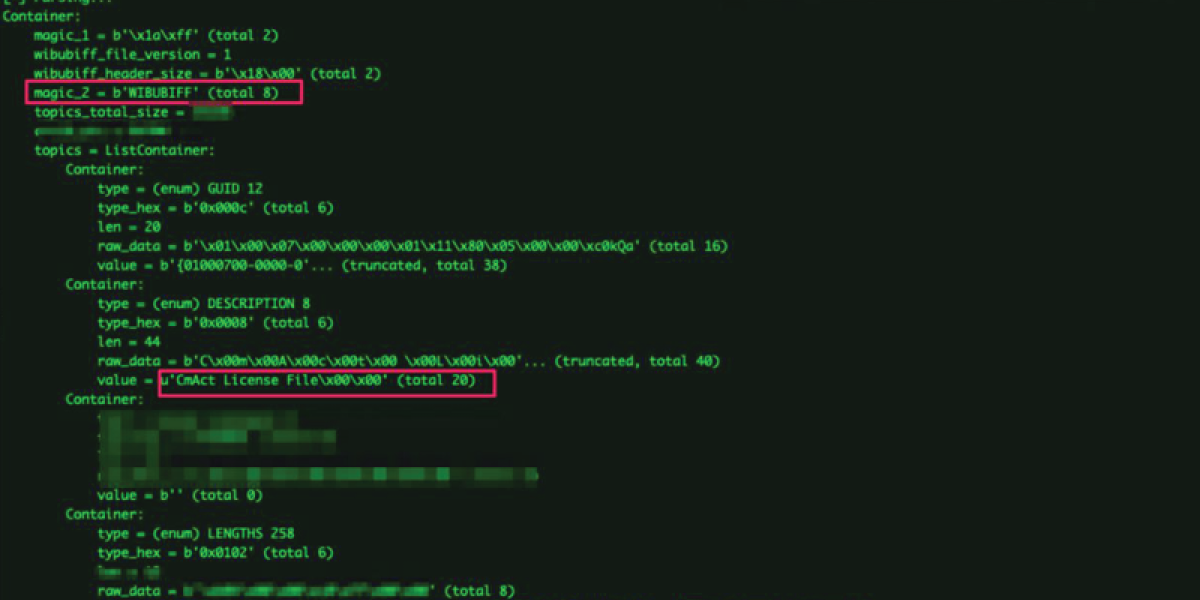
Claroty researchers have uncovered six critical vulnerabilities in Wibu-Systems’ CodeMeter third-party license management component, which could expose OT environments across numerous industries to exploits via phishing campaigns or direct attacks.
-min.png)
BlastShield White Paper
PDF) Keeping Host Sanity for Security of the SCADA Systems
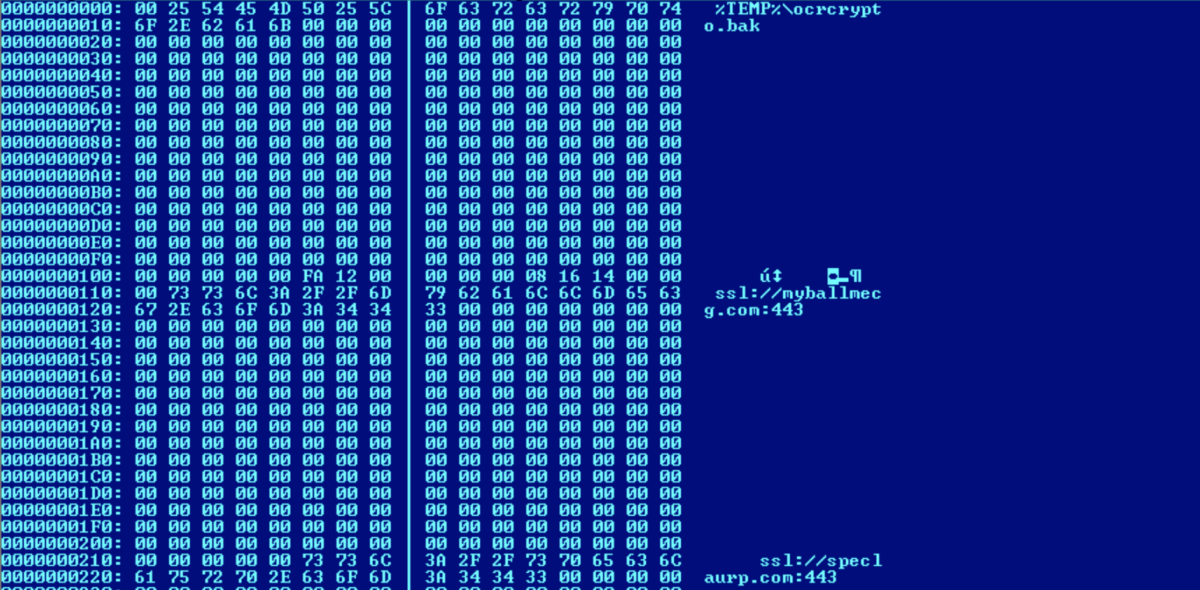
Updated MATA attacks industrial companies in Eastern Europe

Network Security Strategies, PDF, Penetration Test
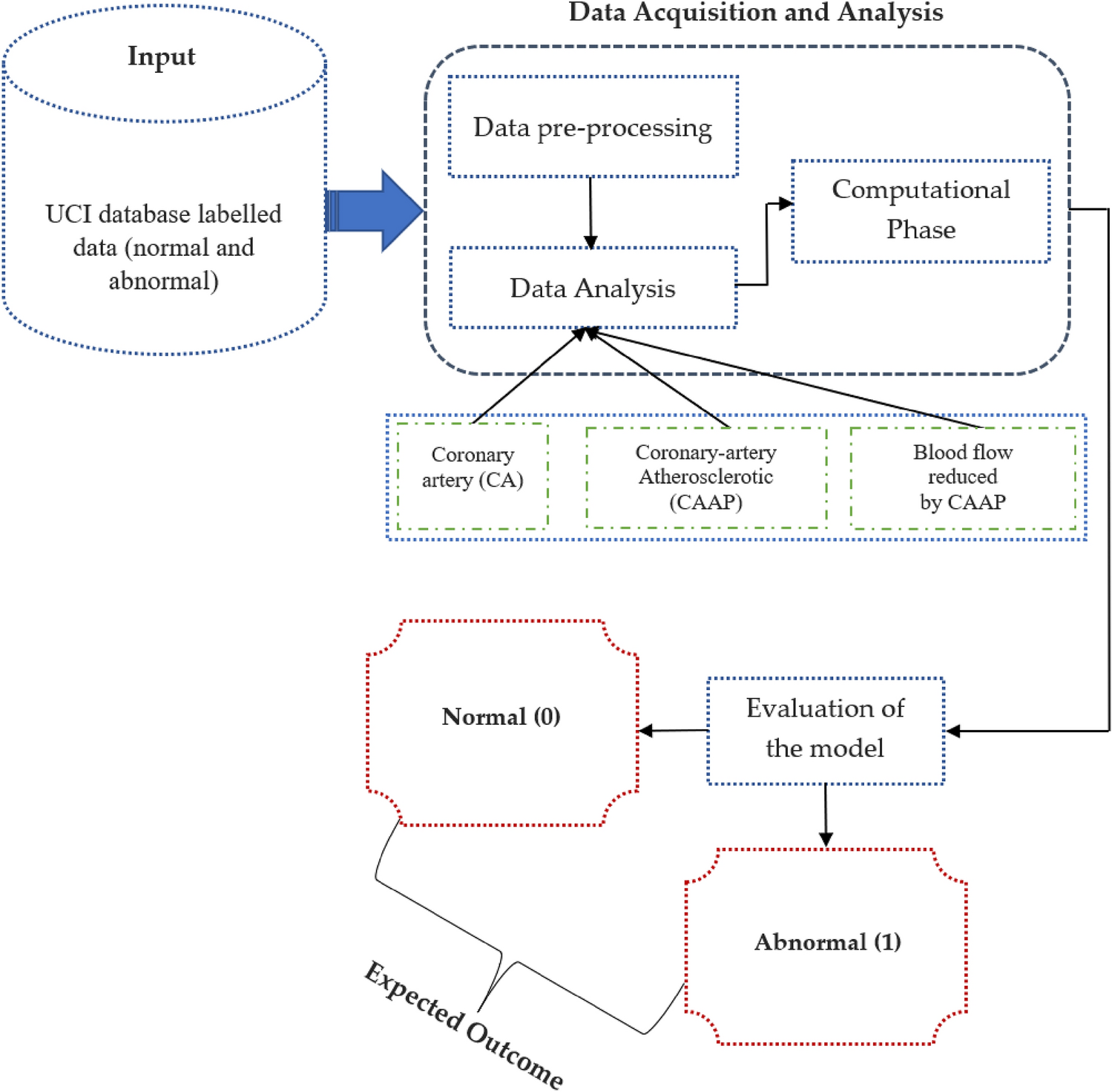
An active learning machine technique based prediction of cardiovascular heart disease from UCI-repository database

Smart Grid: Cyber Attacks, Critical Defense Approaches, and Digital Twin – arXiv Vanity
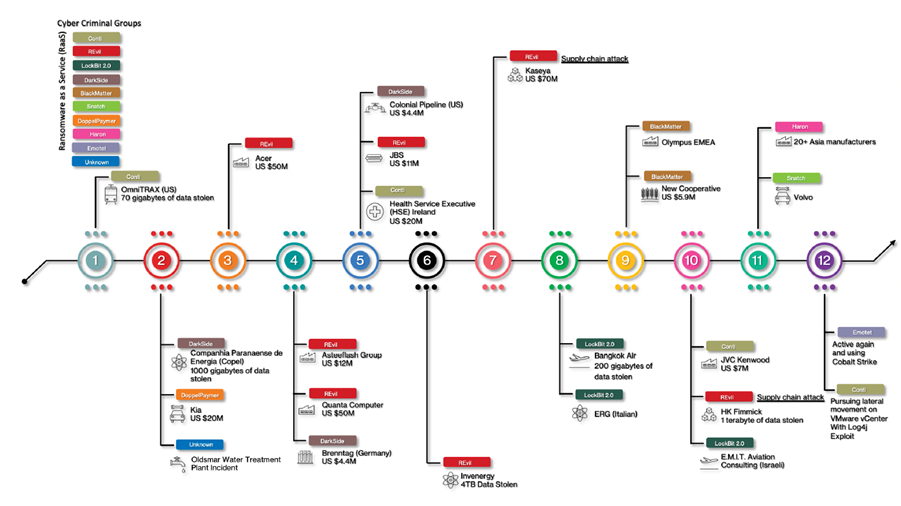
