Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Last updated 26 fevereiro 2025

The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
The Attack Path Management Manifesto, by Andy Robbins

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles

Indirect Command Execution – Penetration Testing Lab

How prepared is the world? Identifying weaknesses in existing assessment frameworks for global health security through a One Health approach - The Lancet
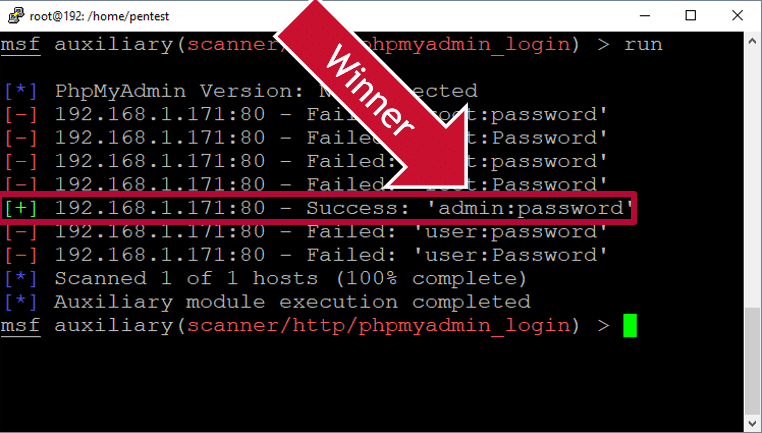
Linux Hacking Case Studies Part 3: phpMyAdmin

Indirect Command Execution
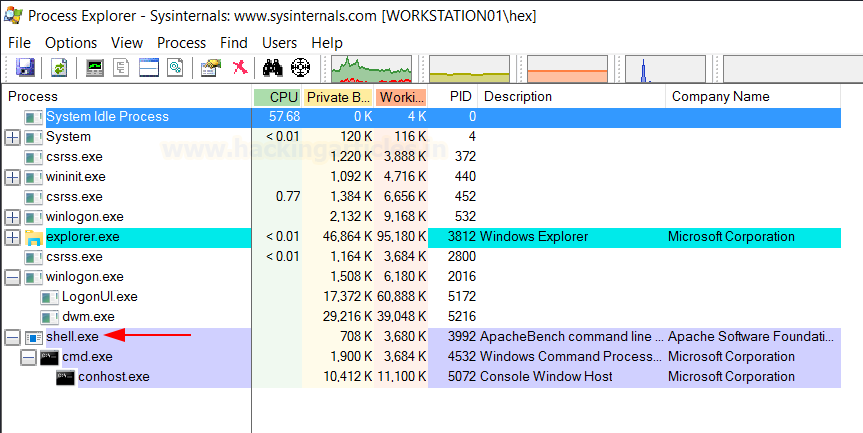
Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles

CVE-2021-31956 Exploiting the Windows Kernel (NTFS with WNF) – Part 2, NCC Group Research Blog

Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
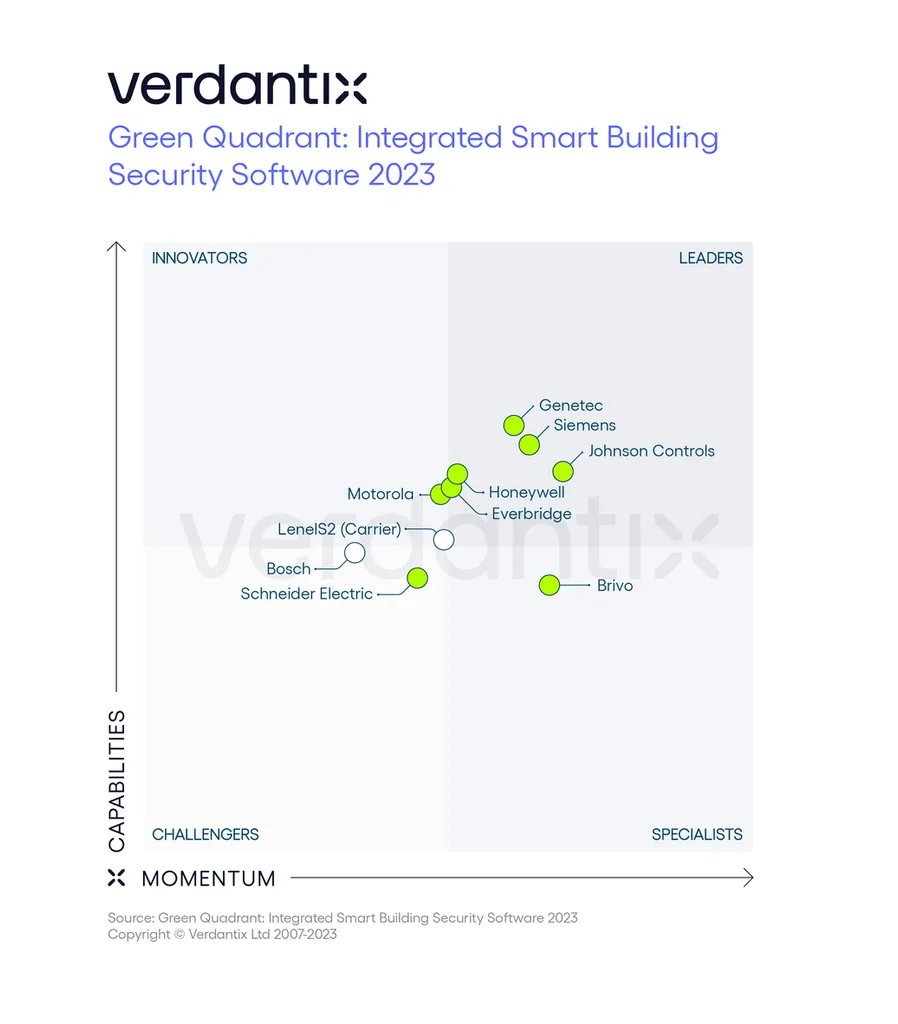
Siemens ranked as a leader in security software for smart buildings, Press, Company

T1202: Indirect Command Execution - Red Team Notes 2.0
Kali Linux Penetration Testing Tutorial: How to Use Kali Linux

