Tricks and COMfoolery: How Ursnif (Gozi) Evades Detection
Por um escritor misterioso
Last updated 28 janeiro 2025

In February we saw a resurgence of Ursnif (also known as Gozi), a credential-stealing Trojan. Learn how Ursnif bypasses an attack surface reduction rule.
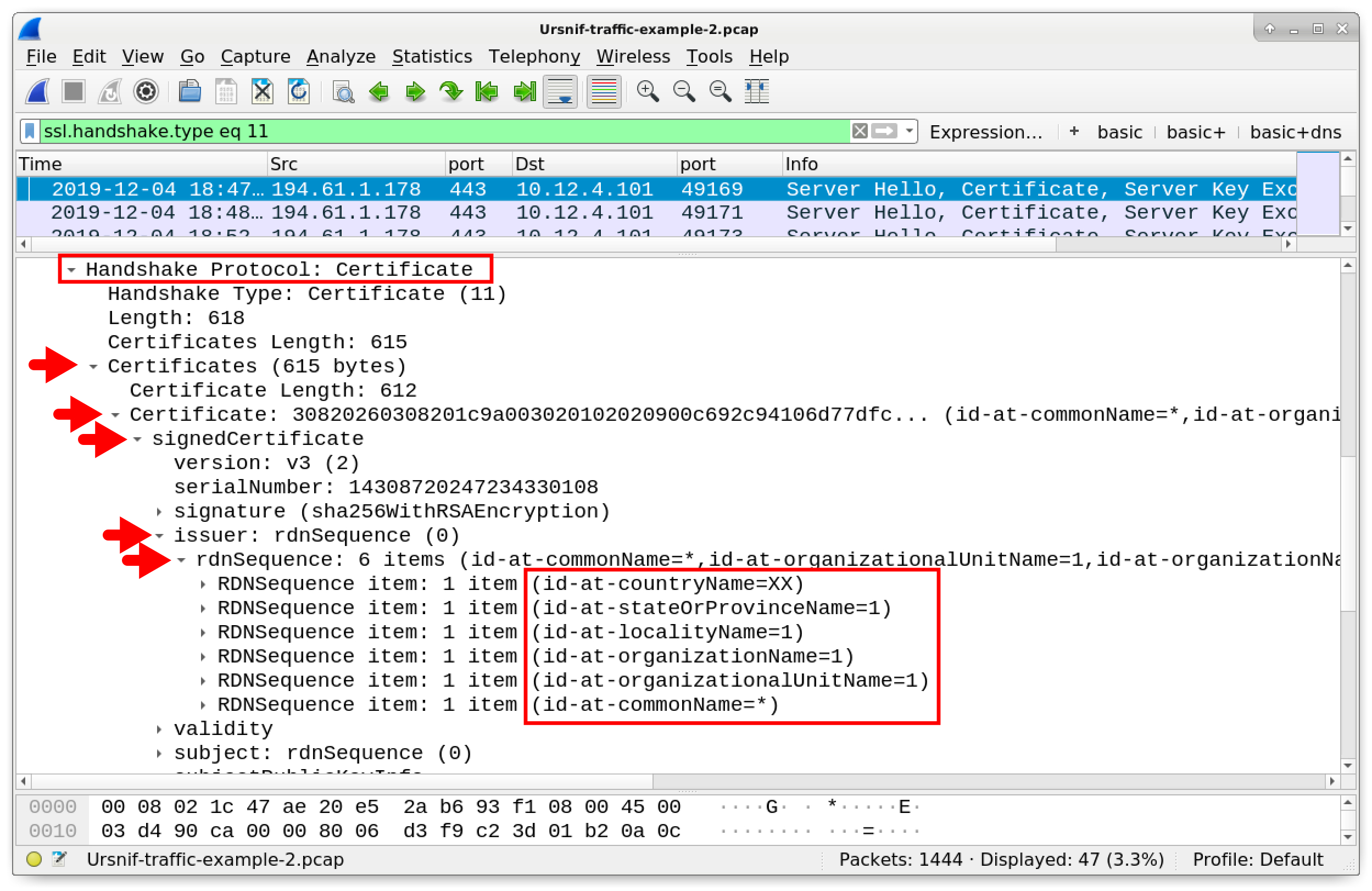
Wireshark Tutorial: Examining Ursnif Infections
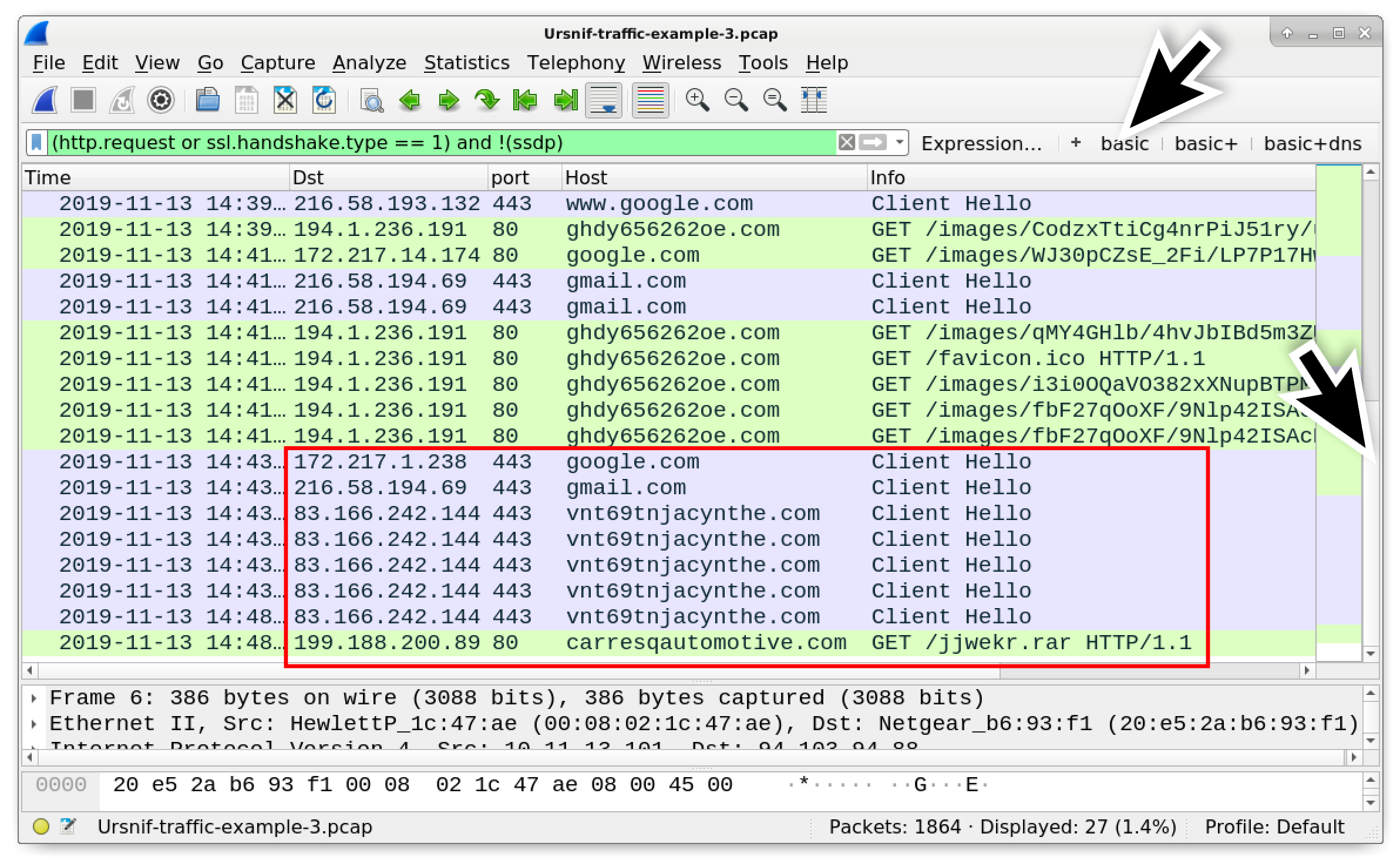
Wireshark Tutorial: Examining Ursnif Infections
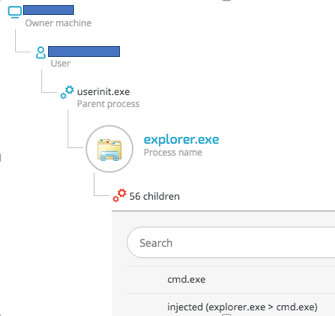
Use behavioral analysis to detect a new Ursnif banking Trojan campaign in Japan

Digital banking fraud: how the Gozi malware works