An In-Depth Look at ICS Vulnerabilities Part 1
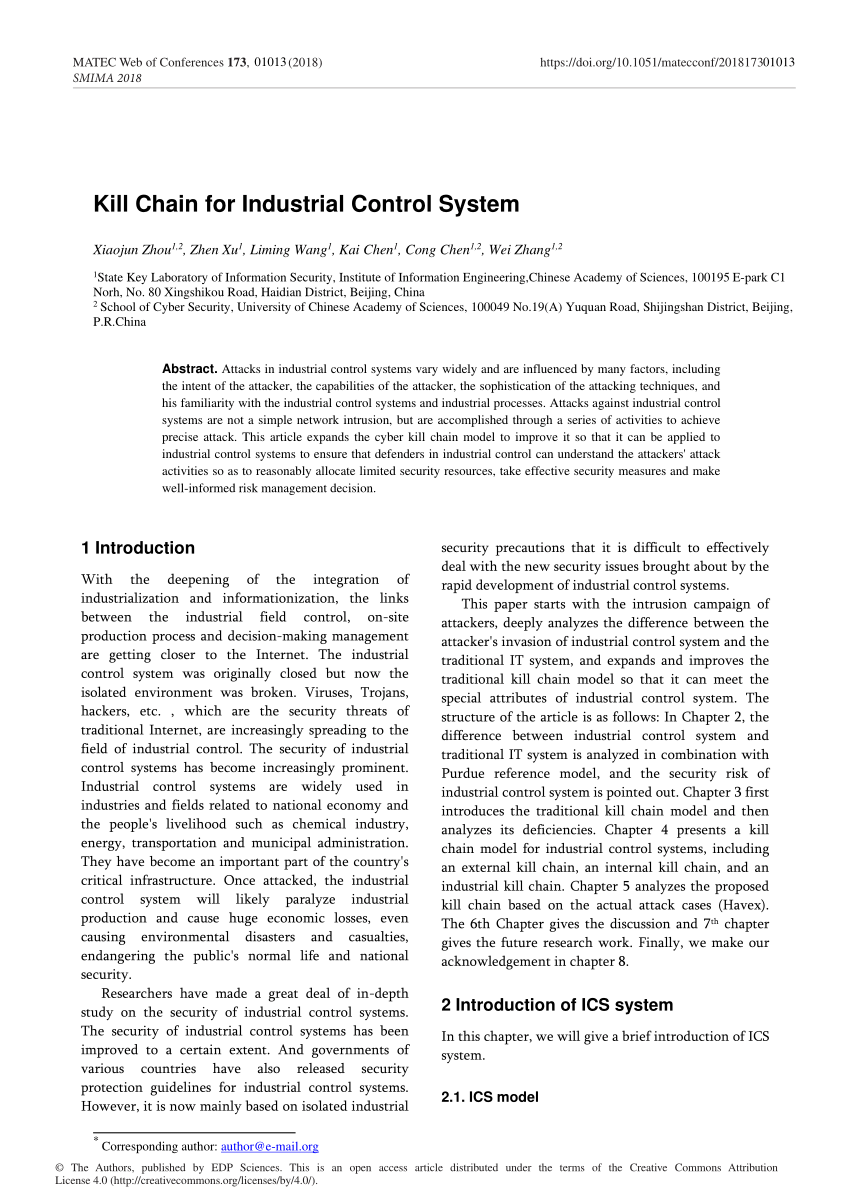
PDF) Kill Chain for Industrial Control System
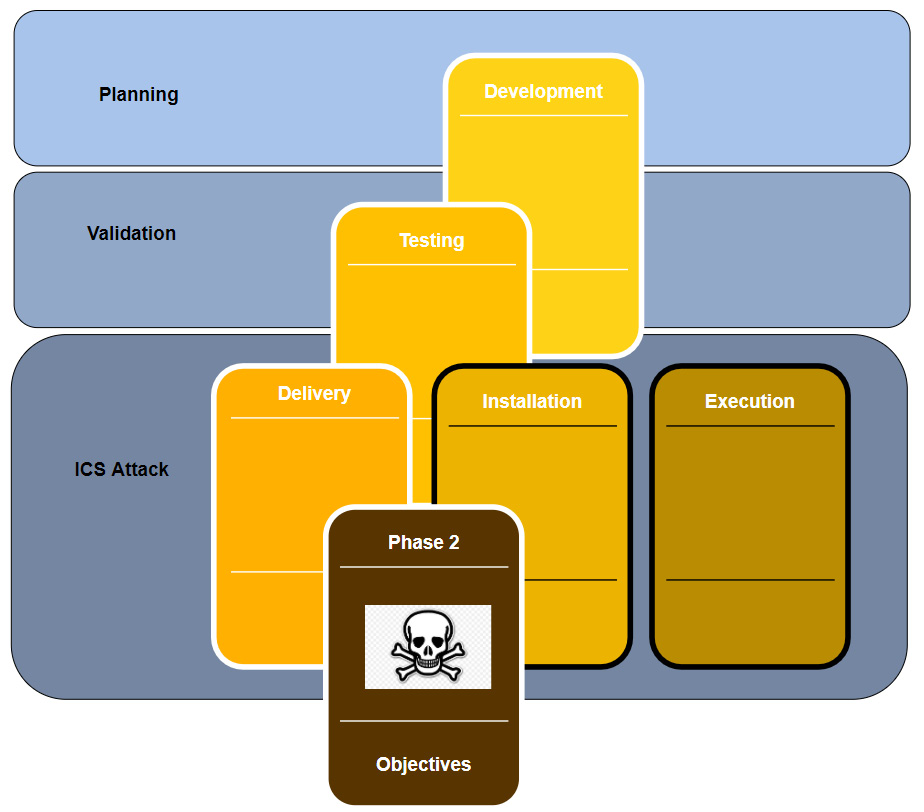
How to Pentest ICS Environments - Packt - SecPro

License to Kill: Leveraging License Management to Attack ICS Networks
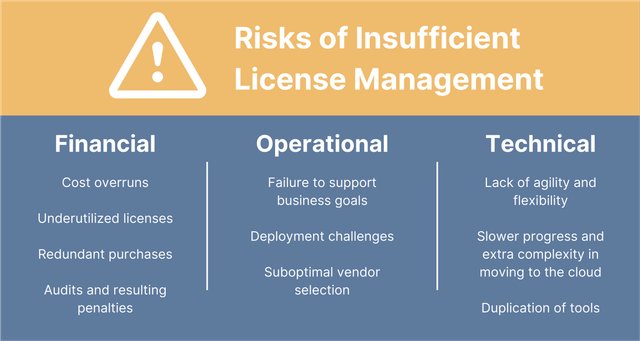
The 6 Key Principles of Software License Management

Eliptic Curve Cryptography 2, PDF, Key (Cryptography)

What Happens When Malware Targets Process Safety Systems?, Chemical Processing
Recomendado para você
-
 Hacker Typer Lets You Turn Jibberish Into Useless Code27 dezembro 2024
Hacker Typer Lets You Turn Jibberish Into Useless Code27 dezembro 2024 -
 Hacker Photos and Images27 dezembro 2024
Hacker Photos and Images27 dezembro 2024 -
