Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 16 junho 2024
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

Your IT Provider Is Letting Hackers Into Your Business”

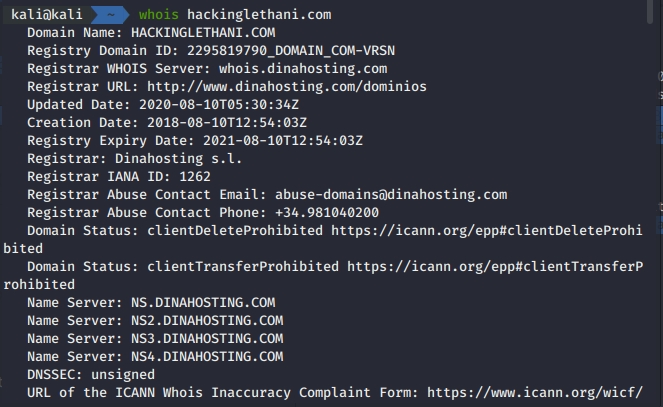
Whois Lookup Ethical Hacking

Infrastructure Hacking: DNS Protocol II » Hacking Lethani

Tips for Investigating Cybercrime Infrastructure

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack

Tips for Investigating Cybercrime Infrastructure

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Understanding Linux Privilege Escalation: Tips to Improve Cy
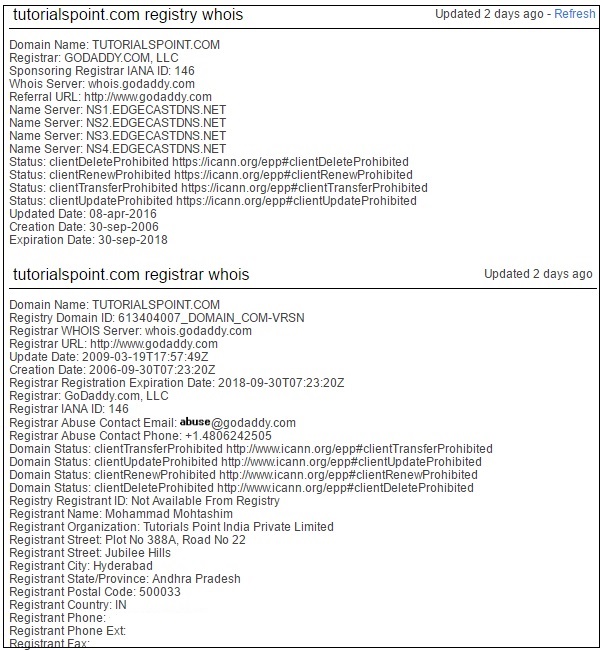
Ethical Hacking - Quick Guide
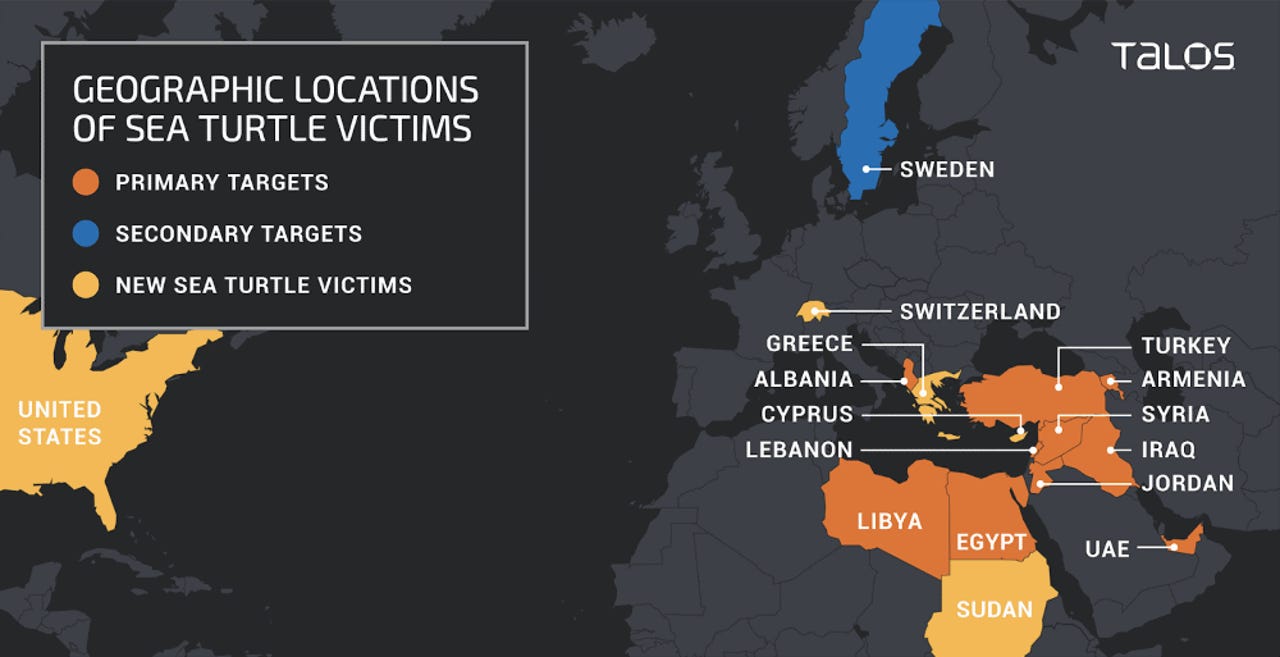
Hackers breached Greece's top-level domain registrar

