Cryptographic Keys 101: What They Are & How They Secure Data - Hashed Out by The SSL Store™
Por um escritor misterioso
Last updated 19 novembro 2024

Cryptographic keys, in combination with an encryption algorithm, disguise data (encryption) so only a special key can access it (decryption).

Cryptography 101: Key Principles, Major Types, Use Cases

Hashing vs. Encryption: Definitions & Differences - Okta SG
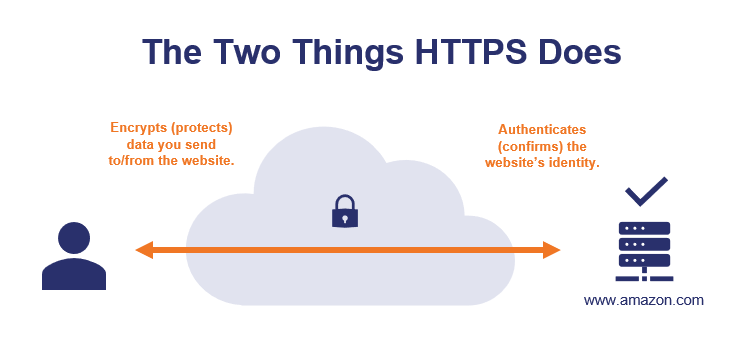
How Does HTTPS Work? - Security Boulevard
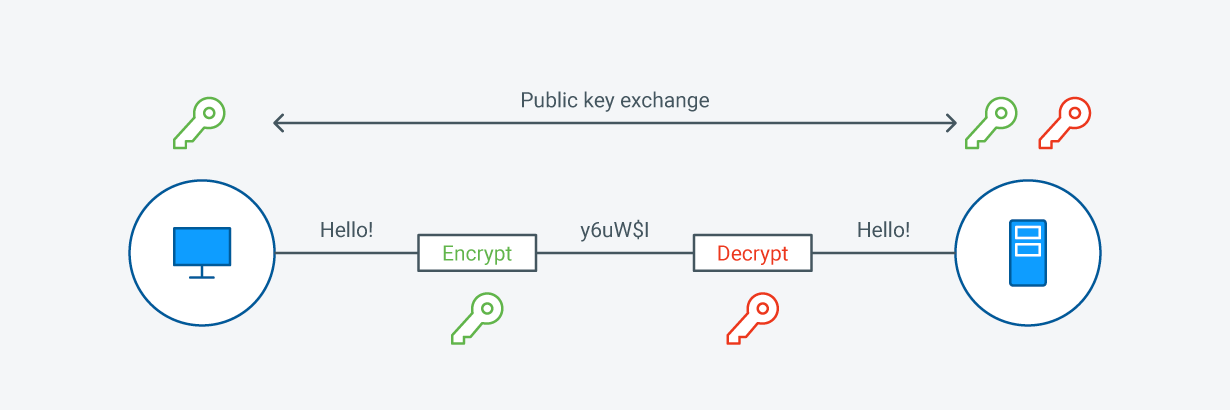
What is SSL Cryptography?
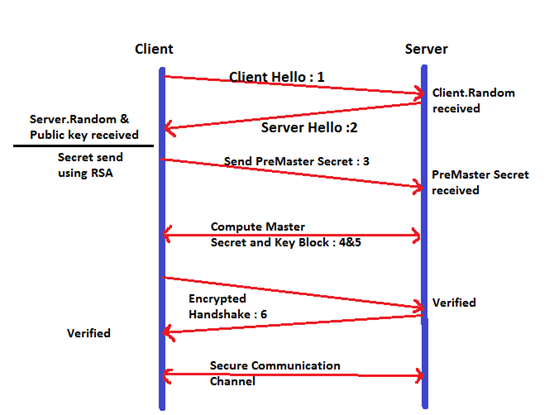
Cryptography 101 with SSL
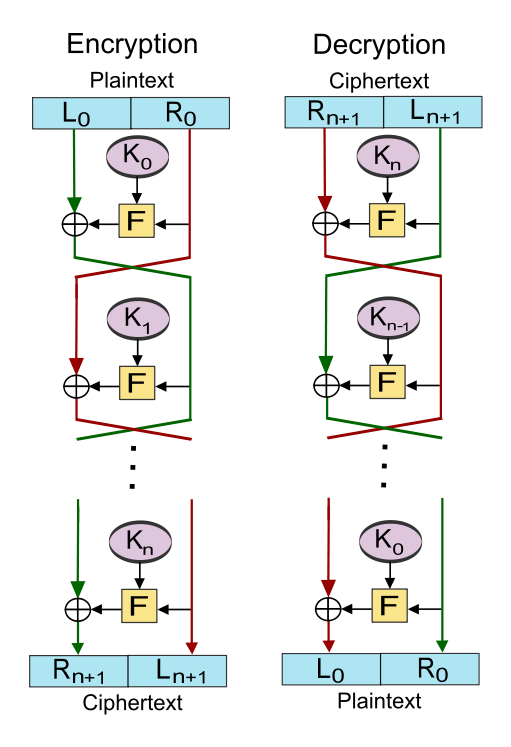
An Overview of Cryptography