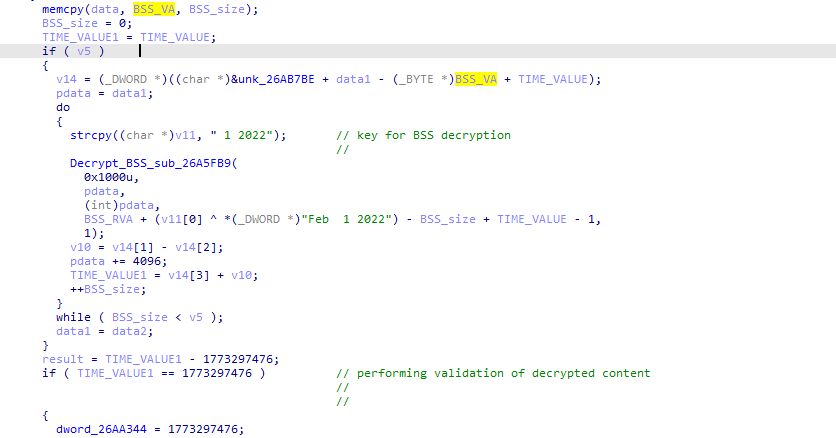
Ursnif Malware Banks on News Events for Phishing Attacks
Unwrapping Ursnifs Gifts - The DFIR Report
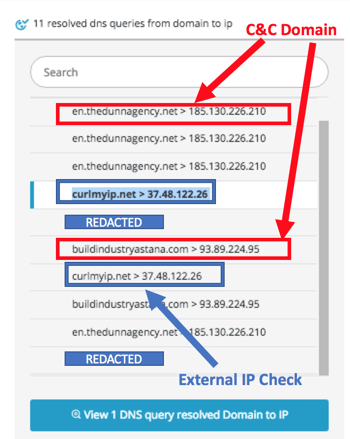
Use behavioral analysis to detect a new Ursnif banking Trojan campaign in Japan
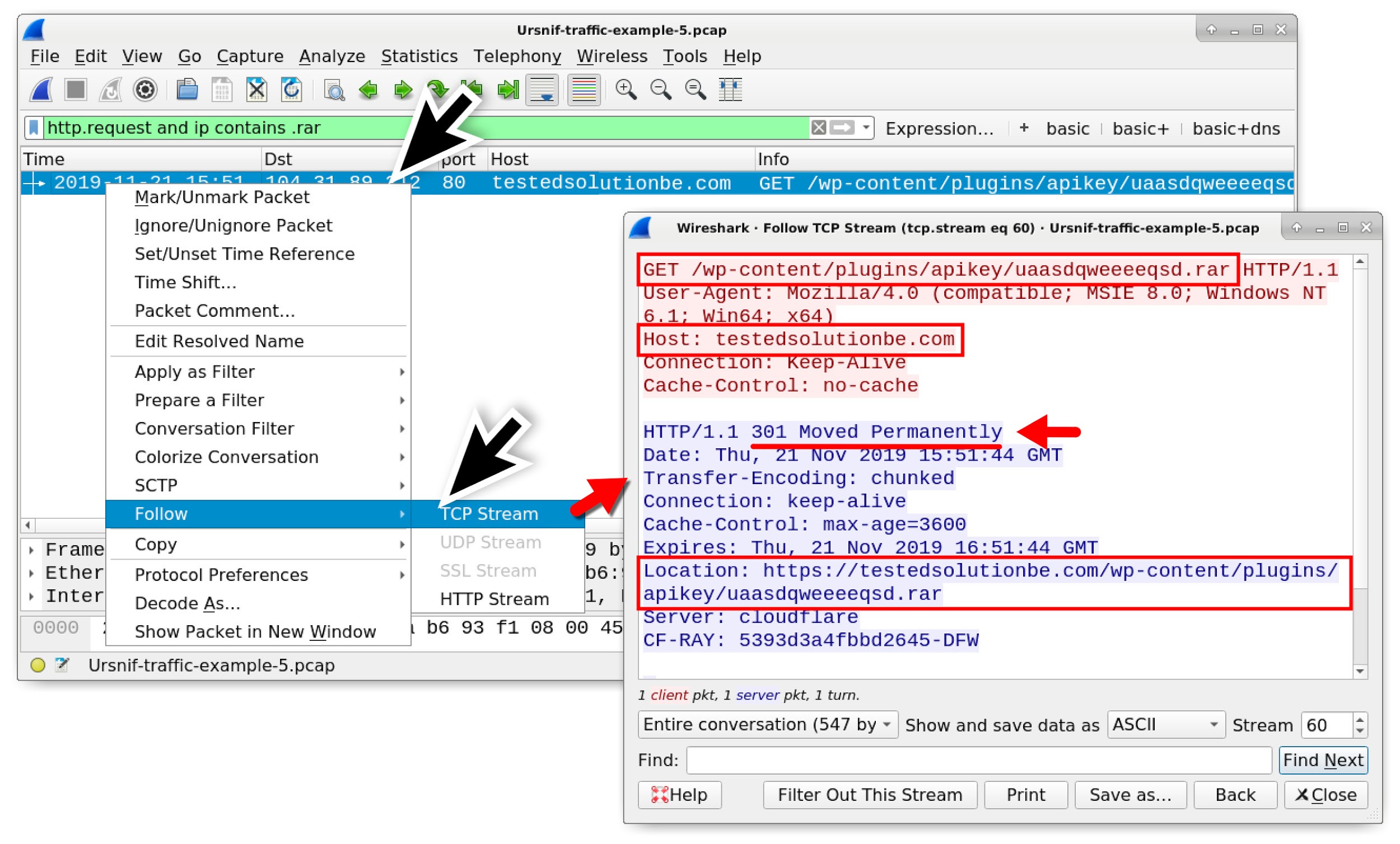
Wireshark Tutorial: Examining Ursnif Infections
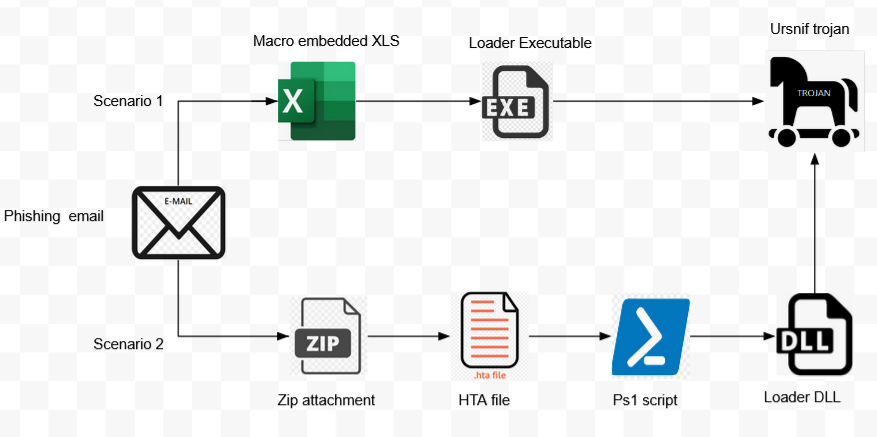
Ursnif Malware Banks on News Events for Phishing Attacks
Gozi: The Malware with a Thousand Faces - Check Point Research
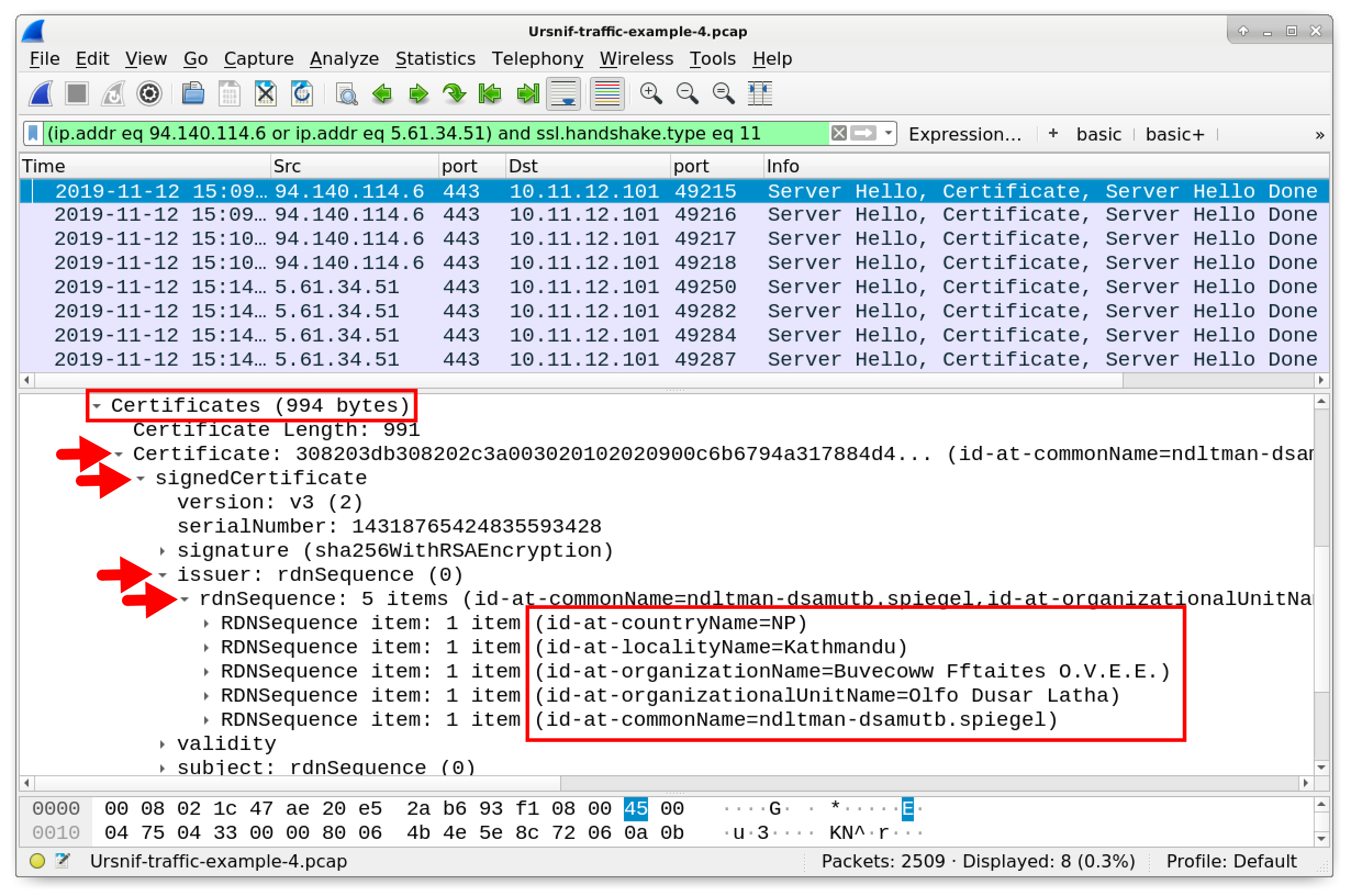
Wireshark Tutorial: Examining Ursnif Infections
