How to DDoS Like an Ethical Hacker
Por um escritor misterioso
Last updated 28 março 2025
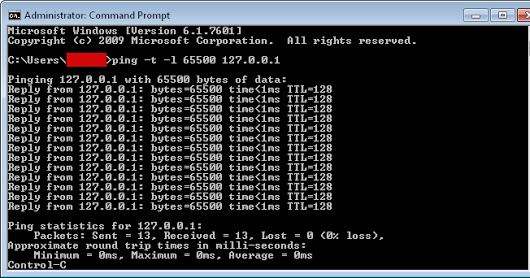
Learn how to DDoS so you can understand how cybercriminals target their victims. See what you can do to prevent getting DDoSed.

How DDoS Works: a 2023 Beginners Guide

Ethical Hacking: The Art of Securing Systems
How to DDoS Like an Ethical Hacker

Legendary Hacks: CyberBunker

CEH Certification, Certified Ethical Hacker, CEH Course

6 common application-layer DDoS attacks – key signals and indicators
What Is a DDoS Attack: Types, Working, Prevention and More

Cyber News #10 - DDoS Attacks: A Global Danger
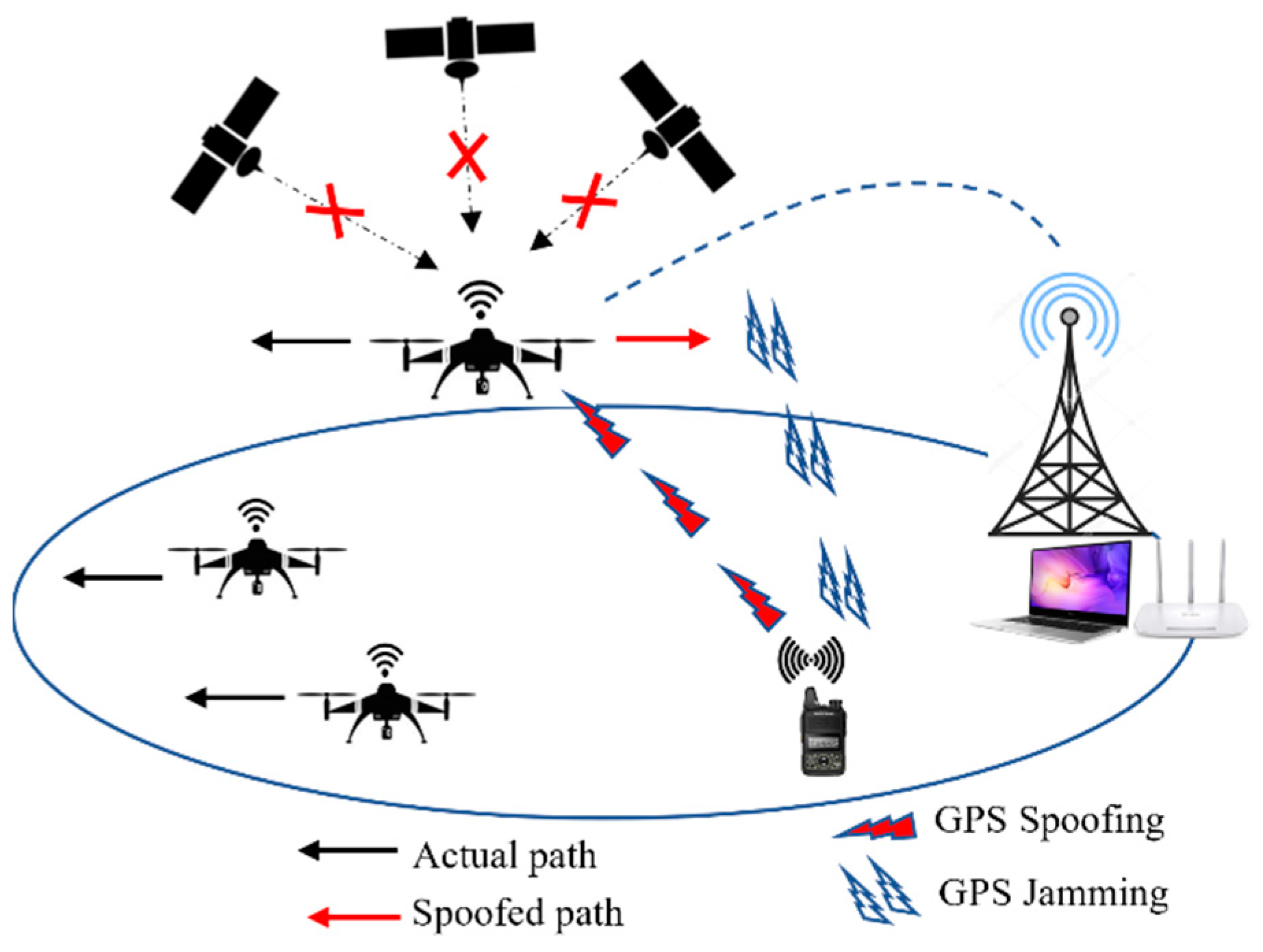
JSAN, Free Full-Text

