How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 15 fevereiro 2025
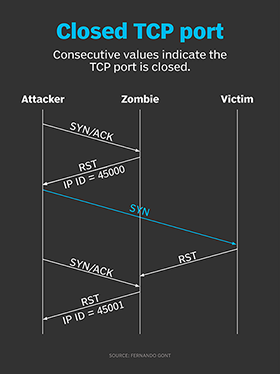
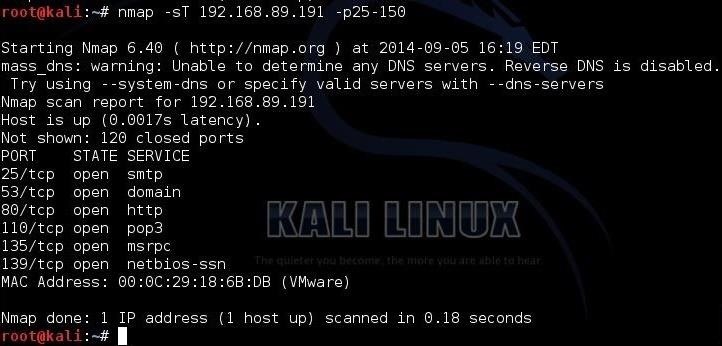
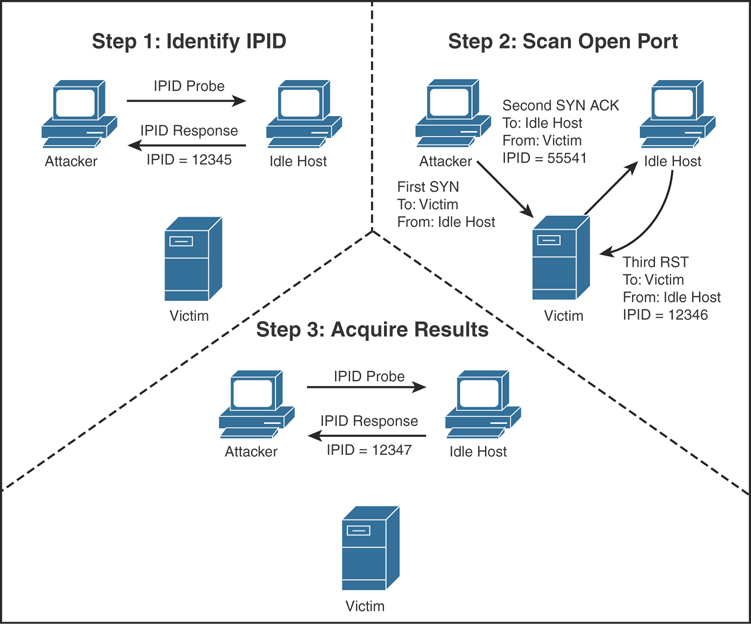
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hack Like a Pro: Advanced Nmap for Reconnaissance « Null Byte :: WonderHowTo
Applied Network Security
Scanning, Footprinting, Reconnaissance, and Scanning

How to hide yourself using Idle scan (-sl) - Port scanning tutorial
Ethical Hacking: Scanning Networks (2016) Online Class

NMap 101: Fun With Firewalls! HakTip 102
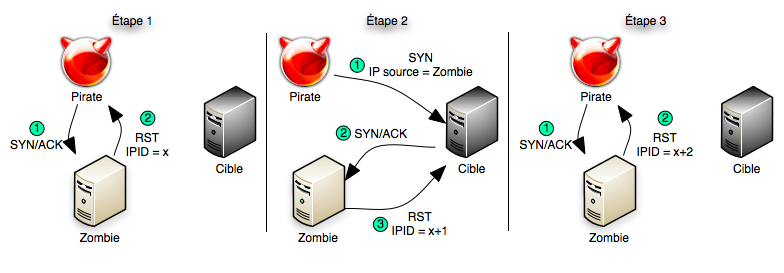
Idle scan - Wikipedia
Port Scanning based Attacks
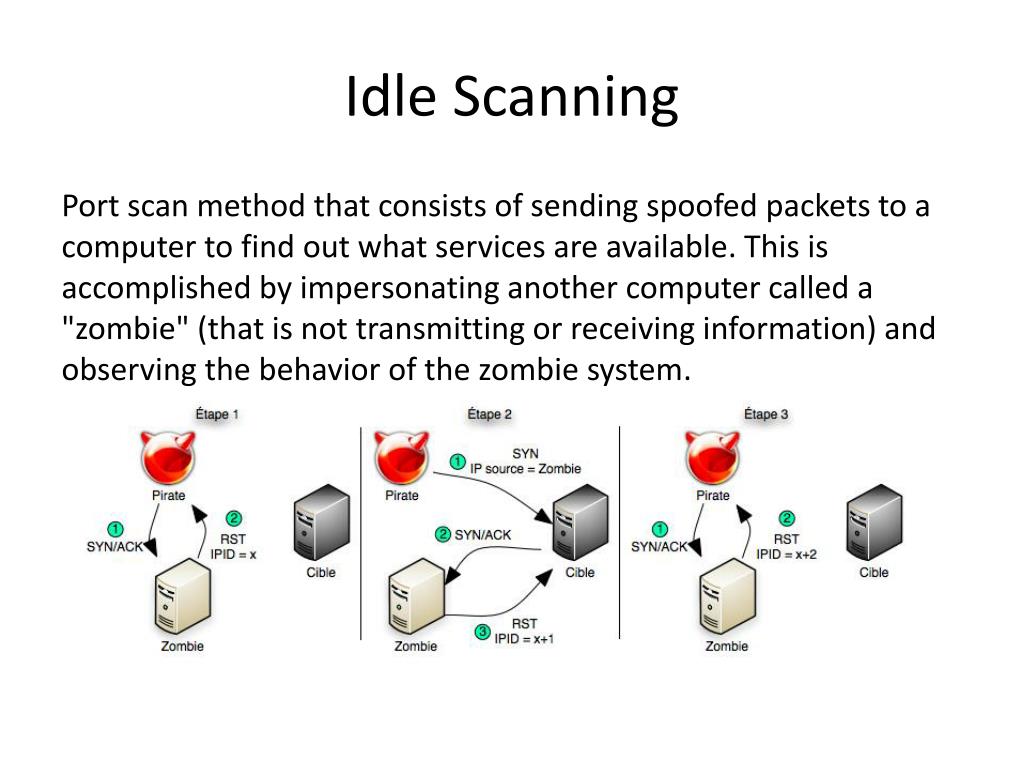
PPT - Port Scanning PowerPoint Presentation, free download - ID:1577632
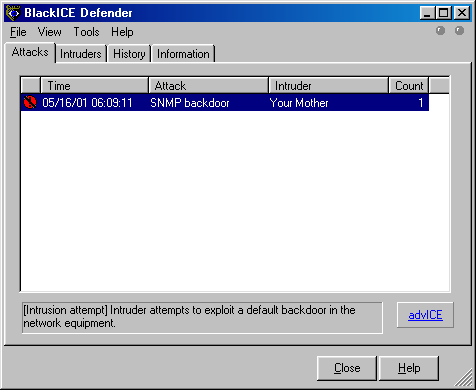
Subverting Intrusion Detection Systems
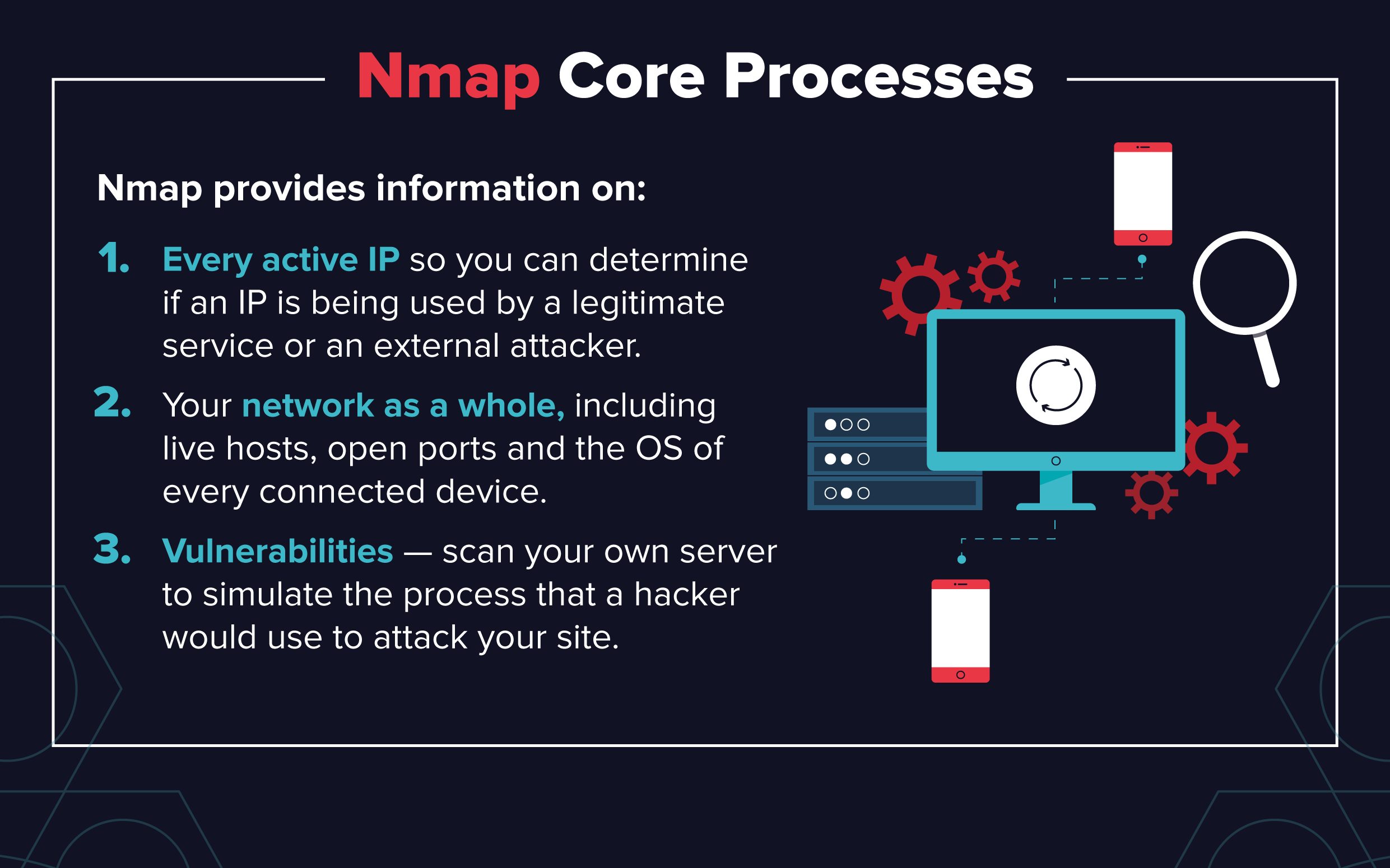
Essential Nmap Commands for System Admins - Penetration Testing Tools, ML and Linux Tutorials
Recomendado para você
-
