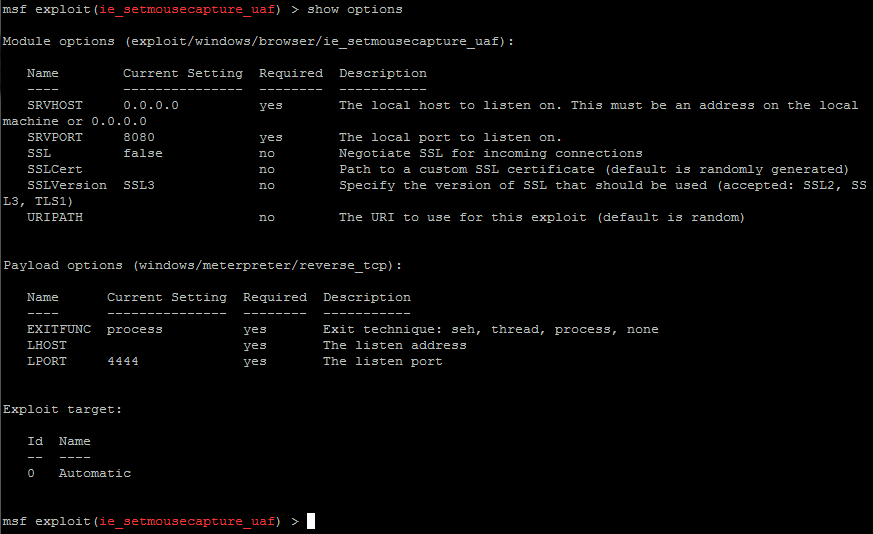
Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 14 novembro 2024
Applied Sciences, Free Full-Text
Blog for and by my students, current and future: Exploiting and

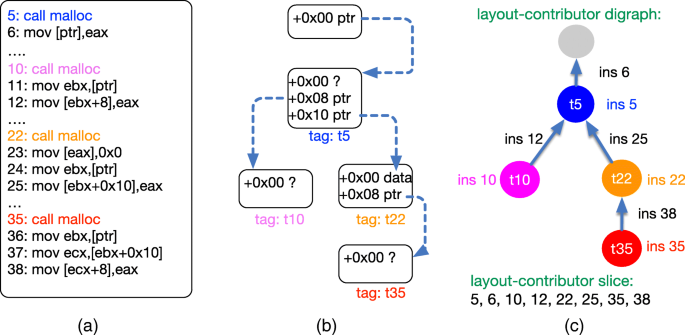
Pwnable-Sherpa: An interactive coaching system with a case study

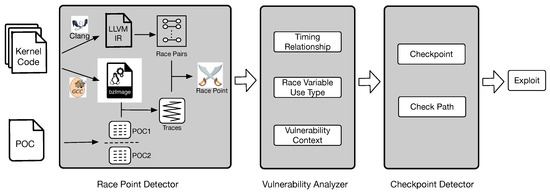
The components of Dr. Memory. The original application's code is
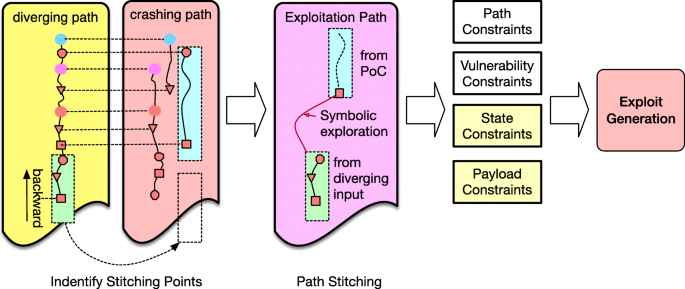
From proof-of-concept to exploitable, Cybersecurity
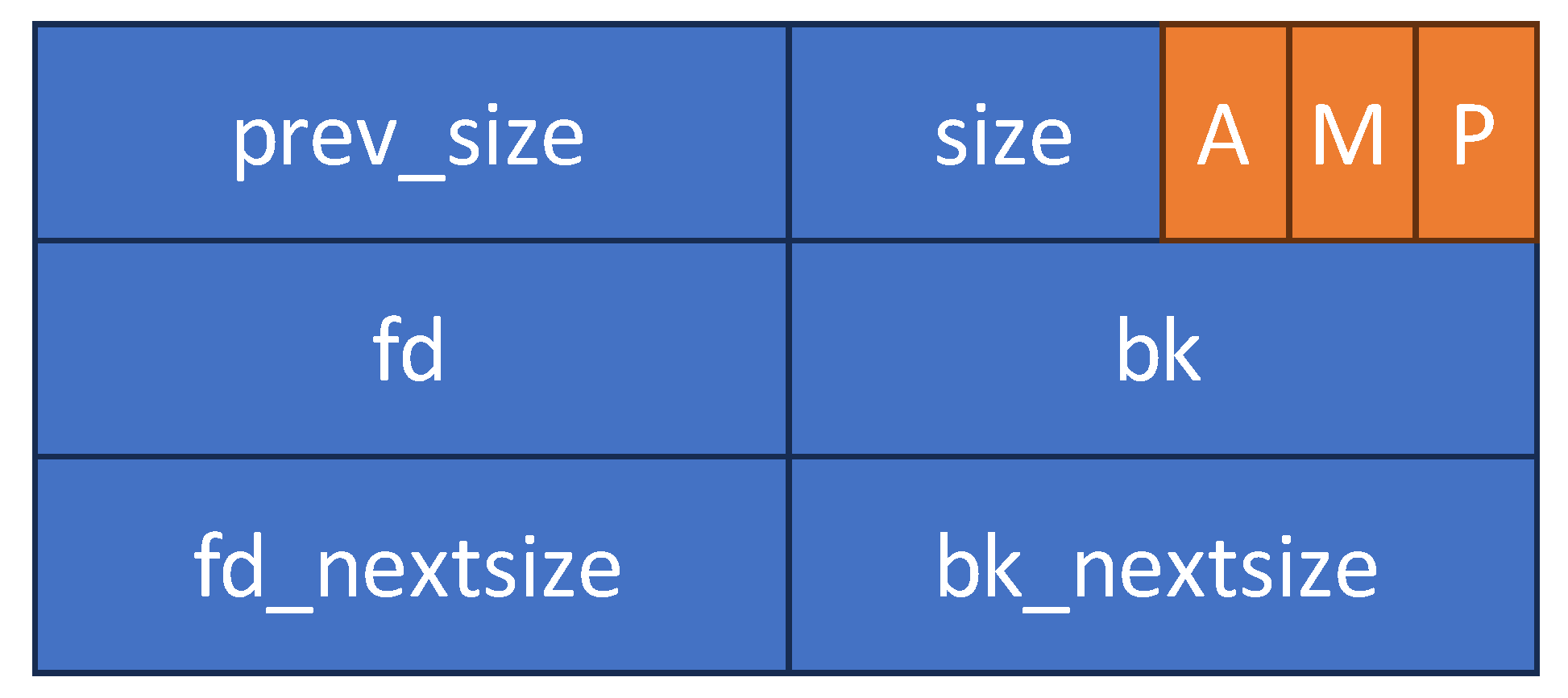
Symmetry, Free Full-Text
From proof-of-concept to exploitable, Cybersecurity
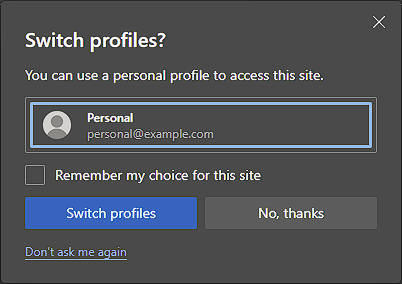
Guest Blog Post - Memory corruption vulnerabilities in Edge
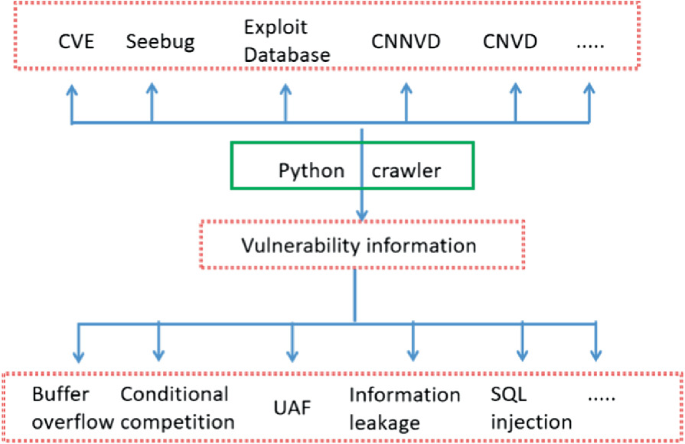