Ethical Hacking Volume 10: DoS/DDoS Attacks: Protecting Network and Services (English Edition) - eBooks em Inglês na

Defending Enterprise Network Security: a DDoS Attack Primer
Recomendado para você
-
 How to code like a Hacker in the terminal28 março 2025
How to code like a Hacker in the terminal28 março 2025 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/m/C/yAj1AQQDG2VA89LsIptw/pexels-sora-shimazaki-5935794.jpg) Hacker Typer: o que é e como usar o simulador para fingir ser hacker28 março 2025
Hacker Typer: o que é e como usar o simulador para fingir ser hacker28 março 2025 -
 Frankenstein was a hack: the copy/paste cryptominer28 março 2025
Frankenstein was a hack: the copy/paste cryptominer28 março 2025 -
termux-tool · GitHub Topics · GitHub28 março 2025
-
 2+ Thousand Command Line Interface Royalty-Free Images, Stock Photos & Pictures28 março 2025
2+ Thousand Command Line Interface Royalty-Free Images, Stock Photos & Pictures28 março 2025 -
 4 CMD Tricks to Look Like a Hacker #shorts28 março 2025
4 CMD Tricks to Look Like a Hacker #shorts28 março 2025 -
Toturial how to hack wifi password using CMD. #cmd #command #commandpr28 março 2025
-
 Fake Hacking With Batch Files - Instructables28 março 2025
Fake Hacking With Batch Files - Instructables28 março 2025 -
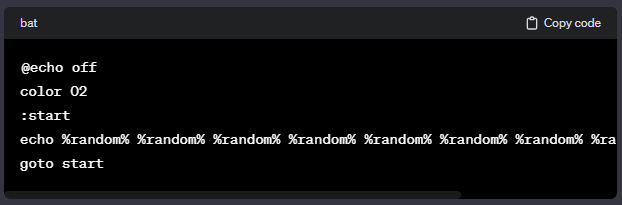 Unleashing the Power of Command Prompt: Hacks and Tricks28 março 2025
Unleashing the Power of Command Prompt: Hacks and Tricks28 março 2025 -
 How to Hack Command Prompt at school to change passwords and more28 março 2025
How to Hack Command Prompt at school to change passwords and more28 março 2025
você pode gostar
-
 Realistic Minecraft Mods Planet Minecraft Community28 março 2025
Realistic Minecraft Mods Planet Minecraft Community28 março 2025 -
 roblox brasileiro mandrake feminina|Búsqueda de TikTok28 março 2025
roblox brasileiro mandrake feminina|Búsqueda de TikTok28 março 2025 -
 COMO TIRAR o LAG do ROBLOX no CELULAR 2024 e AUMENTAR o FPS - RODAR LISO e PARAR de TRAVAR28 março 2025
COMO TIRAR o LAG do ROBLOX no CELULAR 2024 e AUMENTAR o FPS - RODAR LISO e PARAR de TRAVAR28 março 2025 -
 Menina Adolescente Infeliz Usando Fones De Ouvido Olha Tristemente28 março 2025
Menina Adolescente Infeliz Usando Fones De Ouvido Olha Tristemente28 março 2025 -
 Club Atlético Platense - Wikipedia28 março 2025
Club Atlético Platense - Wikipedia28 março 2025 -
 The King of Fighters 2002 Unlimited Match - Metacritic28 março 2025
The King of Fighters 2002 Unlimited Match - Metacritic28 março 2025 -
 Scarlett Johansson Discusses Marriage To Ryan Reynolds28 março 2025
Scarlett Johansson Discusses Marriage To Ryan Reynolds28 março 2025 -
 Rumor afirma que Hellblade 2 chega “logo após” Starfield28 março 2025
Rumor afirma que Hellblade 2 chega “logo após” Starfield28 março 2025 -
 Don't know if this is rare, perfect IV Meloetta. : r/pokemongobrag28 março 2025
Don't know if this is rare, perfect IV Meloetta. : r/pokemongobrag28 março 2025 -
 call of duty modern warfare 2 highly compressed download for pc - 3.85GB28 março 2025
call of duty modern warfare 2 highly compressed download for pc - 3.85GB28 março 2025