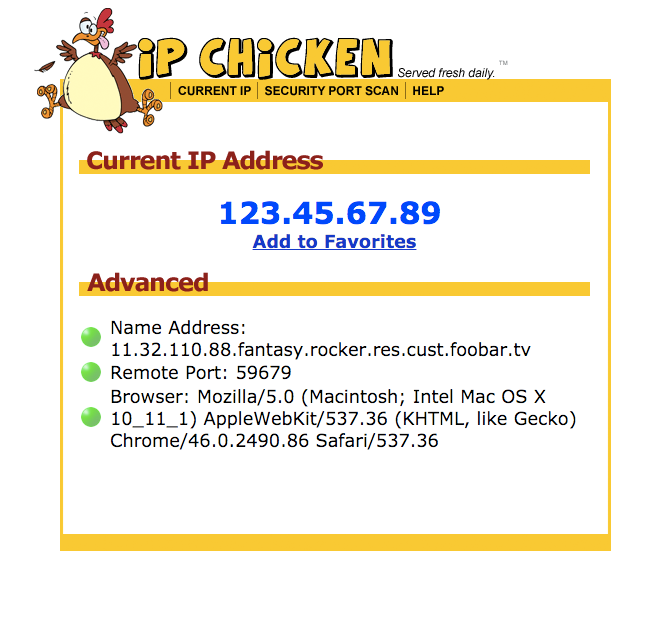 Show Your Public IP - Restreamer15 fevereiro 2025
Show Your Public IP - Restreamer15 fevereiro 2025 -
USGPRO4: 'The gateway is unable to connect to the Internet' - but it is15 fevereiro 2025
-
Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly15 fevereiro 2025
-
174.218.138.250 is a publicly routable IP address is it not?15 fevereiro 2025
-
![Zscaler- Source IP Anchoring [SIPA]](https://i.ytimg.com/vi/ylt74TZnS2Q/hq720.jpg?sqp=-oaymwE7CK4FEIIDSFryq4qpAy0IARUAAAAAGAElAADIQj0AgKJD8AEB-AH-CIAC0AWKAgwIABABGDwgEyh_MA8=&rs=AOn4CLAOEq5hhRYj-Kw0ehVImE5Q4ZxLDQ) Zscaler- Source IP Anchoring [SIPA]15 fevereiro 2025
Zscaler- Source IP Anchoring [SIPA]15 fevereiro 2025 -
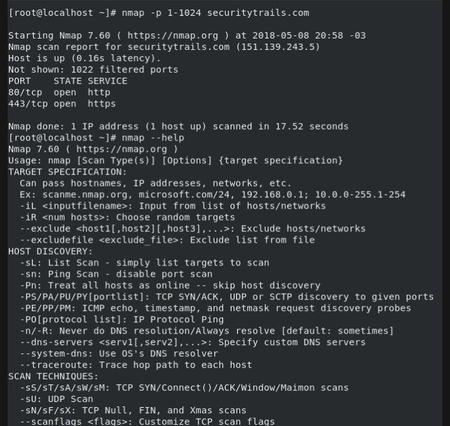 Top 5 Most Popular Port Scanners in CyberSecurity15 fevereiro 2025
Top 5 Most Popular Port Scanners in CyberSecurity15 fevereiro 2025 -
 Port Scan in Ethical Hacking - GeeksforGeeks15 fevereiro 2025
Port Scan in Ethical Hacking - GeeksforGeeks15 fevereiro 2025 -