Establishment of Vulnerability Sample Database in Network Attack

Pwnable-Sherpa: An interactive coaching system with a case study
x86 and Secure Software Design 2023 - UD Capture
Recomendado para você
-
Steam Workshop::gmod fnaf horror14 novembro 2024
-
 KING LEGACY – ScriptPastebin14 novembro 2024
KING LEGACY – ScriptPastebin14 novembro 2024 -
 King Legacy Script Auto Farm, Auto Quest14 novembro 2024
King Legacy Script Auto Farm, Auto Quest14 novembro 2024 -
 History Archives - The Atavist Magazine14 novembro 2024
History Archives - The Atavist Magazine14 novembro 2024 -
 king legacy script fluxus – ScriptPastebin14 novembro 2024
king legacy script fluxus – ScriptPastebin14 novembro 2024 -
 One X Hub King Legacy Script14 novembro 2024
One X Hub King Legacy Script14 novembro 2024 -
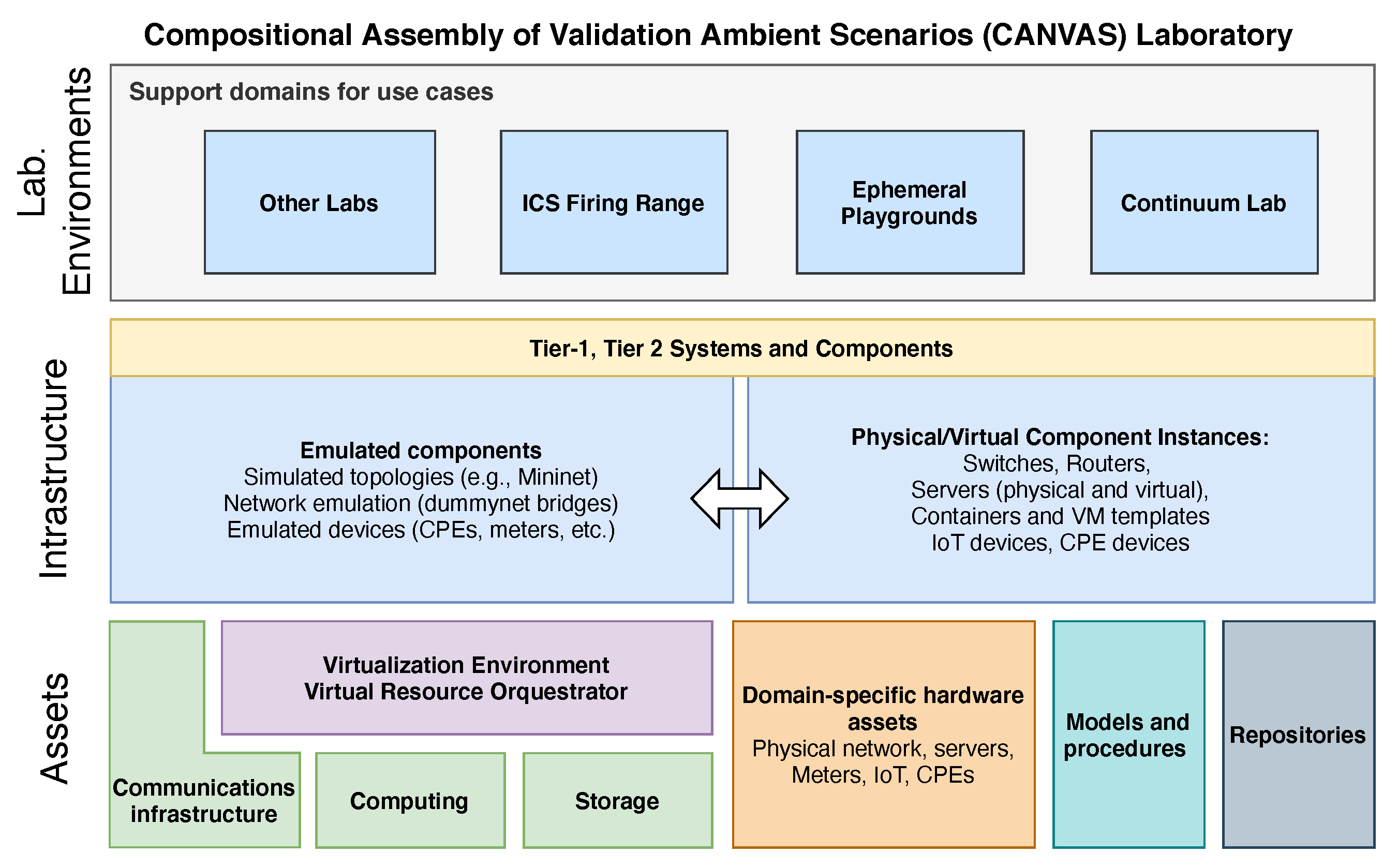 Applied Sciences, Free Full-Text14 novembro 2024
Applied Sciences, Free Full-Text14 novembro 2024 -
 University of California, Berkeley - Wikipedia14 novembro 2024
University of California, Berkeley - Wikipedia14 novembro 2024 -
 Course DesCriptions - University Catalogs - University of Minnesota14 novembro 2024
Course DesCriptions - University Catalogs - University of Minnesota14 novembro 2024 -
 Calaméo - ESRAmagazine Issue 213 July 202214 novembro 2024
Calaméo - ESRAmagazine Issue 213 July 202214 novembro 2024
você pode gostar
-
 Gordon's Fish & Chips in 10 Minutes » Gordon Ramsay.com14 novembro 2024
Gordon's Fish & Chips in 10 Minutes » Gordon Ramsay.com14 novembro 2024 -
 Crash Team Rumble Review — Hot Gamers Only14 novembro 2024
Crash Team Rumble Review — Hot Gamers Only14 novembro 2024 -
UK government closes tax loophole on digital media, could mean the14 novembro 2024
-
 Fallout New Vegas: Mods and tips for the best experience14 novembro 2024
Fallout New Vegas: Mods and tips for the best experience14 novembro 2024 -
VR action games >> 10 titles we can't wait for14 novembro 2024
-
 Gabbi Tuft - Wikipedia14 novembro 2024
Gabbi Tuft - Wikipedia14 novembro 2024 -
Village City Town Building Sim Ver. 2.1.1 MOD APK, Unlimited Cash14 novembro 2024
-
 Barber Shop Flyer Template14 novembro 2024
Barber Shop Flyer Template14 novembro 2024 -
Legends Never Die — Friends, gif dump 2714 novembro 2024
-
 Carlsen moves closer to the leader after 10 rounds of the Tata14 novembro 2024
Carlsen moves closer to the leader after 10 rounds of the Tata14 novembro 2024