Recomendado para você
-
 Evades.io Wiki28 janeiro 2025
Evades.io Wiki28 janeiro 2025 -
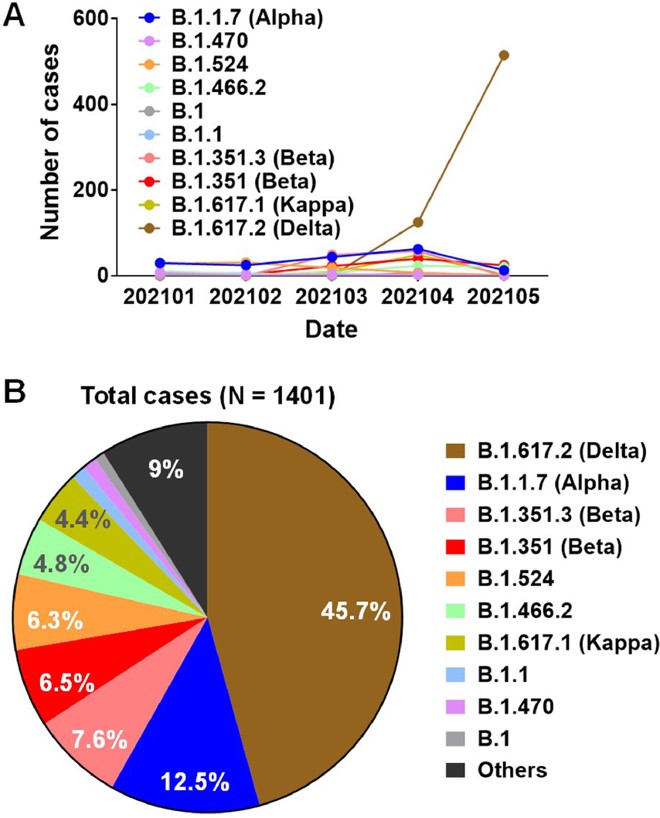 Antibody and CD8+ T Cell Responses: How the Delta Variant Evades Immunity?28 janeiro 2025
Antibody and CD8+ T Cell Responses: How the Delta Variant Evades Immunity?28 janeiro 2025 -
 How to Evade in Star Wars Jedi: Survivor28 janeiro 2025
How to Evade in Star Wars Jedi: Survivor28 janeiro 2025 -
 Kirby evades Morpha's tentacles (by James M) by cvgwjames on DeviantArt28 janeiro 2025
Kirby evades Morpha's tentacles (by James M) by cvgwjames on DeviantArt28 janeiro 2025 -
 Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud28 janeiro 2025
Stream No Sin Evades His Gaze music Listen to songs, albums, playlists for free on SoundCloud28 janeiro 2025 -
 Music Is To Blame: Fox Evades releases her debut EP 'Nothing but Our Dreams28 janeiro 2025
Music Is To Blame: Fox Evades releases her debut EP 'Nothing but Our Dreams28 janeiro 2025 -
 Les Evades Ou Le Chemin Retrouve, Painting by Catherine Villa28 janeiro 2025
Les Evades Ou Le Chemin Retrouve, Painting by Catherine Villa28 janeiro 2025 -
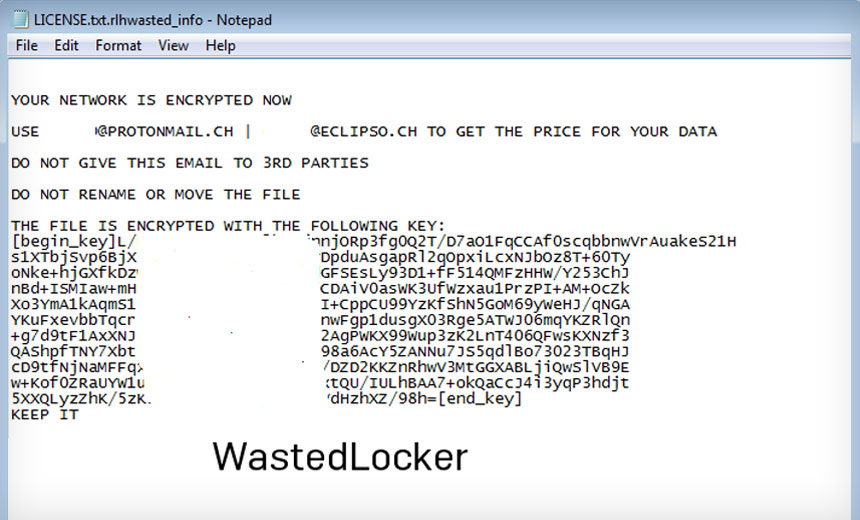 How WastedLocker Evades Anti-Ransomware Tools28 janeiro 2025
