Blocking Coin Miners' in ICT Security Tools
Por um escritor misterioso
Last updated 02 março 2025

A collection of best ICT Security Tools + tutorials how to use them filtered by Blocking Coin Miners

Beijing banned crypto mining, so China miners went underground
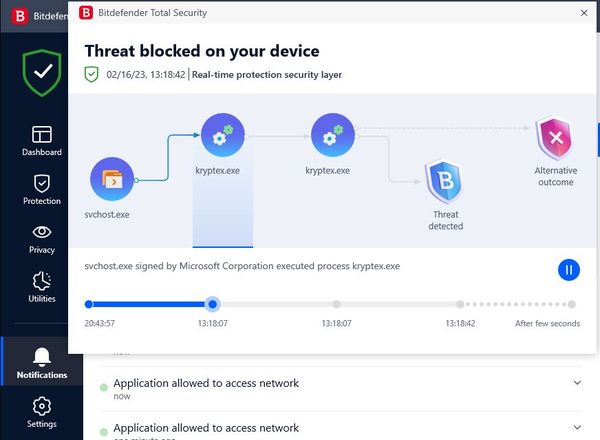
Why Security Software Detects Coin Miners as Potentially Unwanted Applications

Can you use a used server to mine crypto? - We Buy Used IT Equipment

Security 101: The Impact of Cryptocurrency-Mining Malware - Nachrichten zum Thema Sicherheit - Trend Micro DE
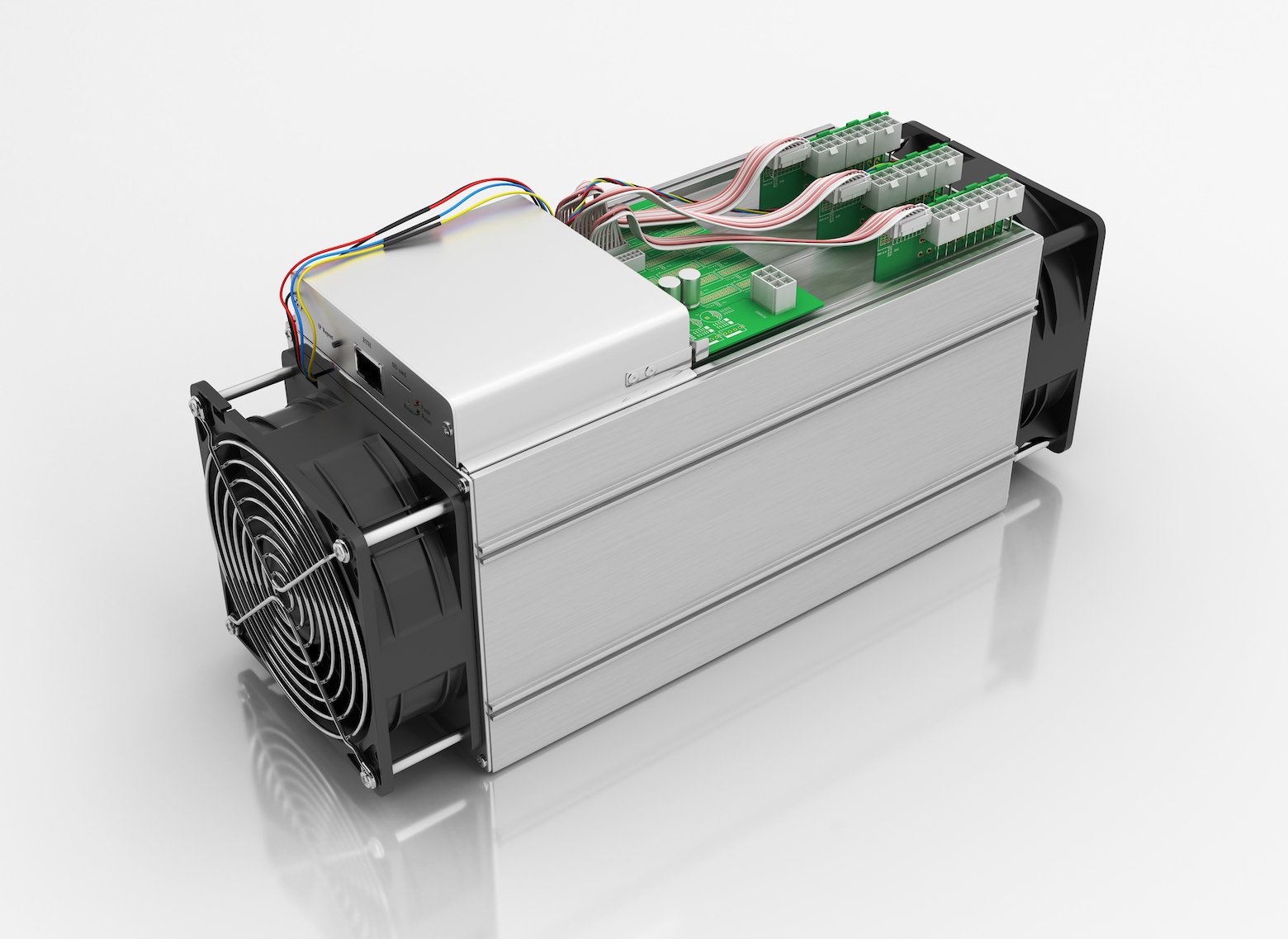
How Does Bitcoin Mining Work? A Guide for Business
Blockchain Security: Everything You Need to Know