TryHackMe Hacktivities
Recomendado para você
-
 Use the System File Checker tool to repair missing or corrupted26 fevereiro 2025
Use the System File Checker tool to repair missing or corrupted26 fevereiro 2025 -
 Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution26 fevereiro 2025
Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution26 fevereiro 2025 -
How to run an EXE from command prompt - Quora26 fevereiro 2025
-
 How do I launch a program from command line without opening a new cmd window? - Stack Overflow26 fevereiro 2025
How do I launch a program from command line without opening a new cmd window? - Stack Overflow26 fevereiro 2025 -
 c++ - How do I run an exe file from cmd but in the same window? - Stack Overflow26 fevereiro 2025
c++ - How do I run an exe file from cmd but in the same window? - Stack Overflow26 fevereiro 2025 -
 Use PowerShell to execute an exe – 4sysops26 fevereiro 2025
Use PowerShell to execute an exe – 4sysops26 fevereiro 2025 -
 How to run CMD command on startup automatically in Windows 11/1026 fevereiro 2025
How to run CMD command on startup automatically in Windows 11/1026 fevereiro 2025 -
 How to execute an SSIS package from the command line or a batch file – SQLServerCentral26 fevereiro 2025
How to execute an SSIS package from the command line or a batch file – SQLServerCentral26 fevereiro 2025 -
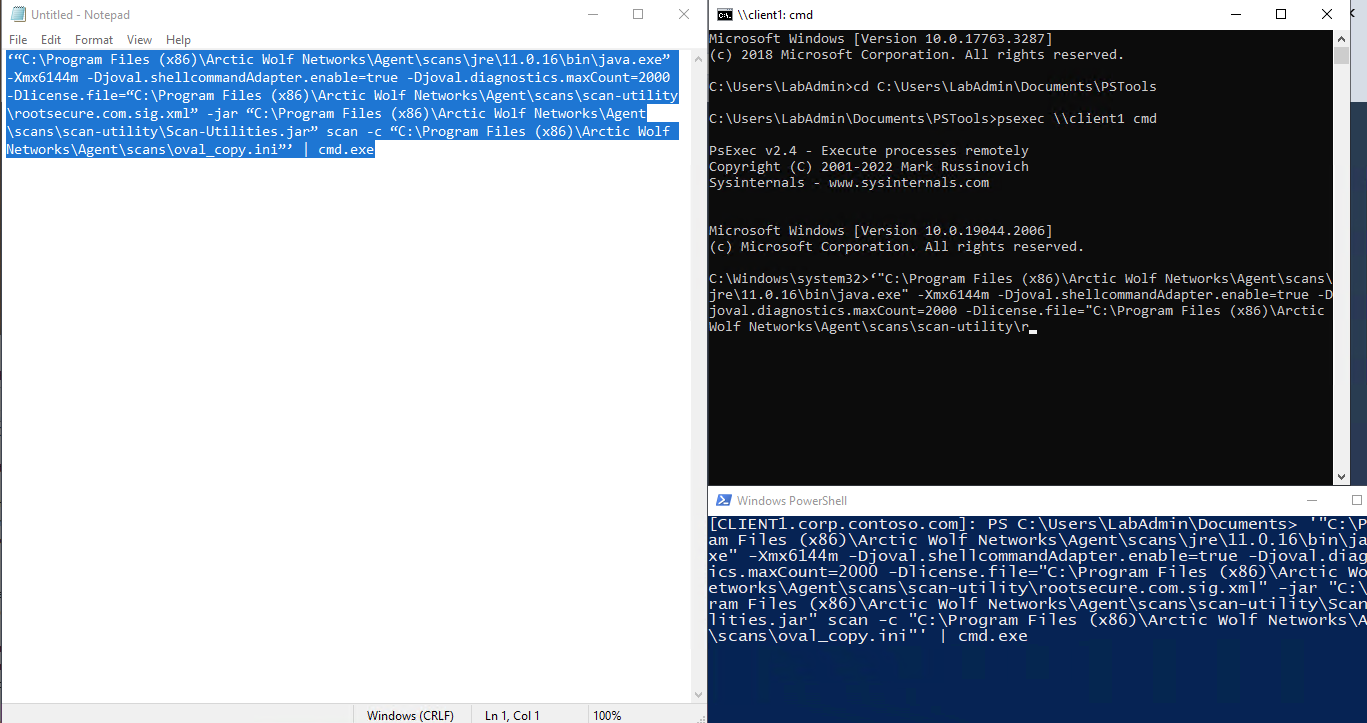 Interactive CMD Prompt Character Length - Right Click Tools- Community - Recast Software Discourse26 fevereiro 2025
Interactive CMD Prompt Character Length - Right Click Tools- Community - Recast Software Discourse26 fevereiro 2025 -
 Launching a Windows `.exe` File, Knowledge Base26 fevereiro 2025
Launching a Windows `.exe` File, Knowledge Base26 fevereiro 2025
você pode gostar
-
 Bocchi imita a Kita-san Bocchi the Rock!26 fevereiro 2025
Bocchi imita a Kita-san Bocchi the Rock!26 fevereiro 2025 -
Puro Axé - Ser Empata Os Empatas são pessoas com uma sensibilidade extrema e que conseguem sentir as energias do ambiente e das pessoas que as cercam. Costumam ter grandes variações de26 fevereiro 2025
-
Saiba como resgatar a sua Jaqueta - Garena Free Fire26 fevereiro 2025
-
 CLEARANCE - The Sicilian Flank Game26 fevereiro 2025
CLEARANCE - The Sicilian Flank Game26 fevereiro 2025 -
 Bolas e Xis! Tic Tac Logic #326 fevereiro 2025
Bolas e Xis! Tic Tac Logic #326 fevereiro 2025 -
 Kill You Cat Meme Generator - Piñata Farms - The best meme generator and meme maker for video & image memes26 fevereiro 2025
Kill You Cat Meme Generator - Piñata Farms - The best meme generator and meme maker for video & image memes26 fevereiro 2025 -
Respondendo a @senhor_blacky Dia 20 do meu clube dos emos: se você26 fevereiro 2025
-
 Legends Of The National Parks: Grand Canyon's Rake26 fevereiro 2025
Legends Of The National Parks: Grand Canyon's Rake26 fevereiro 2025 -
 Morre Just Fontaine, maior artilheiro da Copa do Mundo, que26 fevereiro 2025
Morre Just Fontaine, maior artilheiro da Copa do Mundo, que26 fevereiro 2025 -
 GTA 5 Guide - IGN26 fevereiro 2025
GTA 5 Guide - IGN26 fevereiro 2025