Whois Lookup Ethical Hacking

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting
Recomendado para você
-
 Domain Names & Identity for Everyone16 junho 2024
Domain Names & Identity for Everyone16 junho 2024 -
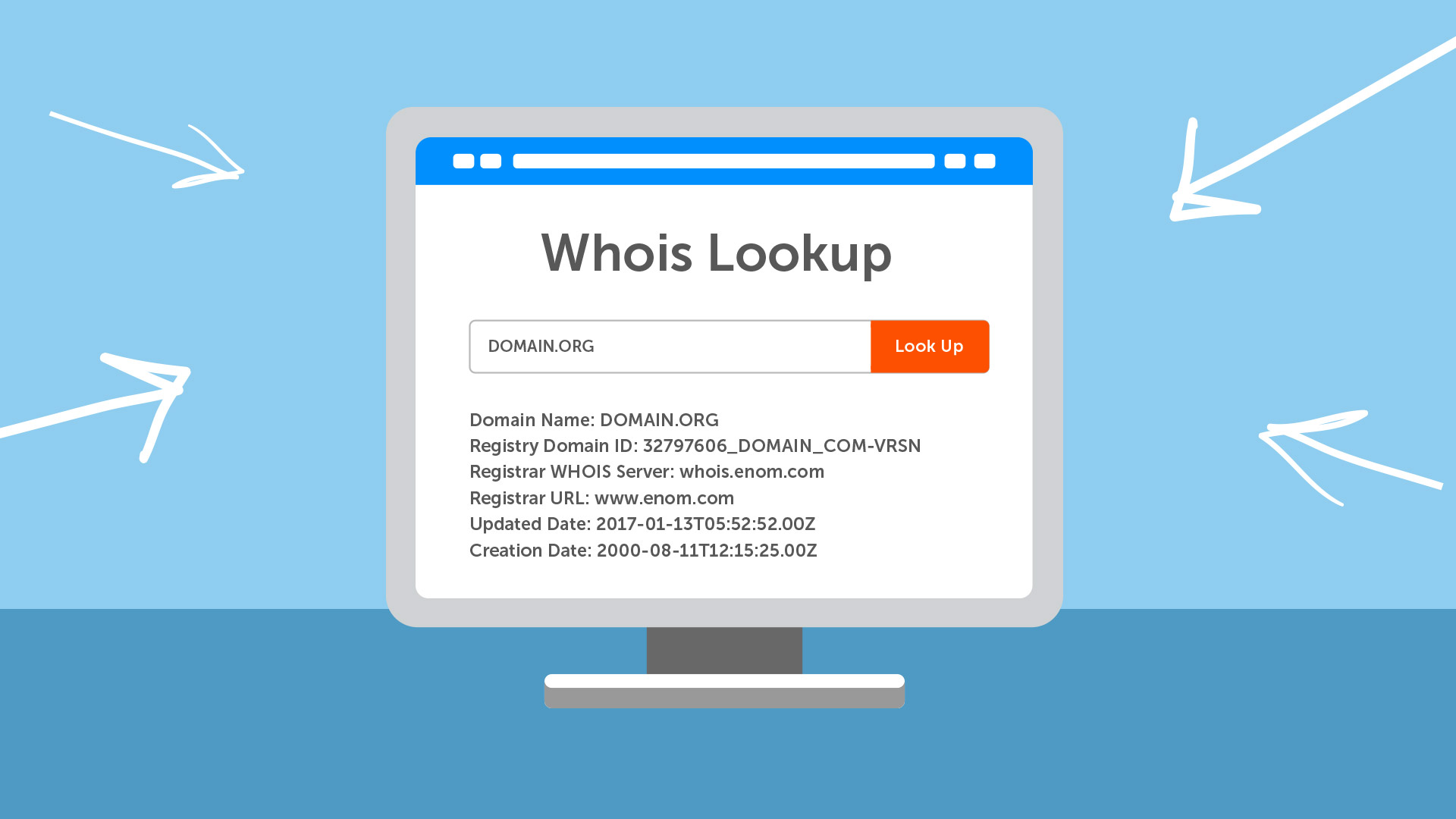 The WHOIS Database16 junho 2024
The WHOIS Database16 junho 2024 -
 How To Find Whois Domain Information from Command Line16 junho 2024
How To Find Whois Domain Information from Command Line16 junho 2024 -
 What is WHOIS and How Is It Used?16 junho 2024
What is WHOIS and How Is It Used?16 junho 2024 -
 Domain WHOIS Search - cdmon16 junho 2024
Domain WHOIS Search - cdmon16 junho 2024 -
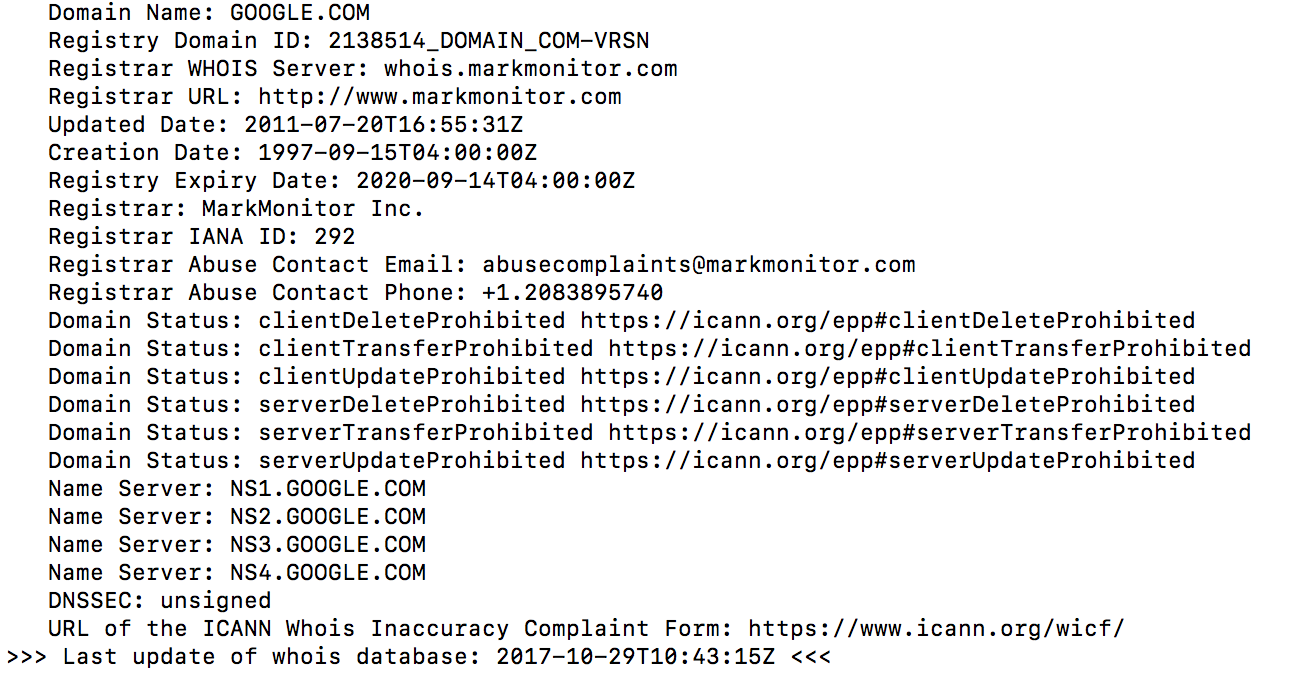 All you need to know about Linux whois command (domain lookup16 junho 2024
All you need to know about Linux whois command (domain lookup16 junho 2024 -
 How to Find a Domain Name Owner w/ WHOIS Lookup (for free)16 junho 2024
How to Find a Domain Name Owner w/ WHOIS Lookup (for free)16 junho 2024 -
 Domain whois State / Country not private - Registrar - Cloudflare16 junho 2024