Cryptojacking explained: How to prevent, detect, and recover from it
Crypto foes gird to stop mines from 'spreading like cancer' - E&E News by POLITICO

Real-world Cyber Attacks Targeting Data Science Tools

How Does Bitcoin Mining Work? A Guide for Business

Bitcoin mining difficulty drops after hashrate collapse in China
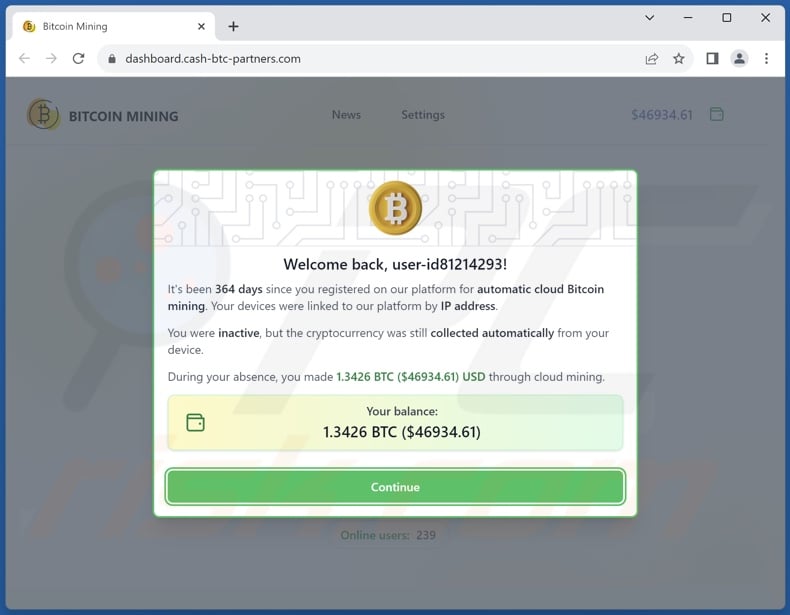
Bitcoin Mining Scam - Removal and recovery steps (updated)