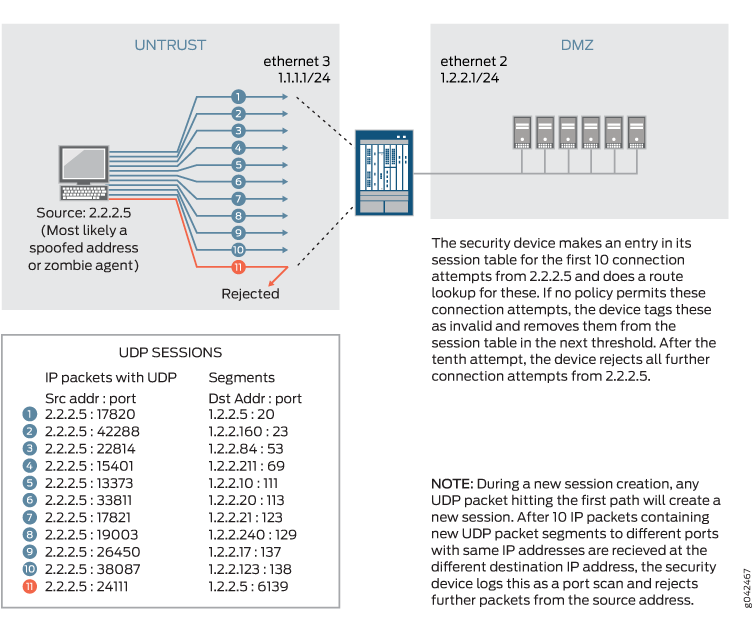 IP Address Sweep and Port Scan, Junos OS15 fevereiro 2025
IP Address Sweep and Port Scan, Junos OS15 fevereiro 2025 -
 Port Scanning Techniques: An Introduction15 fevereiro 2025
Port Scanning Techniques: An Introduction15 fevereiro 2025 -
 10 Best Port Scanner Tools for Network Security - Geekflare15 fevereiro 2025
10 Best Port Scanner Tools for Network Security - Geekflare15 fevereiro 2025
você pode gostar
-
 How to Send the Perfect Friendly Reminder Email (Without Being Annoying)15 fevereiro 2025
How to Send the Perfect Friendly Reminder Email (Without Being Annoying)15 fevereiro 2025 -
 How to Make a Spider Web Out of Rope & Knots15 fevereiro 2025
How to Make a Spider Web Out of Rope & Knots15 fevereiro 2025 -
 10 of the Best Game Boy Advance (GBA) Emulators for Android - Make Tech Easier15 fevereiro 2025
10 of the Best Game Boy Advance (GBA) Emulators for Android - Make Tech Easier15 fevereiro 2025 -
 JOGO DO BICHO free online game on15 fevereiro 2025
JOGO DO BICHO free online game on15 fevereiro 2025 -
 Boruto ࿐ྂ。, @ame_anime15 fevereiro 2025
Boruto ࿐ྂ。, @ame_anime15 fevereiro 2025 -
My Kingdom15 fevereiro 2025
-
 Pokemon Dark Energy - Play Game Online15 fevereiro 2025
Pokemon Dark Energy - Play Game Online15 fevereiro 2025 -
 Elite' é renovada para a 6ª temporada na Netflix15 fevereiro 2025
Elite' é renovada para a 6ª temporada na Netflix15 fevereiro 2025 -
 Noragami Aragoto - Hey Kids!! (Opening), ENGLISH ver, AmaLee, Good songs from anime (the anime that i know)15 fevereiro 2025
Noragami Aragoto - Hey Kids!! (Opening), ENGLISH ver, AmaLee, Good songs from anime (the anime that i know)15 fevereiro 2025 -
 Sonic the Hedgehog para Game Gear (1991)15 fevereiro 2025
Sonic the Hedgehog para Game Gear (1991)15 fevereiro 2025
![Crossfire Philippines - [Notice] Data Transmission Error - Info Gathering Hello Mercenaries! We would like to ask some assistance to further address the issue regarding the Data Transmission Error. This will greatly](https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=2958303717738978)