Domain whois State / Country not private - Registrar - Cloudflare16 junho 2024 -
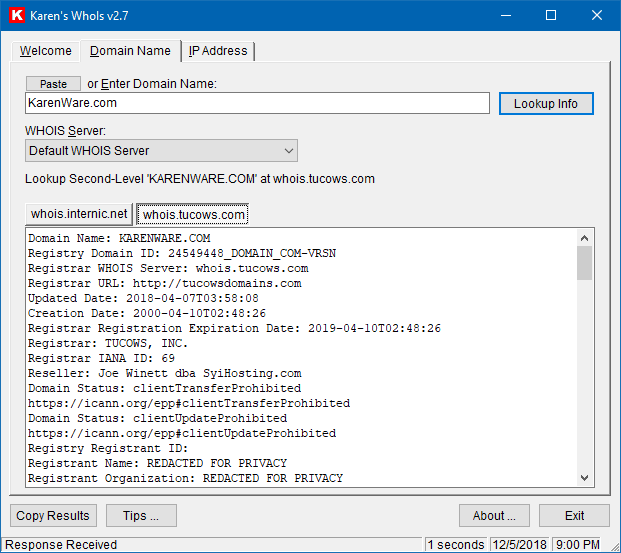 WhoIs v2.7, Karen's Power Tools16 junho 2024
WhoIs v2.7, Karen's Power Tools16 junho 2024 -
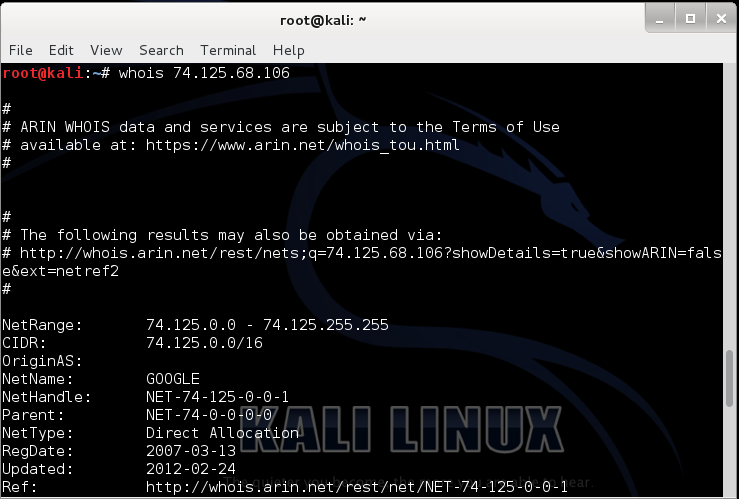 Understanding the Power of Whois Command in Kali Linux16 junho 2024
Understanding the Power of Whois Command in Kali Linux16 junho 2024
você pode gostar
-
 My honkai star rail characters tierlist from my most wanted character to the least Honkai: Star Rail16 junho 2024
My honkai star rail characters tierlist from my most wanted character to the least Honkai: Star Rail16 junho 2024 -
 Download 1966 Chevrolet Nova Drag Car, FiveM Ready, Single Player Ready16 junho 2024
Download 1966 Chevrolet Nova Drag Car, FiveM Ready, Single Player Ready16 junho 2024 -
naruto clássico ep 23 em português|Pesquisa do TikTok16 junho 2024
-
 IFOYO Multi Function 4 in 1 Combo Folding Game Table, Steady Pool Table, Hockey Table, Soccer Football Table, Table Tennis Table, Ideal, Birthday Gift, 48in (Yellow Flame)16 junho 2024