Hacker Typer (@HackerTyperIO) / X27 dezembro 2024
-
 Simulating Complex Systems with Python: How Does COVID Spread?27 dezembro 2024
Simulating Complex Systems with Python: How Does COVID Spread?27 dezembro 2024 -
Computer Hacker Prank! - Apps on Google Play27 dezembro 2024
-
 GitHub Education on X: What was the first programming language27 dezembro 2024
GitHub Education on X: What was the first programming language27 dezembro 2024 -
Dr. Rajendra Kumar on LinkedIn: A Holistic Approach to Personal Data Protection27 dezembro 2024
-
 Lacked memLimitMB field when using db.hostInfo() - Ops and Admin - MongoDB Developer Community Forums27 dezembro 2024
Lacked memLimitMB field when using db.hostInfo() - Ops and Admin - MongoDB Developer Community Forums27 dezembro 2024 -
Eric Hilton on LinkedIn: What are your thoughts? I want to hear from you and your perspective27 dezembro 2024
-
 Hacking Pranks: How to Flip Photos, Change Images & Inject Messages into Friends' Browsers on Your Wi-Fi Network « Null Byte :: WonderHowTo27 dezembro 2024
Hacking Pranks: How to Flip Photos, Change Images & Inject Messages into Friends' Browsers on Your Wi-Fi Network « Null Byte :: WonderHowTo27 dezembro 2024
você pode gostar
-
 Street Fighter™ V – Capcom Pro Tour Premier Pass Complete Bundle27 dezembro 2024
Street Fighter™ V – Capcom Pro Tour Premier Pass Complete Bundle27 dezembro 2024 -
How to readeam grand peace online codes|TikTok Search27 dezembro 2024
-
 Controle a Apple TV com a Central de Controle do iOS ou iPadOS - Suporte da Apple (BR)27 dezembro 2024
Controle a Apple TV com a Central de Controle do iOS ou iPadOS - Suporte da Apple (BR)27 dezembro 2024 -
 I Found EVERY SECRET DOOR in Roblox Doors! (What's INSIDE IT27 dezembro 2024
I Found EVERY SECRET DOOR in Roblox Doors! (What's INSIDE IT27 dezembro 2024 -
Russian Roulette27 dezembro 2024
-
Ryu has an Exciting New Form Courtesy of Street Fighter Duel27 dezembro 2024
-
 Star Wars Episode III Revenge of the Sith Poster 24x3627 dezembro 2024
Star Wars Episode III Revenge of the Sith Poster 24x3627 dezembro 2024 -
 Boneco Action Figure Sonic Articulado 23cm - Casa & Vídeo27 dezembro 2024
Boneco Action Figure Sonic Articulado 23cm - Casa & Vídeo27 dezembro 2024 -
 Pokemon Gold Brendan in Kanto on The Duck : 035 Thats a Gust.Right?27 dezembro 2024
Pokemon Gold Brendan in Kanto on The Duck : 035 Thats a Gust.Right?27 dezembro 2024 -
John Doe Escape Game27 dezembro 2024