How WastedLocker Evades Anti-Ransomware Tools28 janeiro 2025 -
 Comikey Launches Hakusensha Series, “Disguised as a Butler, the Former Princess Evades the Prince's Love!”28 janeiro 2025
Comikey Launches Hakusensha Series, “Disguised as a Butler, the Former Princess Evades the Prince's Love!”28 janeiro 2025 -
Loose emu evades capture in Lakevillev_1N5nqFiRwB28 janeiro 2025
você pode gostar
-
 Sad Bart Simpson edits (1 hour) (for kids) : r/dankmemes28 janeiro 2025
Sad Bart Simpson edits (1 hour) (for kids) : r/dankmemes28 janeiro 2025 -
 Jogo Pure Pool - Ps428 janeiro 2025
Jogo Pure Pool - Ps428 janeiro 2025 -
 Óculos Oakley Juliet Penny Gold 24k Lente Vermelha ⋆ Sanfer Acessórios28 janeiro 2025
Óculos Oakley Juliet Penny Gold 24k Lente Vermelha ⋆ Sanfer Acessórios28 janeiro 2025 -
 Hametsu no Oukoku Episode 2 English SUB28 janeiro 2025
Hametsu no Oukoku Episode 2 English SUB28 janeiro 2025 -
VALORANT - Como começou // Como está indo Mande aqui seu progresso28 janeiro 2025
-
 Link Nonton Kuro no Shoukanshi Episode 2 Sub Indo Bukan Anoboy dan Samehadaku, Streaming di Sini - Kilas Berita28 janeiro 2025
Link Nonton Kuro no Shoukanshi Episode 2 Sub Indo Bukan Anoboy dan Samehadaku, Streaming di Sini - Kilas Berita28 janeiro 2025 -
 Ultimate Fighting Championship: Throwdown - Metacritic28 janeiro 2025
Ultimate Fighting Championship: Throwdown - Metacritic28 janeiro 2025 -
 Tails Doll screenshots, images and pictures - Comic Vine28 janeiro 2025
Tails Doll screenshots, images and pictures - Comic Vine28 janeiro 2025 -
 Fotos de Solidão, Imagens de Solidão sem royalties28 janeiro 2025
Fotos de Solidão, Imagens de Solidão sem royalties28 janeiro 2025 -
 COMO DESENHAR PIJAMA E ACESSÓRIOS DE DORMIR PARA PAPER DUCK28 janeiro 2025
COMO DESENHAR PIJAMA E ACESSÓRIOS DE DORMIR PARA PAPER DUCK28 janeiro 2025

