Abusing Exceptions for Code Execution, Part 1
Por um escritor misterioso
Last updated 27 janeiro 2025

A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.
A common offensive technique used by operators and malware developers alike has been to execute malicious code at runtime to avoid static detection. Often, methods of achieving runtime execution have focused on placing arbitrary code into executable memory that can then be executed. In this article, we will explore a new approach to executing runtime code that does not rely on finding executable regions of memory, but instead relies on abusing existing trusted memory to execute arbitrary code.

Why the C Programming Language Still Runs the World

Hunting for Suspicious Windows Libraries for Execution and Defense Evasion — Elastic Security Labs

Detecting anomalous Vectored Exception Handlers on Windows, NCC Group Research Blog

Patching Perforce perforations: Critical RCE vulnerability discovered in Perforce Helix Core Server
Cloud DNS Security - How to protect DNS in the Cloud – Sysdig
10 Common Web Security Vulnerabilities

Remote Code Execution (RCE), Code Injection, Learn AppSec
We believe urinary health should be proactive, but life happens. That’s why we created the UTI Emergency Kit. , This 3-in-1 bundle contains everything

UTI Emergency Kit

The UTI Emergency Kit
Recomendado para você
-
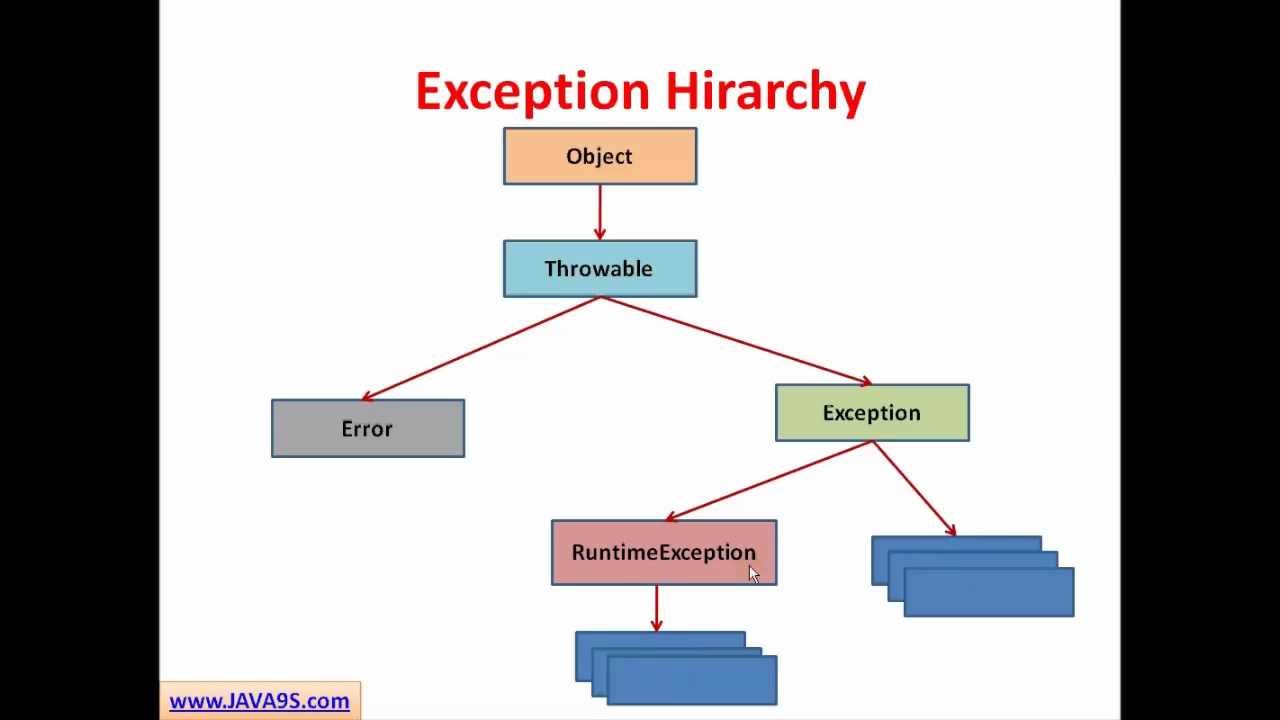 Java Tutorial # 14 Exception Handling in Java - Checked and Unchecked Exceptions27 janeiro 2025
Java Tutorial # 14 Exception Handling in Java - Checked and Unchecked Exceptions27 janeiro 2025 -
 Python Exceptions: The Ultimate Beginner's Guide (with Examples)27 janeiro 2025
Python Exceptions: The Ultimate Beginner's Guide (with Examples)27 janeiro 2025 -
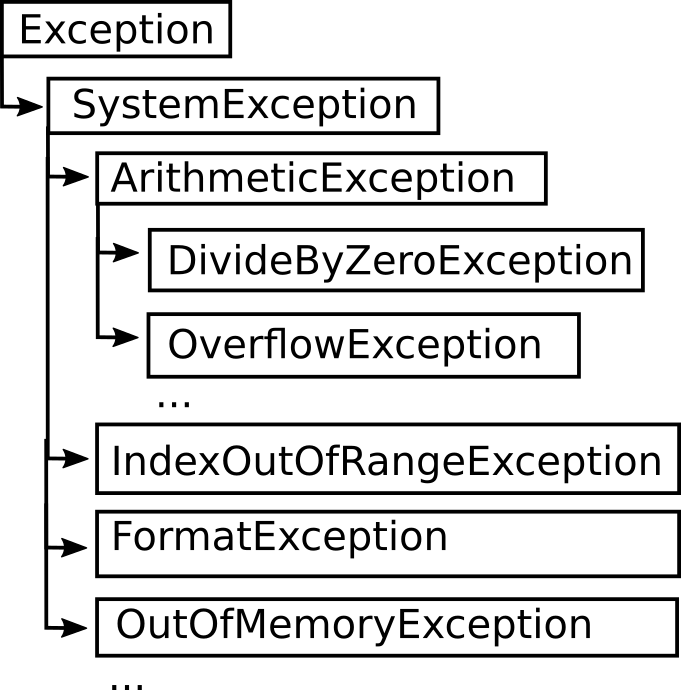 Reading 5, Part 2: Exceptions27 janeiro 2025
Reading 5, Part 2: Exceptions27 janeiro 2025 -
 Exceptions in Java - GeeksforGeeks27 janeiro 2025
Exceptions in Java - GeeksforGeeks27 janeiro 2025 -
 Java Exceptions and How to Log Them Securely27 janeiro 2025
Java Exceptions and How to Log Them Securely27 janeiro 2025 -
 Java Exception Rule Book – Nico de Wet scalable and robust distributed systems27 janeiro 2025