Defending against cryptojacking with Microsoft Defender for Endpoint and Intel TDT
Recomendado para você
-
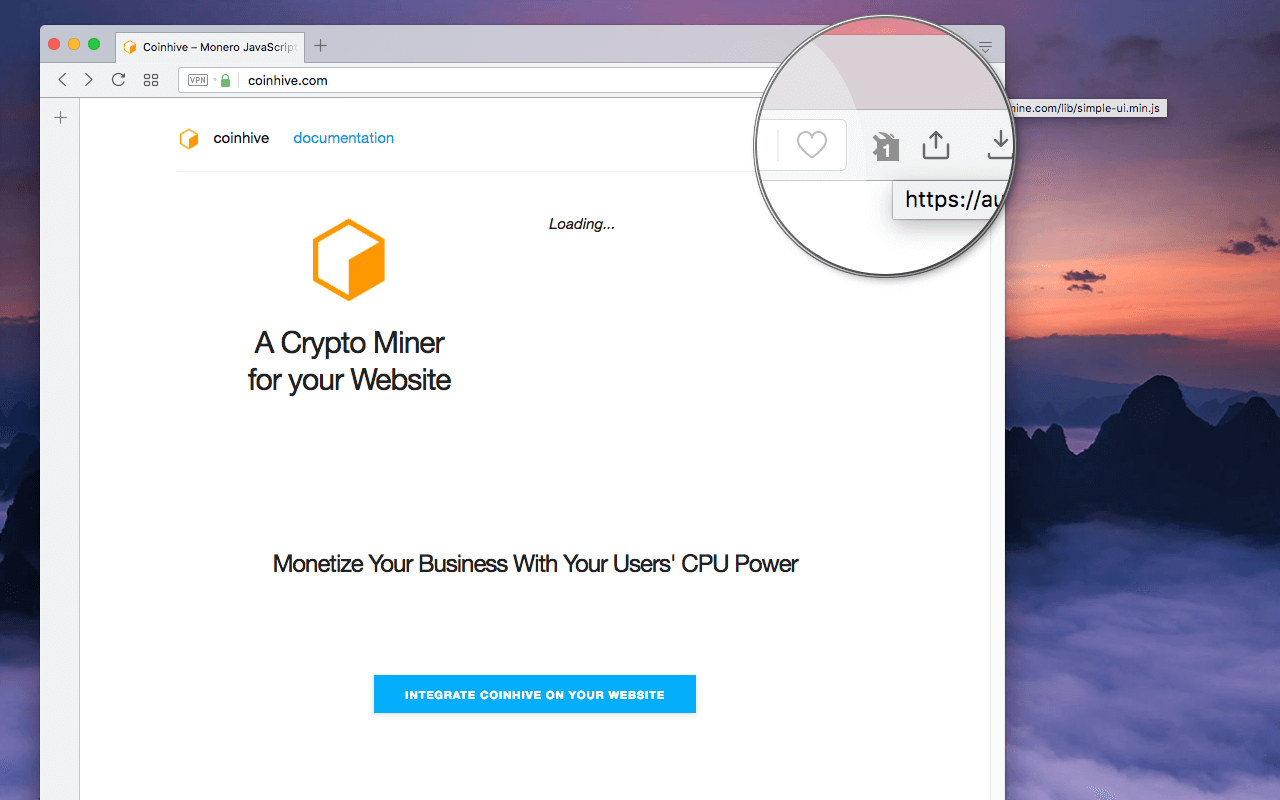 Coin Mining Blocker02 março 2025
Coin Mining Blocker02 março 2025 -
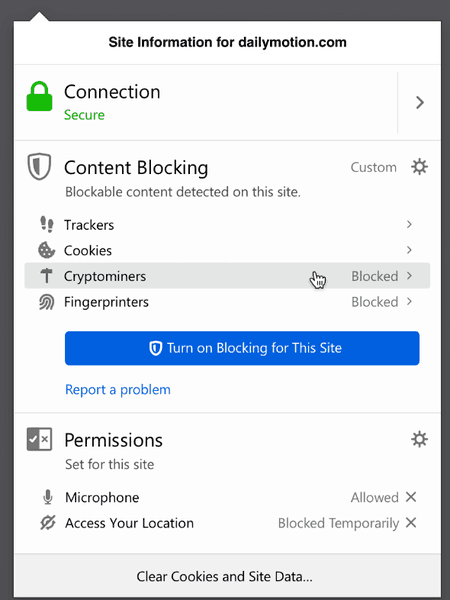 Firefox 67: Cryptocurrency miners and Fingerprinters protection02 março 2025
Firefox 67: Cryptocurrency miners and Fingerprinters protection02 março 2025 -
Cryptojacking of processing power: what is it and how to protect yourself? » IRIS-BH02 março 2025
-
 The Best Ad Blockers for Chrome02 março 2025
The Best Ad Blockers for Chrome02 março 2025 -
 Google might block embedded cryptocurrency mining with new Chrome feature02 março 2025
Google might block embedded cryptocurrency mining with new Chrome feature02 março 2025 -
![8 BEST Ad Blockers For Chrome In 2023 [Free Pop Up Blockers]](https://www.softwaretestinghelp.com/wp-content/qa/uploads/2020/02/AdBlockers.png) 8 BEST Ad Blockers For Chrome In 2023 [Free Pop Up Blockers]02 março 2025
8 BEST Ad Blockers For Chrome In 2023 [Free Pop Up Blockers]02 março 2025 -
 Chrome Solutions – Impact Investment Group02 março 2025
Chrome Solutions – Impact Investment Group02 março 2025 -
) Chrome to soon block notifications from abusive, disruptive websites02 março 2025
Chrome to soon block notifications from abusive, disruptive websites02 março 2025 -
 Web Mining, Part Two: Adblock Plus Now Blocks Web Mining Efforts a la TPB02 março 2025
Web Mining, Part Two: Adblock Plus Now Blocks Web Mining Efforts a la TPB02 março 2025 -