PII Encryption Protect Your Customer's Privacy

The SSL Store: What Is a Hash Function in Cryptography? A

Future Solutions Poster - Cybersecurity, PDF, Encryption
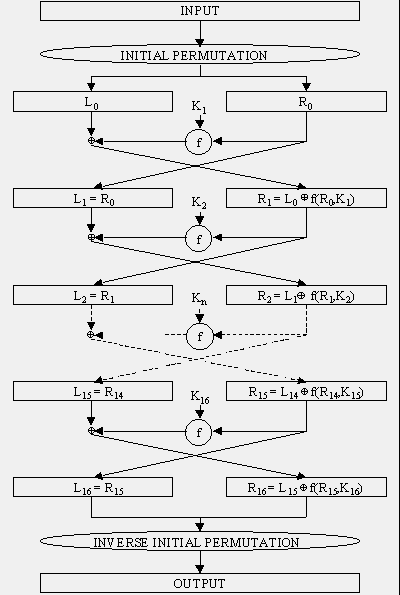
An Overview of Cryptography
Recomendado para você
-
 Dog Door Keys, Accessories19 novembro 2024
Dog Door Keys, Accessories19 novembro 2024 -
 Antique Finish Barrel Key For Furniture Locks19 novembro 2024
Antique Finish Barrel Key For Furniture Locks19 novembro 2024 -
 Clever Organisation for Better Living – Orbitkey19 novembro 2024
Clever Organisation for Better Living – Orbitkey19 novembro 2024 -
 B. toys – Toy Car Keys – Key Fob with Lights & Sounds – Interactive Baby Toy – Pretend Keys for Babies, Toddlers – 10 Months + – FunKeys – Purple19 novembro 2024
B. toys – Toy Car Keys – Key Fob with Lights & Sounds – Interactive Baby Toy – Pretend Keys for Babies, Toddlers – 10 Months + – FunKeys – Purple19 novembro 2024 -
 Wicked Keys19 novembro 2024
Wicked Keys19 novembro 2024 -
 Tiffany Keys Crown Key in Yellow Gold with Diamonds, 1.519 novembro 2024
Tiffany Keys Crown Key in Yellow Gold with Diamonds, 1.519 novembro 2024 -
 Key Cutting Key Copy Checker - FobToronto19 novembro 2024
Key Cutting Key Copy Checker - FobToronto19 novembro 2024 -
 8 Interesting Facts About the Florida Keys19 novembro 2024
8 Interesting Facts About the Florida Keys19 novembro 2024 -
 Keys Photos, Download The BEST Free Keys Stock Photos & HD Images19 novembro 2024
Keys Photos, Download The BEST Free Keys Stock Photos & HD Images19 novembro 2024 -
 Global Link Replacement Keys19 novembro 2024
Global Link Replacement Keys19 novembro 2024
você pode gostar
-
 Chess: An Easy-to-follow Illustrated Guide to Playing This Popular Game of Skill19 novembro 2024
Chess: An Easy-to-follow Illustrated Guide to Playing This Popular Game of Skill19 novembro 2024 -
 The Last Guardian: Procedural Animation - Game Anim19 novembro 2024
The Last Guardian: Procedural Animation - Game Anim19 novembro 2024 -
 Pin de Toni 🌀 em G I F Como criar gif, Memes gretchen, Gif risada19 novembro 2024
Pin de Toni 🌀 em G I F Como criar gif, Memes gretchen, Gif risada19 novembro 2024 -
 Quando é a final da Champions League 2023? Veja calendário19 novembro 2024
Quando é a final da Champions League 2023? Veja calendário19 novembro 2024 -
 Rooms in the House Cut and Paste Page19 novembro 2024
Rooms in the House Cut and Paste Page19 novembro 2024 -
 Fidelity Bank Shelby, NC — Branch & ATM Location19 novembro 2024
Fidelity Bank Shelby, NC — Branch & ATM Location19 novembro 2024 -
 INTIMIDADE NO TELEFONE EMBRULHA PRA VIAGEM19 novembro 2024
INTIMIDADE NO TELEFONE EMBRULHA PRA VIAGEM19 novembro 2024 -
 O jogo Super Mario Bros da Nintendo de 1985 – MCC - Museu Capixaba do Computador19 novembro 2024
O jogo Super Mario Bros da Nintendo de 1985 – MCC - Museu Capixaba do Computador19 novembro 2024 -
 The Mimic, Triple A Fazbear Wiki, Fandom in 202319 novembro 2024
The Mimic, Triple A Fazbear Wiki, Fandom in 202319 novembro 2024 -
Mako Mermaids - Season 319 novembro 2024