Java Exception Rule Book – Nico de Wet scalable and robust distributed systems27 janeiro 2025 -
 Selenium WebDriver: Handling Exceptions, Blog27 janeiro 2025
Selenium WebDriver: Handling Exceptions, Blog27 janeiro 2025 -
 No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime27 janeiro 2025
No Exceptions Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime27 janeiro 2025 -
 Handling Exceptions27 janeiro 2025
Handling Exceptions27 janeiro 2025 -
 What Is an Exception? (The Java™ Tutorials > Essential Java Classes > Exceptions)27 janeiro 2025
What Is an Exception? (The Java™ Tutorials > Essential Java Classes > Exceptions)27 janeiro 2025
você pode gostar
-
/cloudfront-eu-central-1.images.arcpublishing.com/diarioas/XXNXUDPFFJEPRHQUB6ZOLXAT3Q.jpg) Luis Suárez close to Nacional return - AS USA27 janeiro 2025
Luis Suárez close to Nacional return - AS USA27 janeiro 2025 -
 Plants vs. Zombies Online/Concepts, Plants vs. Zombies Wiki27 janeiro 2025
Plants vs. Zombies Online/Concepts, Plants vs. Zombies Wiki27 janeiro 2025 -
 The Deer King Review: Reminiscent of Ghibli, But Far From Its Equal27 janeiro 2025
The Deer King Review: Reminiscent of Ghibli, But Far From Its Equal27 janeiro 2025 -
 Ruy López Opening: Morphy Defense, Exchange, Alapin Gambit, 1-027 janeiro 2025
Ruy López Opening: Morphy Defense, Exchange, Alapin Gambit, 1-027 janeiro 2025 -
 Boneco Majin Buu Dragon Ball Z Bandai Grande 44cm Novo Promo27 janeiro 2025
Boneco Majin Buu Dragon Ball Z Bandai Grande 44cm Novo Promo27 janeiro 2025 -
 PDF) Metaverso. Novas possibilidades e desafios para a Igreja27 janeiro 2025
PDF) Metaverso. Novas possibilidades e desafios para a Igreja27 janeiro 2025 -
 Teclado Piano Musical Bebê Brinquedo Infantil Divertido Som Pinguim - Catálogo GrupoShopMix27 janeiro 2025
Teclado Piano Musical Bebê Brinquedo Infantil Divertido Som Pinguim - Catálogo GrupoShopMix27 janeiro 2025 -
 Portuguese – PT-PT Voices for characters – FighterZ Mods27 janeiro 2025
Portuguese – PT-PT Voices for characters – FighterZ Mods27 janeiro 2025 -
Cheetos Crunchy Cheese Flavored Snacks, 1.375 oz, Joe V's Smart Shop27 janeiro 2025
-
MyAnimeList.net - The main female characters of Enen no27 janeiro 2025