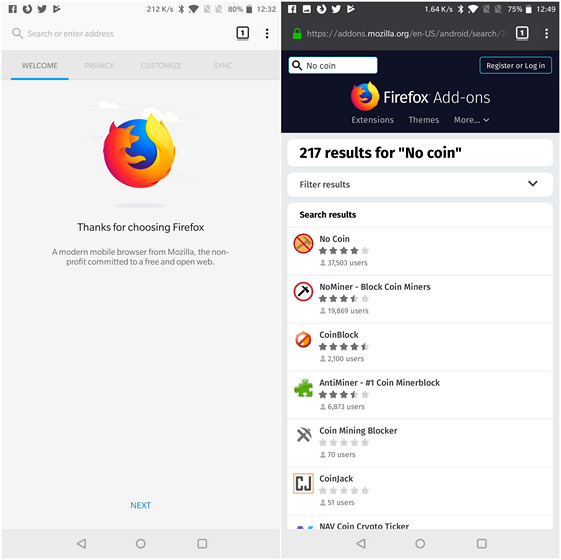 How to Stop Websites from Mining Cryptocurrencies on Smartphone or PC02 março 2025
How to Stop Websites from Mining Cryptocurrencies on Smartphone or PC02 março 2025
você pode gostar
-
Camponesa Sonhadora - - Camponesa Sonhadora - Ravenna02 março 2025
-
 Baka Mitai GIF - Baka Mitai - Discover & Share GIFs02 março 2025
Baka Mitai GIF - Baka Mitai - Discover & Share GIFs02 março 2025 -
 Otherside, Otherside Picnic Wiki02 março 2025
Otherside, Otherside Picnic Wiki02 março 2025 -
 20+ Sonic the Hedgehog HD Wallpapers and Backgrounds02 março 2025
20+ Sonic the Hedgehog HD Wallpapers and Backgrounds02 março 2025 -
 Retiro Jovens - Região 955 em Curitiba - Sympla02 março 2025
Retiro Jovens - Região 955 em Curitiba - Sympla02 março 2025 -
 Cara assustadora de halloween tamanho grande de sorriso emoji amarelo02 março 2025
Cara assustadora de halloween tamanho grande de sorriso emoji amarelo02 março 2025 -
 An Overview of Networking Infrastructure for Massively Multiplayer Online Games02 março 2025
An Overview of Networking Infrastructure for Massively Multiplayer Online Games02 março 2025 -
 Filme de Your Lie in April a caminho?02 março 2025
Filme de Your Lie in April a caminho?02 março 2025 -
 Son Goku/História Oficial, Dragon Ball Wiki02 março 2025
Son Goku/História Oficial, Dragon Ball Wiki02 março 2025 -
 Do You Think Kratos with the Boots of Hermes Instead of the Draupnir Spear Could Take Down Heimdall? : r/GodofWar02 março 2025
Do You Think Kratos with the Boots of Hermes Instead of the Draupnir Spear Could Take Down Heimdall? : r/GodofWar02 março 2025