IFOYO Multi Function 4 in 1 Combo Folding Game Table, Steady Pool Table, Hockey Table, Soccer Football Table, Table Tennis Table, Ideal, Birthday Gift, 48in (Yellow Flame)16 junho 2024 -
 São Paulo FC - Wikiwand16 junho 2024
São Paulo FC - Wikiwand16 junho 2024 -
 Volume 9 (Light Novel), Assassins Pride Wiki, Fandom16 junho 2024
Volume 9 (Light Novel), Assassins Pride Wiki, Fandom16 junho 2024 -
Poppy Playtime Ch. 2 (Original Game Soundtrack) - Album by MOB16 junho 2024
-
 GTA MTA RP🔵 DESTINY RP 💙01 DA FAC DE RUA ONN💙 VEM RESENHAR COLAAA16 junho 2024
GTA MTA RP🔵 DESTINY RP 💙01 DA FAC DE RUA ONN💙 VEM RESENHAR COLAAA16 junho 2024 -
 Overwatch 2's One-Punch Man Collaboration Is Now Live: Doomfist Fashioned After Saitama, More Details16 junho 2024
Overwatch 2's One-Punch Man Collaboration Is Now Live: Doomfist Fashioned After Saitama, More Details16 junho 2024 -
 Lavanda Isolado Desenho Ilustração Elemento Desenhado Mão Para Ervas Casamento imagem vetorial de AcantStudio© 50738180416 junho 2024
Lavanda Isolado Desenho Ilustração Elemento Desenhado Mão Para Ervas Casamento imagem vetorial de AcantStudio© 50738180416 junho 2024

